Windows Server 2012 Hardening (Part I)
Servers are the penultimate layer of security between potential threats and your organization’s data. Therefore, applying proper security policies specifically for each server profile is both important and necessary.
Common sense recommendations are to "stop all unnecessary services" or "turn off unused features". Fortunately, every new version of Windows Server is built to be more secure by default. That said, it is common to have several of different roles assigned to a single server as well as multiple sets of file servers, web servers, database servers, etc. So, how can we guarantee that each of these servers, with their different characteristics, is configured in compliance with the best security practices?
You cannot install SCM 4 on a Windows Server 2012 just like that, you’ll probably get a warning from the Program Compatibility Assistant. This is a known issue when installing SQL Server 2008 Express, even on supported OSes.
Besides, Windows Server is not on the list of SCM 4 supported OSes…
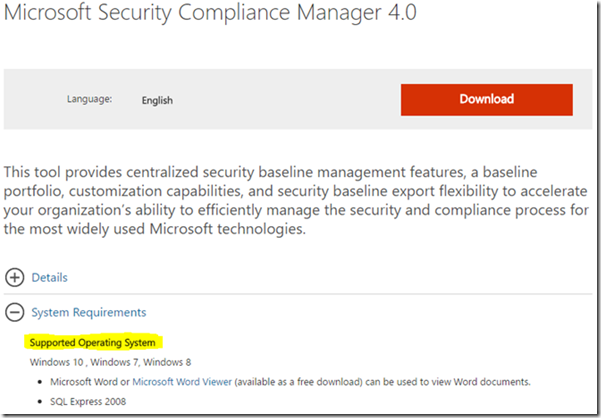
To overcome this, install a newer version of SQL Server, like SQL Server 2014 Express, before installing SCM and everything will go smoothly.
The procedure will be exactly the same as what we did for Windows 10, but now we are going to do same extra steps.
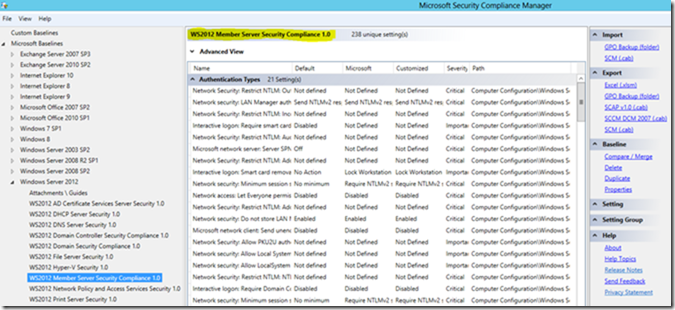
Duplicate and save
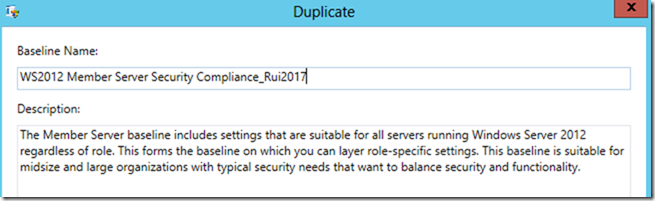
Create a new setting group
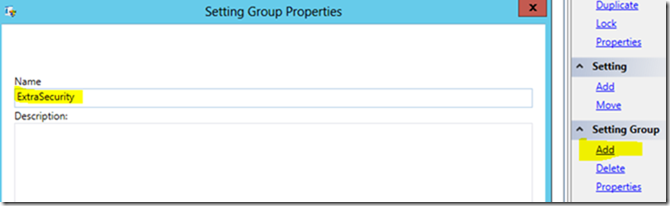
Add setting and select the previously created group
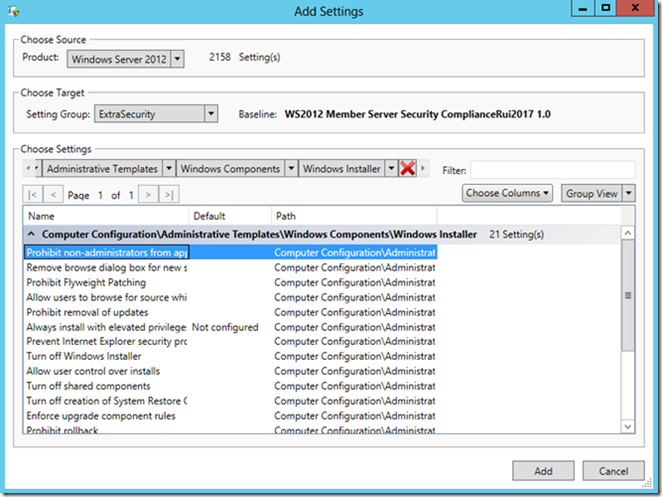
