What is Azure Container Instances?
Microsoft Azure provides many services, and Azure Container Instances (ACI) is one of them. This service helps to run and manage containers and applications without managing the virtual machines. Using ACI, containers can get started within a few seconds without deploying or managing virtual machines. For deploying images, we can use the provided images (Linux and Windows from Docker Hub), the Azure container registry, or another image registry. We can specify the CPU and memory required as per the use. This service uses a Pay-as-you-go pricing model.
Sign in to Azure
- Access the Azure portal by signing in with your credentials.
- If you’re new to Azure, sign up for a free account before proceeding with the steps.
Create a container instance | Step-By-Step Tutorial
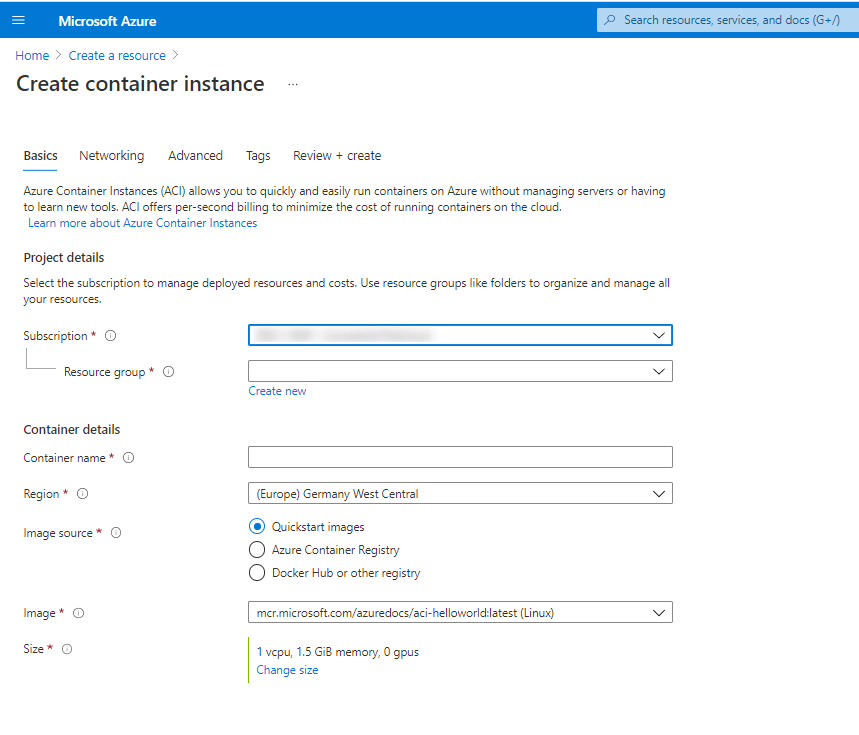
Step 1: Begin by logging in to your Azure portal. Then, navigate to the “Create Resource” option to initiate the resource creation process professionally.
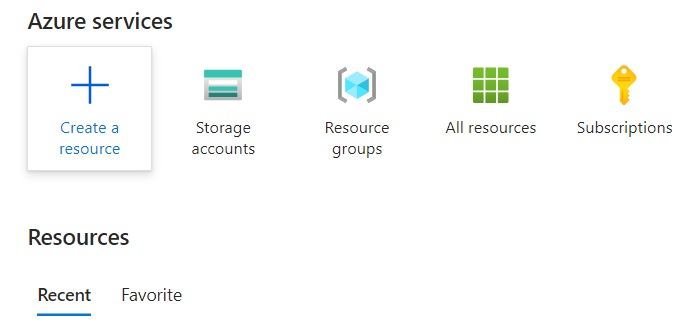 Step 2: Next, from the left panel, select “Container” and then choose “Container Instance” to proceed with the deployment professionally..
Step 2: Next, from the left panel, select “Container” and then choose “Container Instance” to proceed with the deployment professionally..
