Linux Hardening with OpenSCAP
The OpenSCAP project is a collection of open source tools for implementing and enforcing this standard, and has been awarded the SCAP 1.2 certification by NIST in 2014. The project provides tools that are free to use anywhere you like, for any purpose.
The OpenSCAP basic tools are:
sudo apt-get install openssh-server
Install OpenSCAP Base:
sudo apt-get install libopenscap8
Get the OVAL file:
wget https://people.canonical.com/~ubuntu-security/oval/com.ubuntu.xenial.cve.oval.xml
oscap oval eval --results /tmp/results-xenial.xml --report /tmp/report-xenial.html com.ubuntu.xenial.cve.oval.xml
You can get a full list of options here.
To see the results:
firefox /tmp/report-xenial.html

dnf install openscap-scanner
Install SCAP Workbench:
dnf install scap-workbench
sudo scap-workbench
Or use the GUI:

SCAP Security Guide:

Run a local scan choosing the General-Purpose compliance tests:

Initial results:
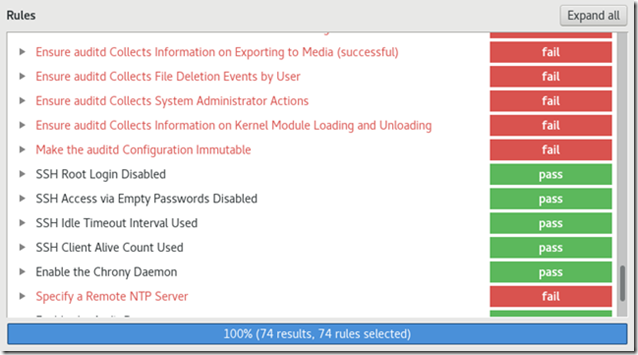
The report:

Explanation for one of the vulnerabilities:

Group by…
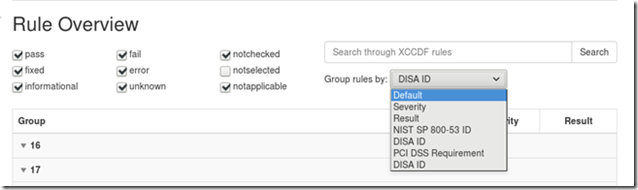
One of OpenSCAP’s best features is the ability to automatically fix some of the vulnerabilities discovered.
Try running a scan choosing the option to Remediate:

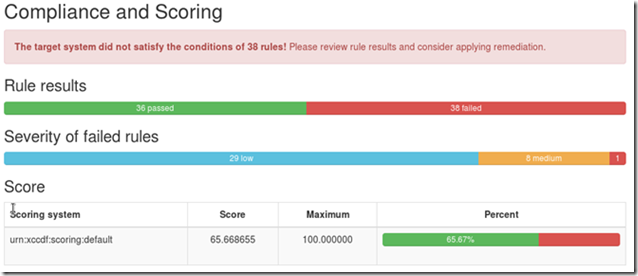
The overall score didn’t improve but some of the medium and low severity flaws were automatically corrected after the scan:
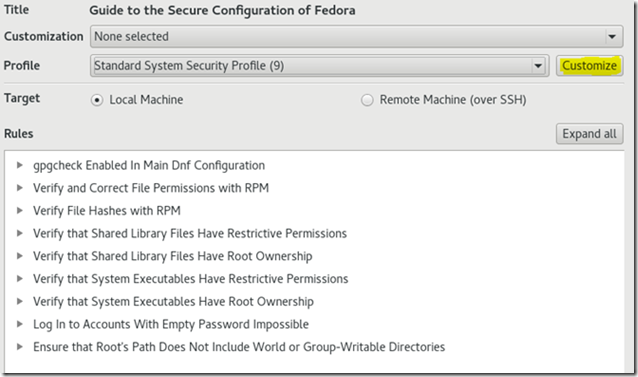
Customize a scan. Start with a small and simple one:
Rename it:

Add some additional scans:

Start:

You’ll get new results according to your customized request:

yum install openscap-scanner
Install SCAP Workbench:
yum install scap-workbench
sudo scap-workbench
Or use the GUI:

SCAP Security Guide:

Run a local scan choosing the Common Profile compliance tests. Choose the option to Fetch Remote Resources.