Under Choose Settings, click the black arrow to the left of the red cross and select Computer Configuration from the drop-down menu.
A new menu will appear to the right. Set it to Administrative Templates. Set the following menus to Windows Components and Windows Installer respectively as shown in the figure below.
In the list of settings below the menus, select Prohibit non-administrators from applying vendor signed updates and click Add.
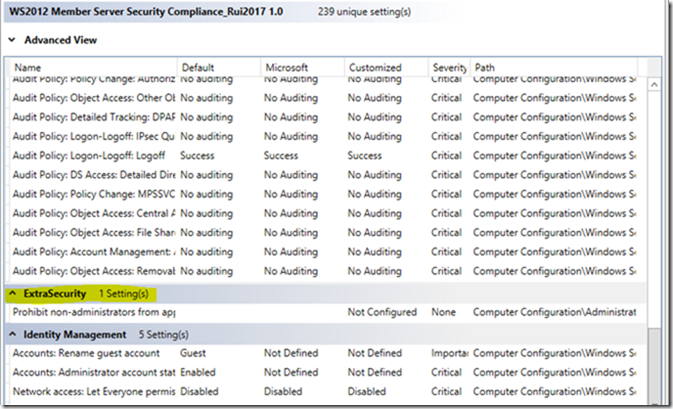
If you scroll down the list of settings in the template in the central pane of SCM, you should now see an ExtraSecurity group with the setting we added in the above steps.
Now, using the Group Policy Management Console (GPMC), we can create a Group Policy Object from the backup we just made.
To start GPMC, open Server Manager and select Group Policy Management from the Tools menu.
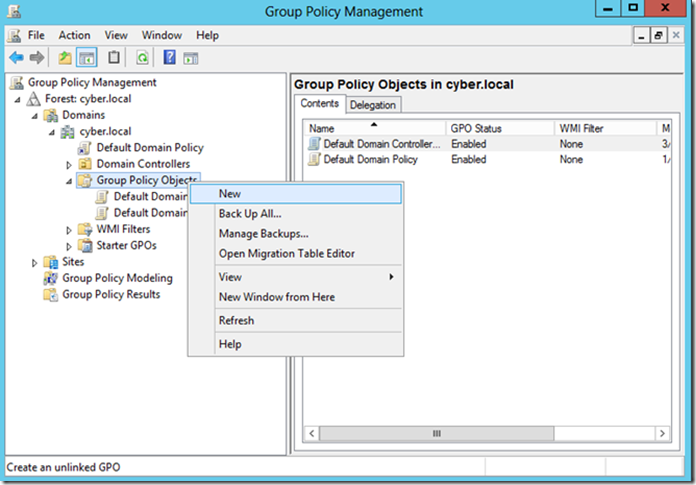
In GPMC, expand your Active Directory (AD) forest and domain in the left pane. In the left pane of GPMC, right click Group Policy Objects and click New.
Name the new GPO and click OK. Right click the GPO you just created and select Import Settings… from the menu
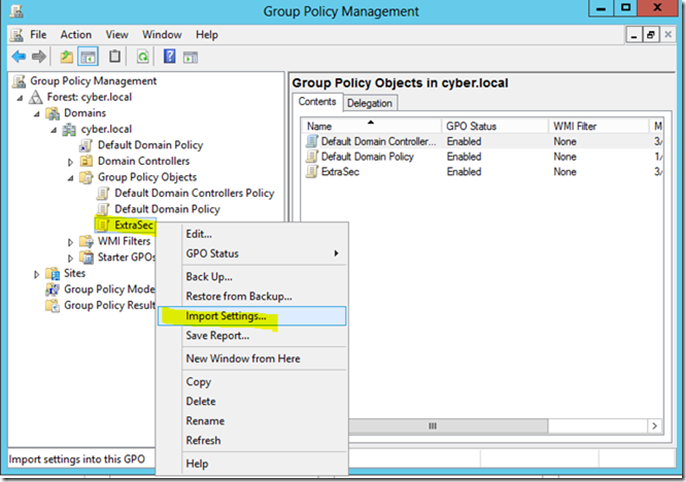
As there are no settings in our GPO, click Next on the Backup GPO screen. On the Backup location screen, click Browse and select the backup folder created using SCM. Click Next to continue
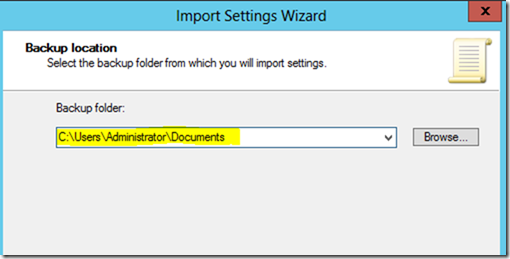
On the Source GPO screen, select the desired GPO backup and click Next.
Wait a second while the wizard scans the backup, then click Next on the Scanning Backup screen.