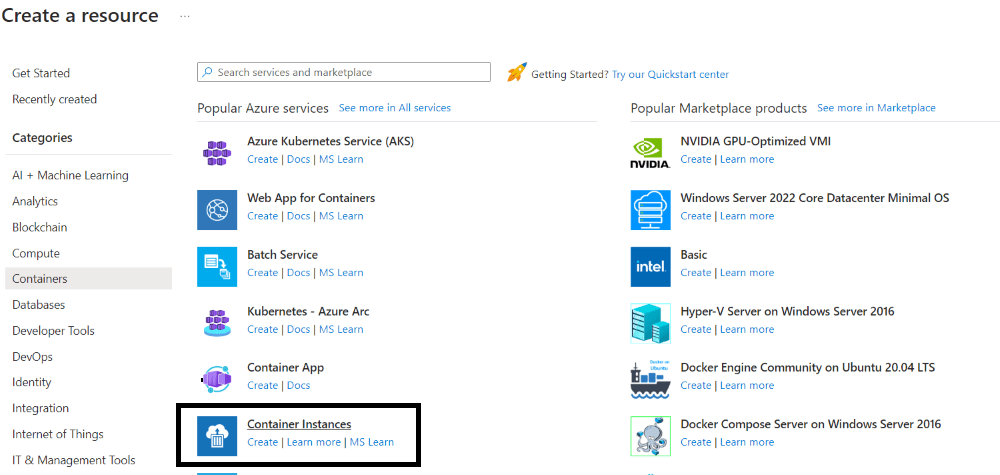
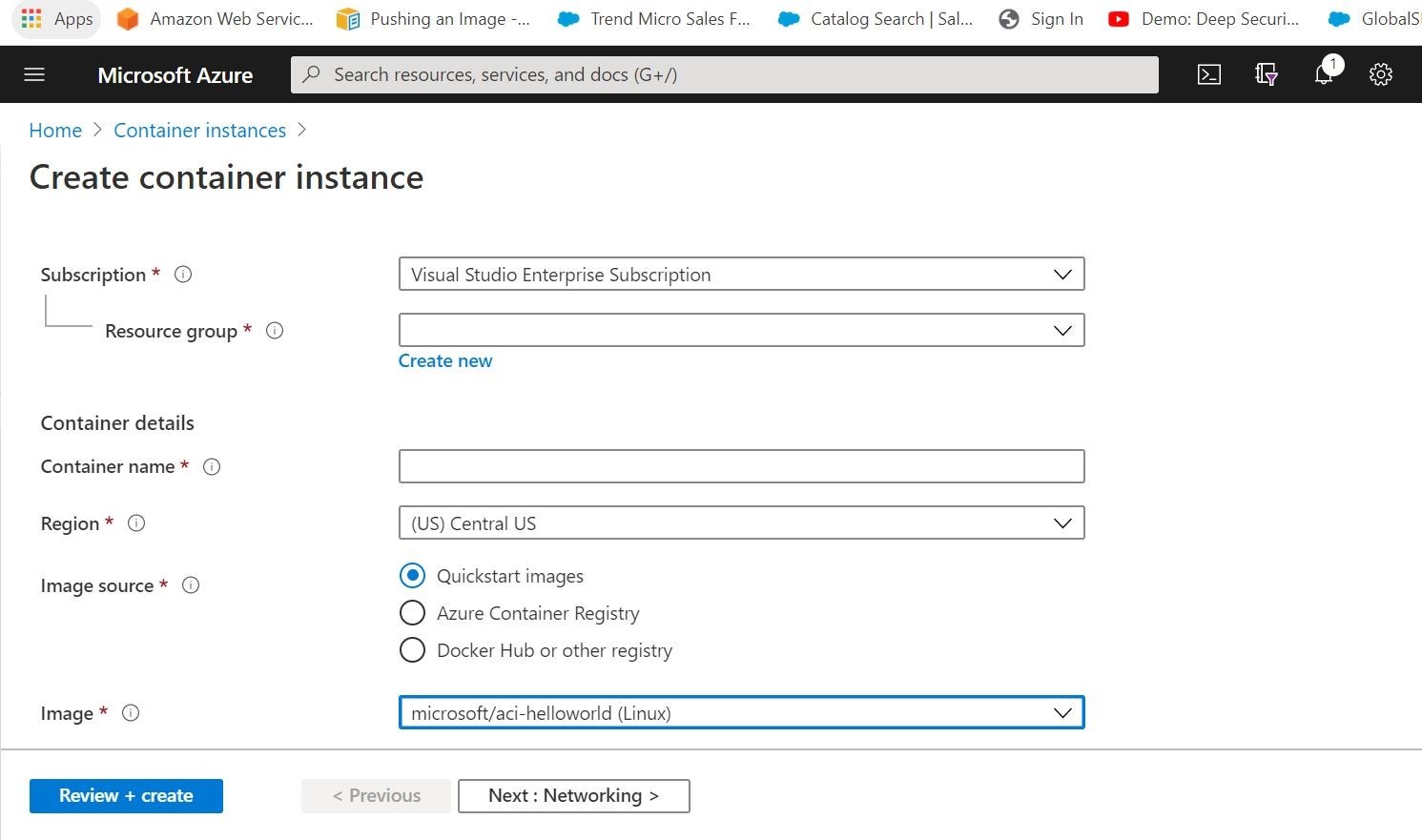
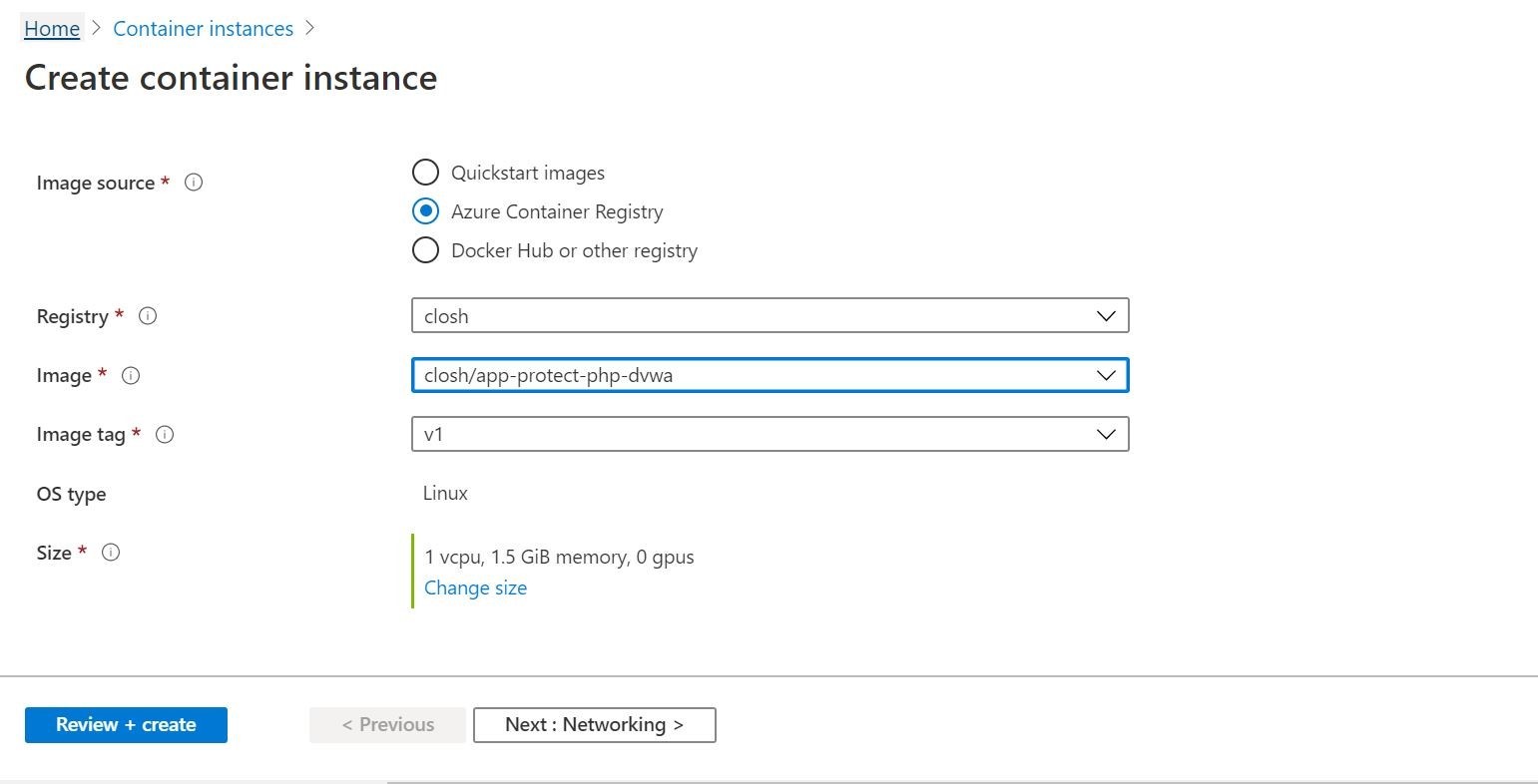
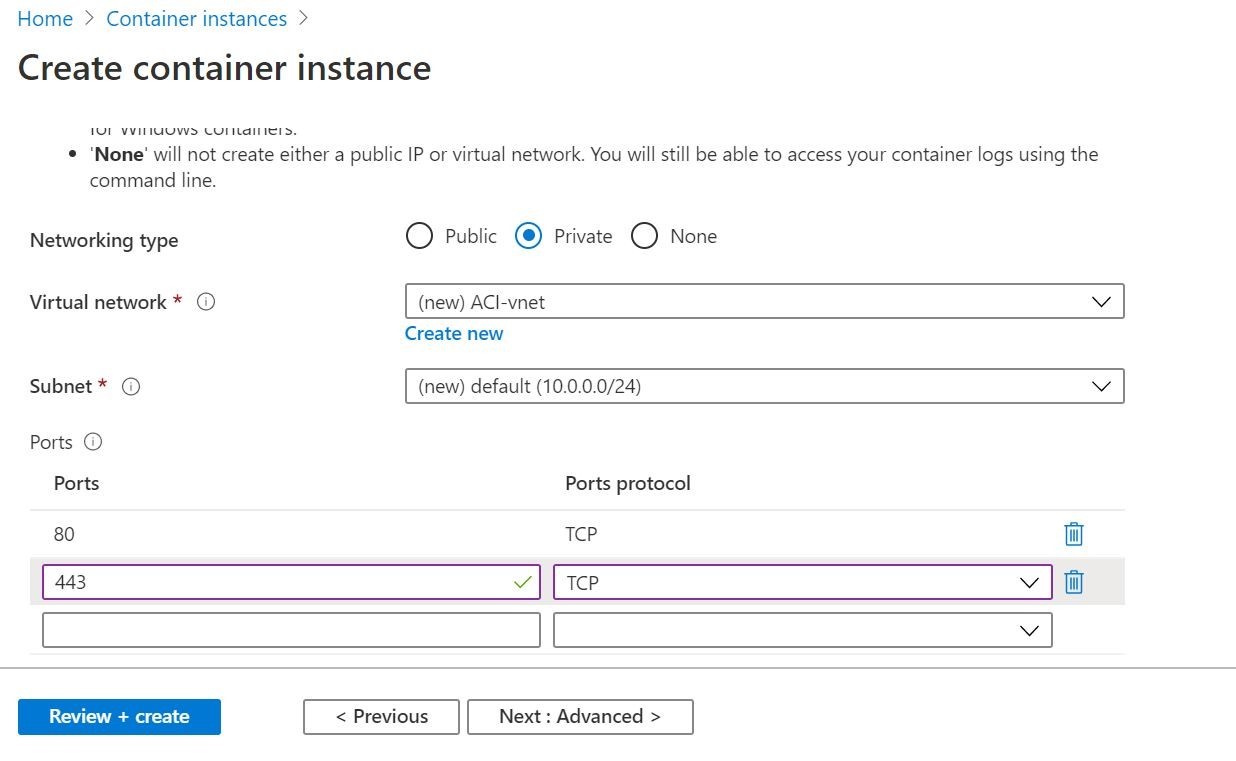
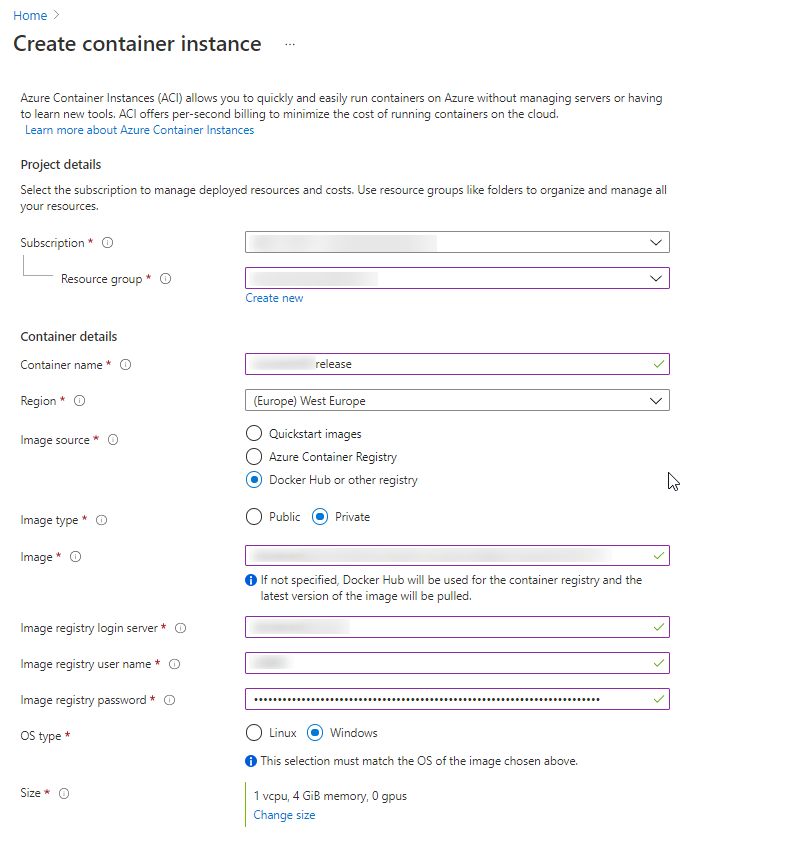
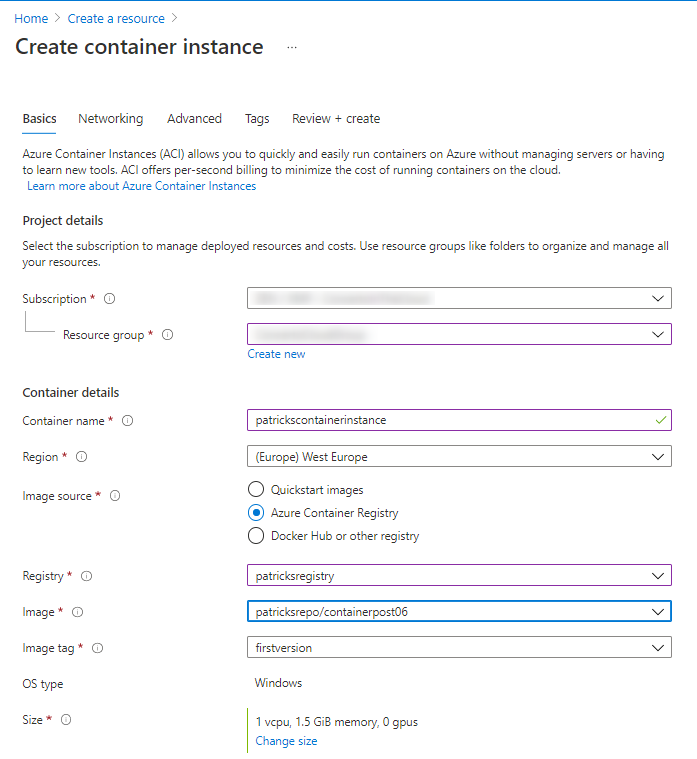
Step 3: Proceed by filling out the template with details such as your Subscription, Resource Group, and a Name for the instance. Select an image from Quickstart images or other repositories like Azure Container Registry. Choose the appropriate OS (Linux or Windows) and specify the desired size in terms of vCPU and memory. Then, navigate to the Networking section to continue with the configuration professionally.
