Windows Server 2012 Hardening (Part II)
Using the Security and Configuration Analysis
Microsoft provides security templates for Windows Server and client operating systems, containing security configuration designed for different scenarios and server roles. There are some security templates that are part of the operating system and get applied during different operations, such as when promoting a server to a domain controller.In Windows Server 2008 and later versions, security templates are located in %systemroot%inf and are more limited than in Windows Server 2003. Templates include:
- Defltbase.inf (baseline)
- Defltsv.inf (web/file/print servers)
- DCfirst.inf (for the first domain controller in a domain)
- Defltdc.inf (other domain controllers)
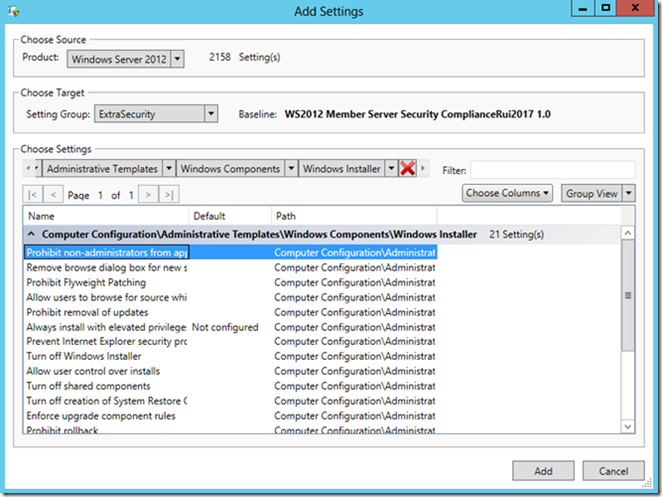
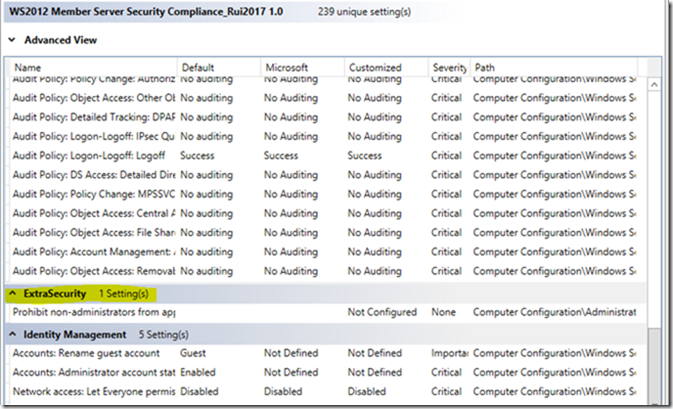
Analyze the baseline template with the Policy Analyzer
Add the baseline template
Compare

Analyze the differences.

Apply the template with SCA
Load the baseline into SCA
Analyze and apply

Repeat the procedure using another of the templates, according to your needs and to the server role in your environment.
Using the Security Configuration Wizard
With the release of the 2003 Service Pack 1 (SP1) version, Windows Server started to include the Security Configuration Wizard tool aimed at analyzing the server’s profile and recommending changes to adjust system’s security according to the server’s role. In Windows Server 2012, the Security Configuration Wizard is conveniently located in the new Server Manager dashboard.Create a new policy with SCW

When starting the Security Configuration Wizard, the first step is to choose which action is going to be performed on the server’s security policy.
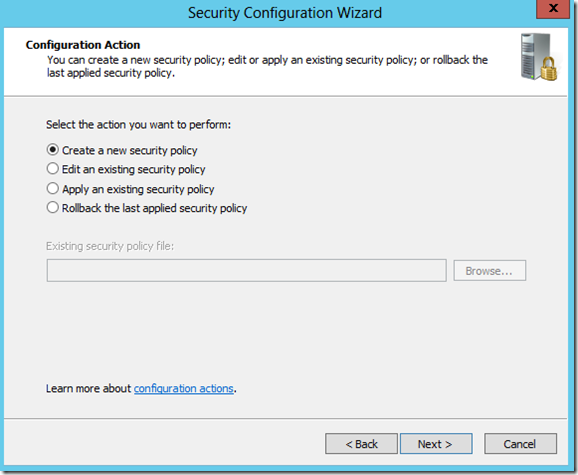
You then select the server that you want to apply the policy to.

In Windows Server 2012, the Security Configuration Wizard then parses the selected server and the information collected, and compares that with Microsoft’s security recommendations for that server profile (file, database, web, etc).

The Security Configuration Database contains information about server roles, client features, administration options, services, Windows Firewall, and other settings.
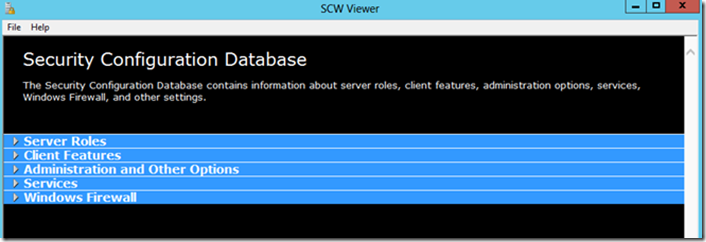
The results of the Security Configuration Wizard analysis, and its suggestions for amendments, will be adapted according to your specific needs.