If the GPO backup contains references to security principals and/or UNC paths, you will be shown the Migrating References screen.
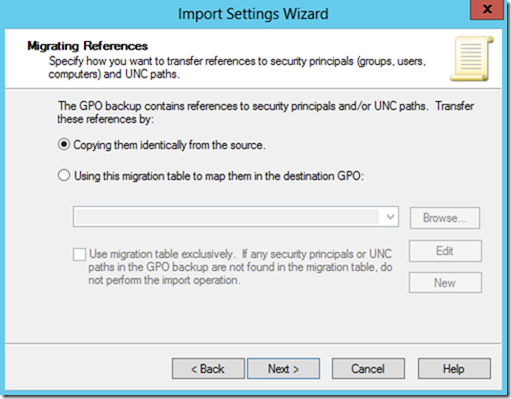
If the GPO contains unique UNCs or security descriptors referencing names of servers or domains, you may need to use a migration table to map them to the new GPO.
If that is the case, choose “Using this migration table to map them in the destination GPO” and then click “New”.
In the Migration Table Editor window, click Tools and select Populate from Backup from the menu.
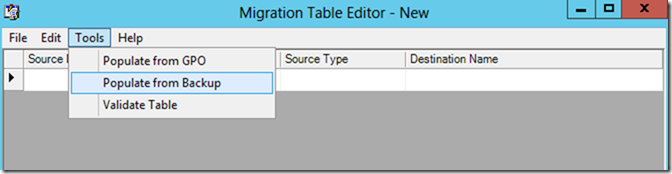
In the Select Backup dialog, make sure the backup location is set to the location of the GPO backup created in SCM, under Backed up GPOs select the GPO backup you created in SCM and then click OK.
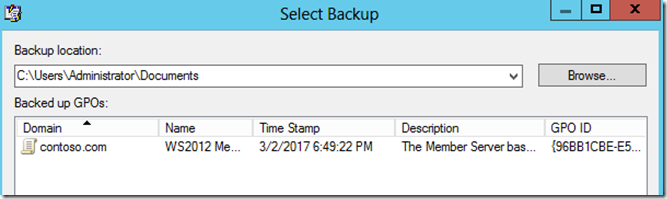
In the Migration Table Editor window, you’ll see the security descriptors and UNC paths listed. If any of them will not work in the target domain, you can type the appropriate path or name in the Destination Name column.
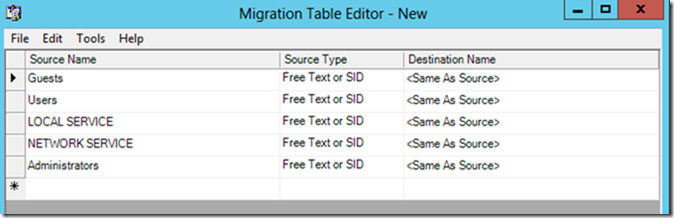
In this example, I don’t need to make any changes as all the security descriptors listed will work in the target domain.
If you made any modifications to the table, select File and then Save from the menu to save the migration table to a location of your choice. Otherwise, close the Migration Table Editor window, and click No when prompted to save the table.
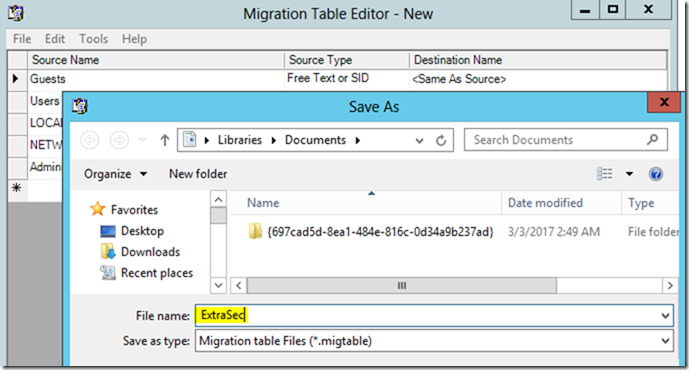