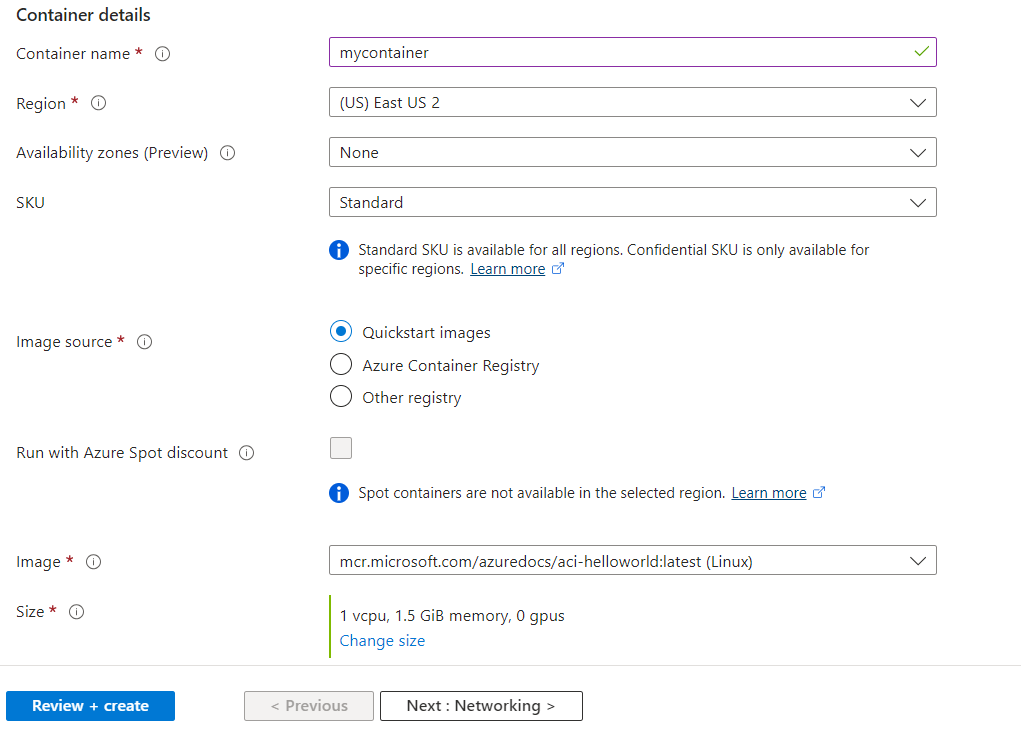
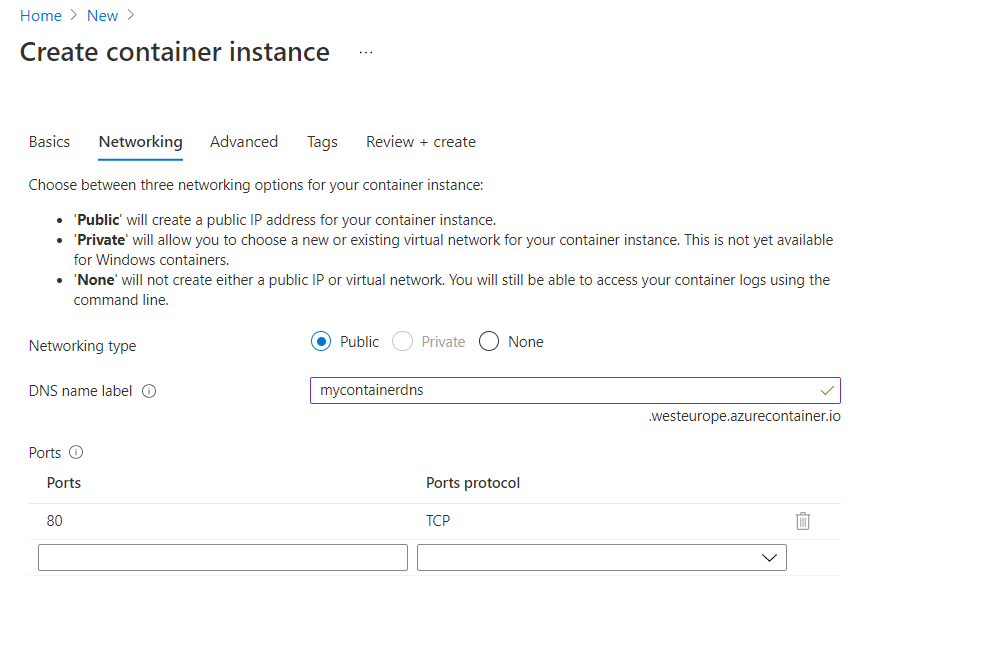
In the Networking section, select between Public or Private accessibility options. For demonstration purposes, we’ve chosen the public option. Assign a DNS name label and specify its Scope, in this case, we’ve set it as “Tenant.” The DNS name label, combined with auto-generated hashed values, forms a fully qualified domain name for accessibility. Proceed to the next step after configuring these settings professionally.