Select additional services

How do you to handle unspecified services?

Confirm changes
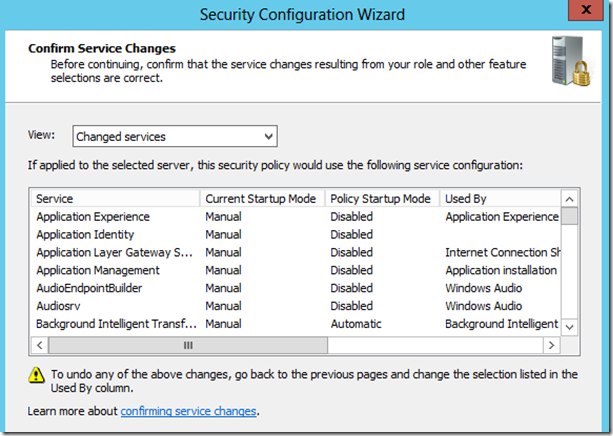
Next, you’ll have the chance to configure firewall policy, registry settings and audit policy or you can skip them. Once the Security Configuration Wizard has completed its analysis and recommendations, you can save and apply the policy.

Want to apply the policy immediately?

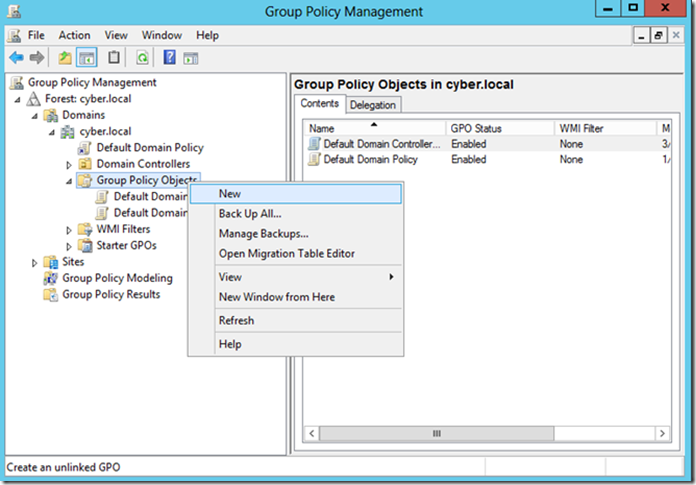
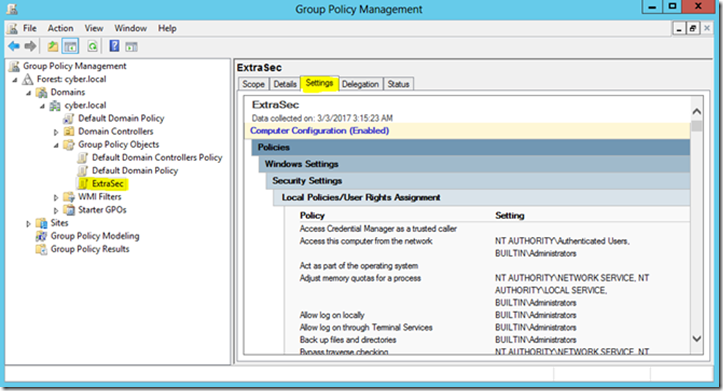
Convert the policy to a GPO
Since there is often more than one server in the profile that was analyzed by the wizard, it might be a good idea to create a Group Policy Object (GPO) to apply that policy to all servers with the same characteristics.To do this, use Windows PowerShell and run the following command:
scwcmd transform /p:<FullFilePathToSecurityPolicy> /g:<GPOName>
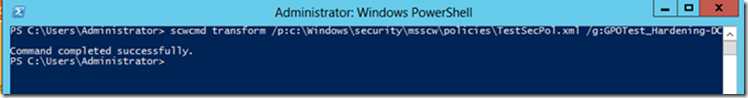
When you run this command, the SCW will create a GPO folder for the newly created GPO in the SYSVOL folder and the GPO will be available in the GPMC for you to use.

This can result in a better standardization of the security policies applied to your environment, and make it easier for you to organize those policies as part of your overall server security strategy.
Edit a policy with SCW
If you feel the need to change your policy definitions, you can edit it with SCW.
Obviously, once the changes are complete you’ll have to reapply the policy
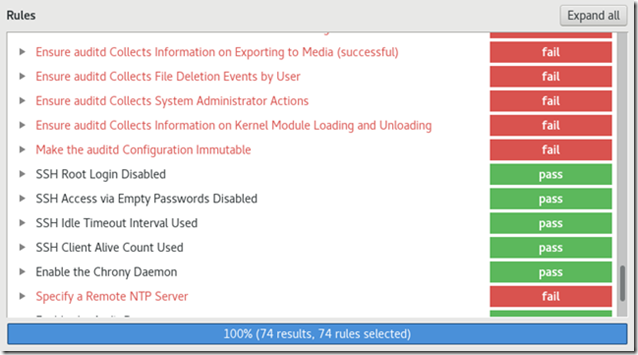
Using the STIGs
Use the STIG Viewer and check the system’s compliance after applying the appropriate Microsoft’s security templates.Don’t forget to use also the STIGs for SQL Server, Exchange, .NET, etc.