If you save a migration table that you need to use to map the references in the GPO backup for the target domain, click Browse on the Migrating References screen and select the migration table that you just saved.
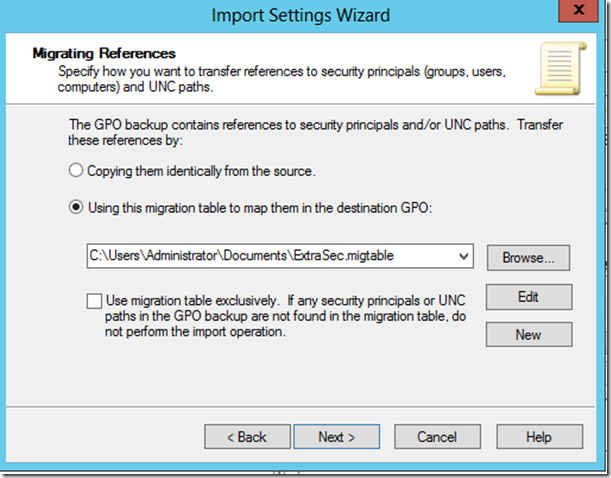
If you don’t need to use a migration table, choose “Copying them identically from the source”.
One more screen and it’s done!
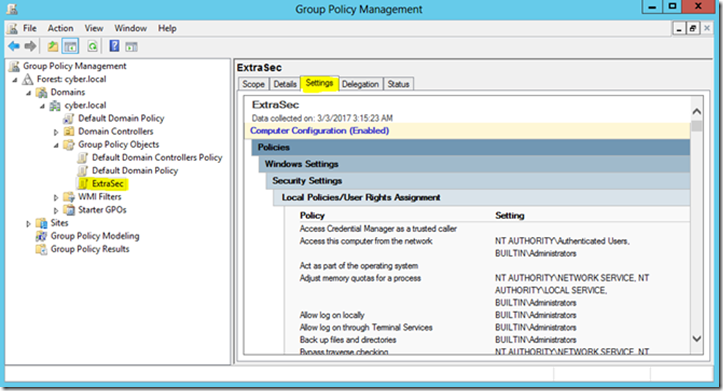
Check your settings:
Previous post: GPEdit vs SecPol
Common sense recommendations are to "stop all unnecessary services" or "turn off unused features". Fortunately, every new version of Windows Server is built to be more secure by default. That said, it is common to have several of different roles assigned to a single server as well as multiple sets of file servers, web servers, database servers, etc. So, how can we guarantee that each of these servers, with their different characteristics, is configured in compliance with the best security practices?
Using the Security Compliance Manager
Using SCM in Windows Server is basically the same as using it on a workstation. The major difference is related to what you can do with your GPOs once you are done.You cannot install SCM 4 on a Windows Server 2012 just like that, you’ll probably get a warning from the Program Compatibility Assistant. This is a known issue when installing SQL Server 2008 Express, even on supported OSes.
Besides, Windows Server is not on the list of SCM 4 supported OSes…