In this scenario, you’re responsible for configuring your own Virtual Network to ensure the private connectivity of your Container Instance within your network environment. This entails setting up the necessary subnets, network security groups, and other networking components to enable communication between your resources securely.
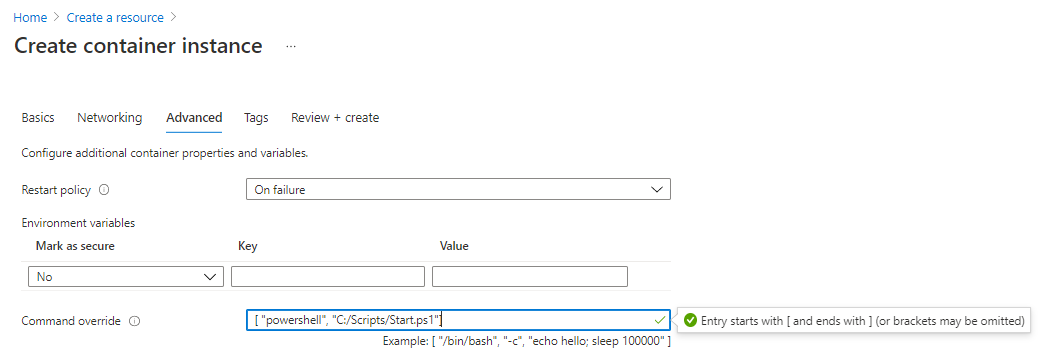
For advanced configurations, you can specify the Restart Policy according to your specific requirements. In this case, the “On failure” option has been selected, ensuring that the container automatically restarts only in the event of a failure, optimizing availability and reliability.
Please do not make any changes to the setups; leave them all as they are.