Notice the availability of several STIGs and other compliance standards.
These are the results:

Now run the same scan but choose to Remediate. This is the new report:
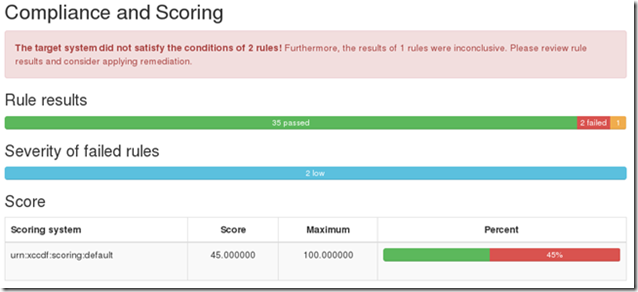
You’ll get the same overall score but the vast majority of flaws were corrected.

https://www.open-scap.org/tools/scap-workbench/download-win32

Download the SCAP Security Guide:
https://github.com/OpenSCAP/scap-security-guide/releases/download/v0.1.31/scap-security-guide-0.1.31-oval-5.10.zip
Extract all files to any directory:

Copy all the.xml files to the SCAP Workbench installation directory replacing the existing ones.



Results:

Try to Remediate remotely:

Not very good, but it works!
The OpenSCAP basic tools are:
- OpenSCAP Base
- Provides a command line tool which enables various SCAP capabilities such as displaying the information about specific security content, vulnerability and configuration scanning, or converting between different SCAP formats.
- SCAP Workbench
- User friendly graphical utility offering an easy way to tailor SCAP content to your needs, perform local or remote scans, and export results.
Using OpenSCAP in Ubuntu
At the time of writing this guide, there was no package available to install OpenSCAP Workbench in Ubuntu. However, it’s possible to use OpenSCAP Base without the GUI, or run a remote scan from other machine, running Windows or other Linux distribution.Installing OpenSCAP
Install SSHsudo apt-get install openssh-server
Install OpenSCAP Base:
sudo apt-get install libopenscap8
Get the OVAL file:
wget https://people.canonical.com/~ubuntu-security/oval/com.ubuntu.xenial.cve.oval.xml
Running OpenSCAP
This is an example usage of the basic command:oscap oval eval --results /tmp/results-xenial.xml --report /tmp/report-xenial.html com.ubuntu.xenial.cve.oval.xml
You can get a full list of options here.
To see the results:
firefox /tmp/report-xenial.html

Using OpenSCAP in Fedora 25
In Fedora, you can install not only the scanner but also the GUIInstalling OpenSCAP
Install OpenSCAP Base using DNF:dnf install openscap-scanner
Install SCAP Workbench:
dnf install scap-workbench
Running OpenSCAP
To run the app under Fedora type:sudo scap-workbench
Or use the GUI:

SCAP Security Guide:

Run a local scan choosing the General-Purpose compliance tests:

Initial results:

The report:

Explanation for one of the vulnerabilities:

Group by…

One of OpenSCAP’s best features is the ability to automatically fix some of the vulnerabilities discovered.
Try running a scan choosing the option to Remediate:

The overall score didn’t improve but some of the medium and low severity flaws were automatically corrected after the scan:

Customize a scan. Start with a small and simple one:

Rename it:

Add some additional scans:

Start:

You’ll get new results according to your customized request:

Using OpenSCAP in CentOS 7
In this OS the procedures are almost exactly the same as for Fedora.Installing OpenSCAP
Install OpenSCAP Base using Yum:yum install openscap-scanner
Install SCAP Workbench:
yum install scap-workbench
Running OpenSCAP
To run the application under CentOS type:sudo scap-workbench
Or use the GUI:

SCAP Security Guide:

Run a local scan choosing the Common Profile compliance tests. Choose the option to Fetch Remote Resources.

Notice the availability of several STIGs and other compliance standards.
These are the results:

Now run the same scan but choose to Remediate. This is the new report:

You’ll get the same overall score but the vast majority of flaws were corrected.
Using OpenSCAP in Windows
You cannot run a scan on a Windows machine because there is no OpenSCAP Base scanner available for this OS. However, you can install OpenSCAP Worbench and use it to remotely scan Linux machinesInstalling OpenSCAP
Download and install the workbench application:https://www.open-scap.org/tools/scap-workbench/download-win32

Download the SCAP Security Guide:
https://github.com/OpenSCAP/scap-security-guide/releases/download/v0.1.31/scap-security-guide-0.1.31-oval-5.10.zip
Extract all files to any directory:

Copy all the.xml files to the SCAP Workbench installation directory replacing the existing ones.

Running OpenSCAP
Now you can run a remote scan of an Ubuntu machine
Results:

Try to Remediate remotely:

Not very good, but it works!

No comments:
Post a Comment