To overcome this, install a newer version of SQL Server, like SQL Server 2014 Express, before installing SCM and everything will go smoothly.
The procedure will be exactly the same as what we did for Windows 10, but now we are going to do same extra steps.
Add a new setting to SCM
Select one of the Windows 2012 Baselines
Duplicate and save

Create a new setting group

Add setting and select the previously created group
Under Choose Settings, click the black arrow to the left of the red cross and select Computer Configuration from the drop-down menu.
A new menu will appear to the right. Set it to Administrative Templates. Set the following menus to Windows Components and Windows Installer respectively as shown in the figure below.
In the list of settings below the menus, select Prohibit non-administrators from applying vendor signed updates and click Add.

If you scroll down the list of settings in the template in the central pane of SCM, you should now see an ExtraSecurity group with the setting we added in the above steps.

Create a GPO based on a SCM template
In the right pane of SCM under Export, click GPO Backup (folder). Select or create a new folder within which to store the backup files and click OK. File Explorer will then open showing the exported Group Policy Object backup.
Now, using the Group Policy Management Console (GPMC), we can create a Group Policy Object from the backup we just made.
To start GPMC, open Server Manager and select Group Policy Management from the Tools menu.
In GPMC, expand your Active Directory (AD) forest and domain in the left pane. In the left pane of GPMC, right click Group Policy Objects and click New.

Name the new GPO and click OK. Right click the GPO you just created and select Import Settings… from the menu

As there are no settings in our GPO, click Next on the Backup GPO screen. On the Backup location screen, click Browse and select the backup folder created using SCM. Click Next to continue

On the Source GPO screen, select the desired GPO backup and click Next.

Wait a second while the wizard scans the backup, then click Next on the Scanning Backup screen.

If the GPO backup contains references to security principals and/or UNC paths, you will be shown the Migrating References screen.

If the GPO contains unique UNCs or security descriptors referencing names of servers or domains, you may need to use a migration table to map them to the new GPO.
If that is the case, choose “Using this migration table to map them in the destination GPO” and then click “New”.
In the Migration Table Editor window, click Tools and select Populate from Backup from the menu.

In the Select Backup dialog, make sure the backup location is set to the location of the GPO backup created in SCM, under Backed up GPOs select the GPO backup you created in SCM and then click OK.

In the Migration Table Editor window, you’ll see the security descriptors and UNC paths listed. If any of them will not work in the target domain, you can type the appropriate path or name in the Destination Name column.

In this example, I don’t need to make any changes as all the security descriptors listed will work in the target domain.
If you made any modifications to the table, select File and then Save from the menu to save the migration table to a location of your choice. Otherwise, close the Migration Table Editor window, and click No when prompted to save the table.

If you save a migration table that you need to use to map the references in the GPO backup for the target domain, click Browse on the Migrating References screen and select the migration table that you just saved.

If you don’t need to use a migration table, choose “Copying them identically from the source”.
One more screen and it’s done!

Check your settings:

Previous post: GPEdit vs SecPol


No comments:
Post a Comment