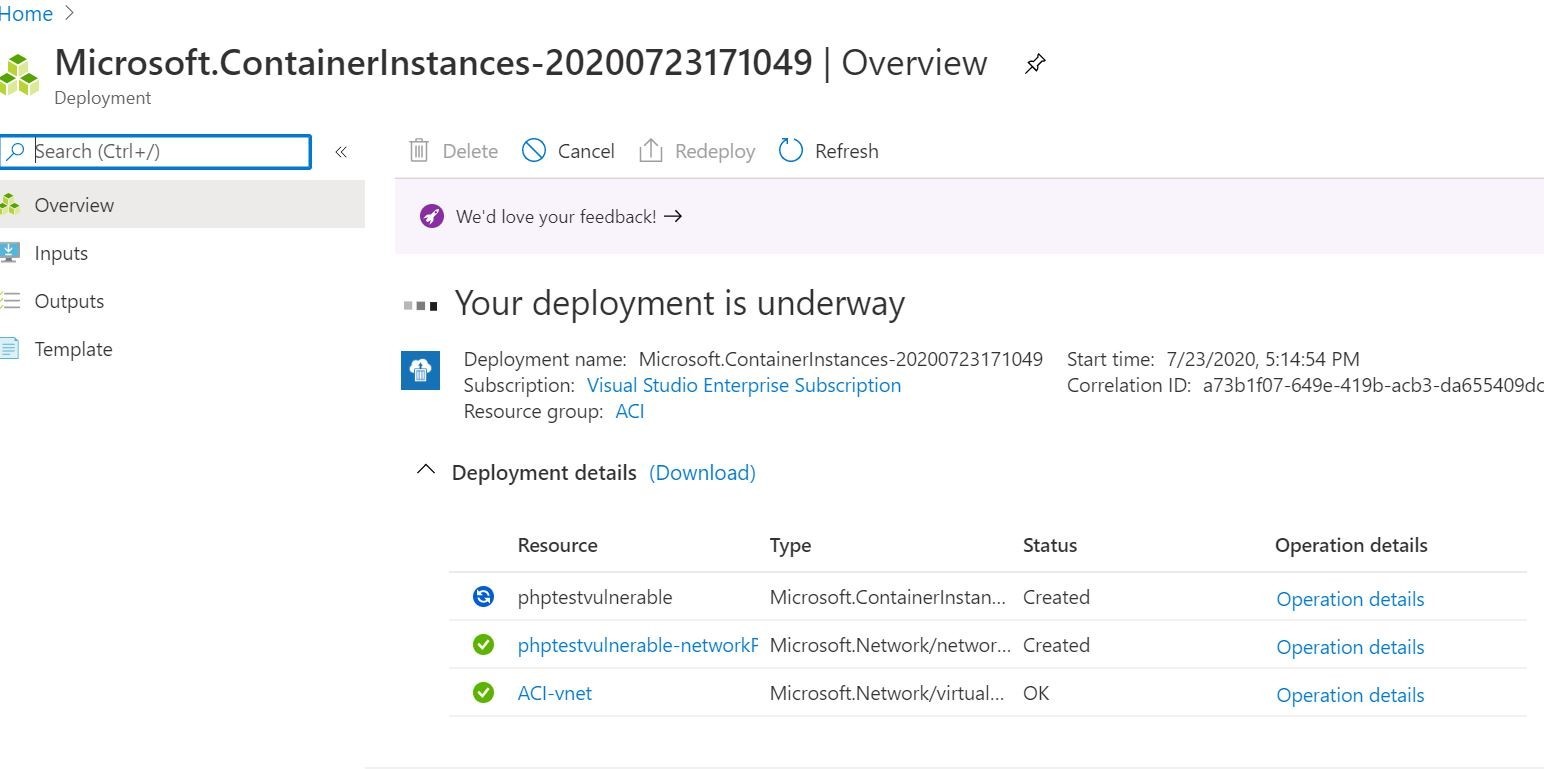
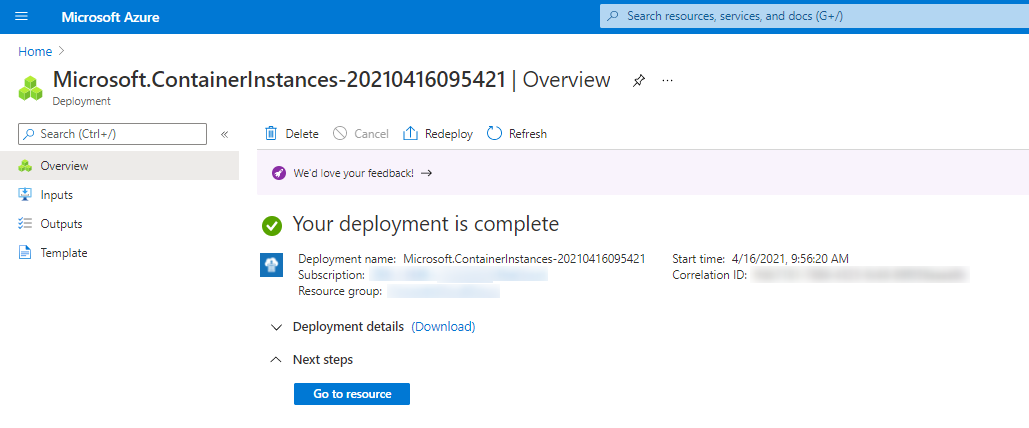
Step 4: After reviewing your settings, proceed to click on “Review + Create” and then select “Create” to initiate the deployment process.
Step 5: Navigate to “Container” and select your container from the overview. Then, click on the Fully Qualified Domain Name (FQDN) link to access your deployed container.
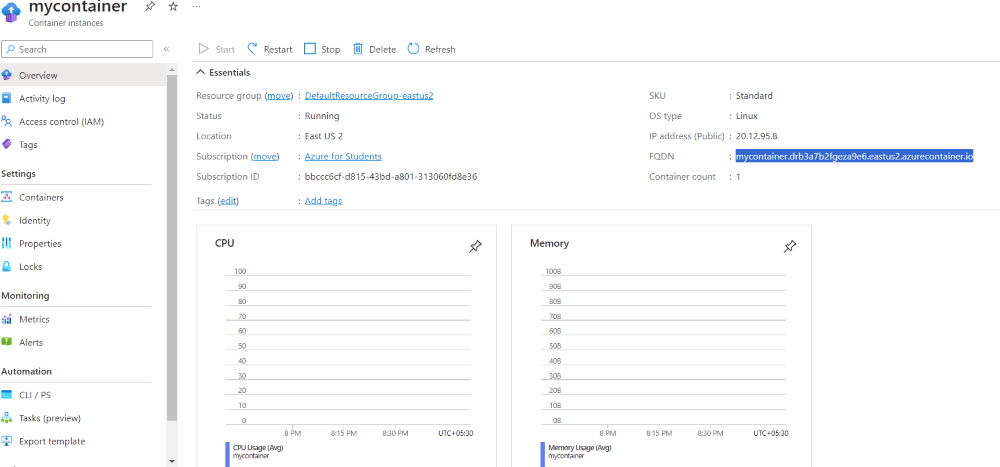
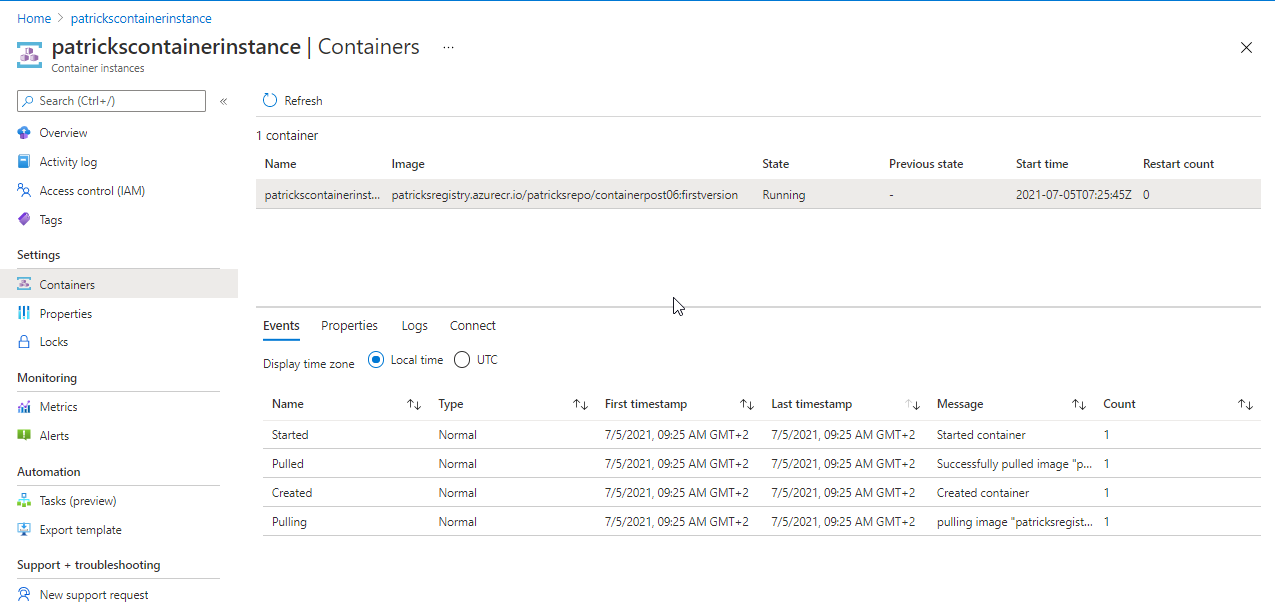
Upon accessing the web page, you can view the details and status of your container instance, allowing you to manage and monitor its performance effectively.

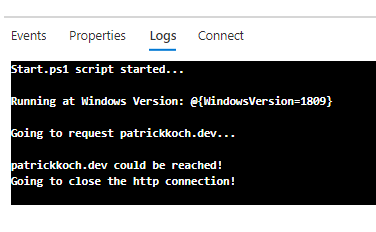
View container logs
Examining the logs of a container instance proves invaluable for diagnosing potential issues with either the container itself or the application it hosts.
- Navigate to the Settings section of your container instance configuration.
- Select Containers and then Logs from the menu options.
- Review the displayed logs to observe the HTTP GET request that was generated when accessing the application through your browser.
Clean up resources
To ensure proper cleanup and resource management, it’s important to delete container instances that are no longer needed. This helps free up resources and avoid unnecessary costs associated with running idle or unused instances.
- Navigate to the Overview tab of the “mycontainer” container instance.
- Click on the Delete button to remove the container instance.
Deploying Containers with Azure Container Instances: Real-World Use Cases
- Web Applications: Host web applications in containers on ACI for easy deployment and scalability.
- Microservices Architecture: Deploy microservices as individual containers on ACI to achieve better isolation and scalability.
- CI/CD Pipelines: Use ACI to run containerized CI/CD pipelines, allowing for quick and efficient testing and deployment of applications.
- Batch Processing: Run batch processing tasks in containers on ACI to handle periodic or one-time compute-intensive workloads.
- Dev/Test Environments: Provision temporary development or testing environments by deploying containers on ACI, reducing setup time and resource usage.
Steps To Deploy a Container to Azure Container Instances Using Azure CLI
Follown the steps mentioned below to Deploy a Container to Azure Container Instances Using Azure CLI.
Prerequisites
- Use the Bash environment in Azure Cloud Shell.
- For installing azure cli on local refer following link to access the resoures using the azure-cli.
Step 1: Create a resource group
Container instances must be deployed into a resource group in a manner similar to other Azure resources. Resource groups can be used to manage and arrange related Azure resources.
az group create --name myResourceGroup --location eastusStep 2: Create A Container
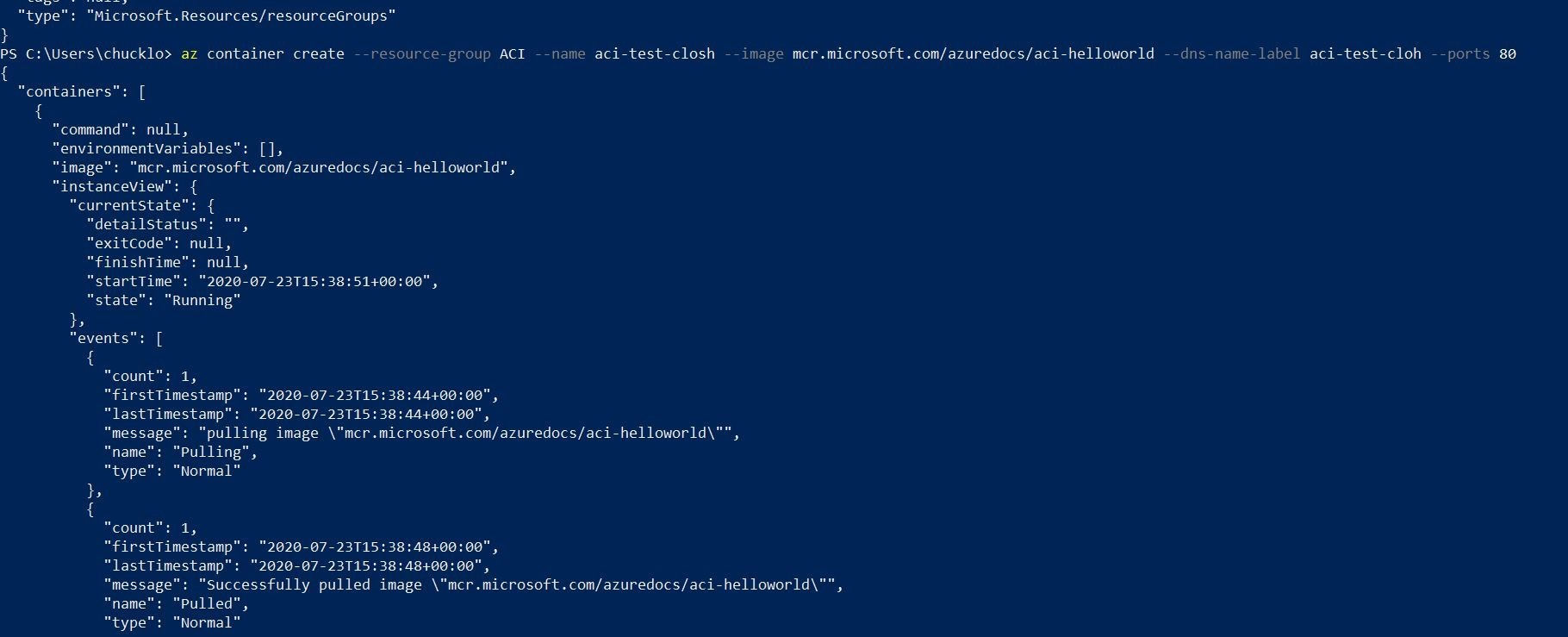
Using the Azure CLI command az container create, a container instance must be created in this stage. Using the Docker image “mcr.microsoft.com/azuredocs/aci-helloworld,” this command establishes a container with the name “mycontainer” in the designated Azure resource group (“myResourceGroup”). It also gives the container the DNS name label “aci-demo” and opens port 80 to network traffic.
az container create --resource-group myResourceGroup --name mycontainer
--image mcr.microsoft.com/azuredocs/aci-helloworld --dns-name-label aci-demo --ports 80
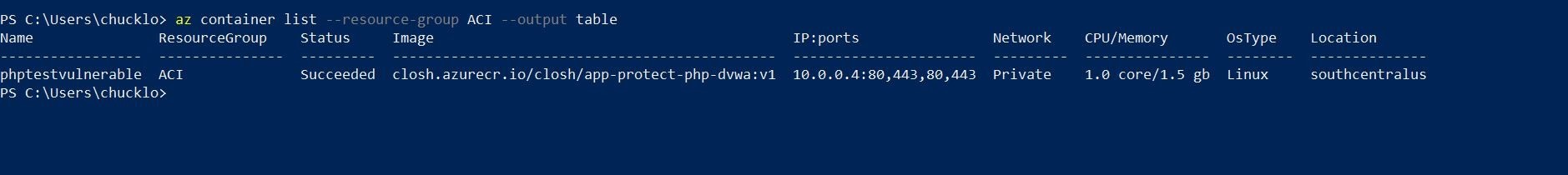
To obtain information about a particular container instance, use the az container display command. Here, it obtains details about the “mycontainer” container, which is housed in the “myResourceGroup” resource group. The Fully Qualified Domain Name (FQDN) and Provisioning State are properties that are exhibited in a table format using the –out table option. The attributes to display are specified by the –query argument.
az container show --resource-group myResourceGroup --name mycontainer
--query "{FQDN:ipAddress.fqdn,ProvisioningState:provisioningState}" --out table
Step 3: Pull The Container Logs
The command listed below can be used to get the logs for a particular container instance. Here, it obtains the logs from the “mycontainer” container, which is housed in the “myResourceGroup” resource group. When the containerized application is operating within the container instance, this command can be useful for monitoring and troubleshooting it.
az container logs --resource-group myResourceGroup --name mycontainerStep 4: Attach output streams
Real-time communication with a container is possible by attaching its standard input, output, and error streams to the local terminal using the az container attach command. Here, it affixes to the “mycontainer” container inside the “myResourceGroup” resource group. The behavior of the containerized application operating within the container instance can be seen and debugged with the help of this command.
az container attach --resource-group myResourceGroup --name mycontainerStep 5: Clean up resources
To remove a container instance, use the az container delete command. In this instance, it removes the “mycontainer” container instance from the resource group “myResourceGroup.” The container instance and its related resources are permanently removed from the Azure environment by using this command.
az container delete --resource-group myResourceGroup --name mycontainer