Fix common errors for Datadog - An Azure Native ISV Service
Marketplace Purchase errors
The Microsoft.SaaS RP is not registered on the Azure subscription.
- Before you use a resource provider, you must make sure your Azure subscription is registered for the resource provider. Learn more about Resource provider registration and resolving errors on RP registration.
Plan cannot be purchased on a free subscription, please upgrade your account.
- You can't make marketplace purchases on a free Azure subscription. Refer to the Azure free Account FAQ. For more information, see purchase SaaS offer in the Azure portal.
Purchase has failed because we couldn't find a valid payment method associated with your Azure subscription.
- Use a different Azure subscription or add or update current credit card or payment method information for this subscription. For more information, see purchase SaaS offer in the Azure portal.
The Publisher does not make available Offer, Plan in your Subscription/Azure account’s region.
- The offer or the specific plan isn't available to the billing account market that is connected to the Azure Subscription.
Enrollment for Azure Marketplace is set to Free/BYOL SKUs only, purchase for Azure product is not allowed. Please contact your enrollment administrator to change EA settings.
- Enterprise administrators can disable or enable Azure Marketplace purchases for all Azure subscriptions under their enrollment. For more information, see Azure Marketplace - Microsoft Cost Management. More information on different listing options is present in Introduction to listing options
Marketplace is not enabled for the Azure subscription.
- Enterprise administrators can disable or enable Azure Marketplace purchases for all Azure subscriptions under their enrollment. Refer Azure Marketplace - Microsoft Cost Management.
Plan by publisher is not available to you for purchase due to private marketplace settings made by your tenant’s IT administrator.
- Customer uses private marketplace to limit the access of its organization to specific offers and plans. The specific offer or the plan weren't set up to be available in the tenant's private marketplace. Contact your tenant’s IT administrator.
The EA subscription doesn't allow Marketplace purchases.
- Use a different subscription or check if your EA subscription is enabled for Marketplace purchase. For more information, see Enable Marketplace purchases.
If those options don't solve the problem, contact Datadog support.
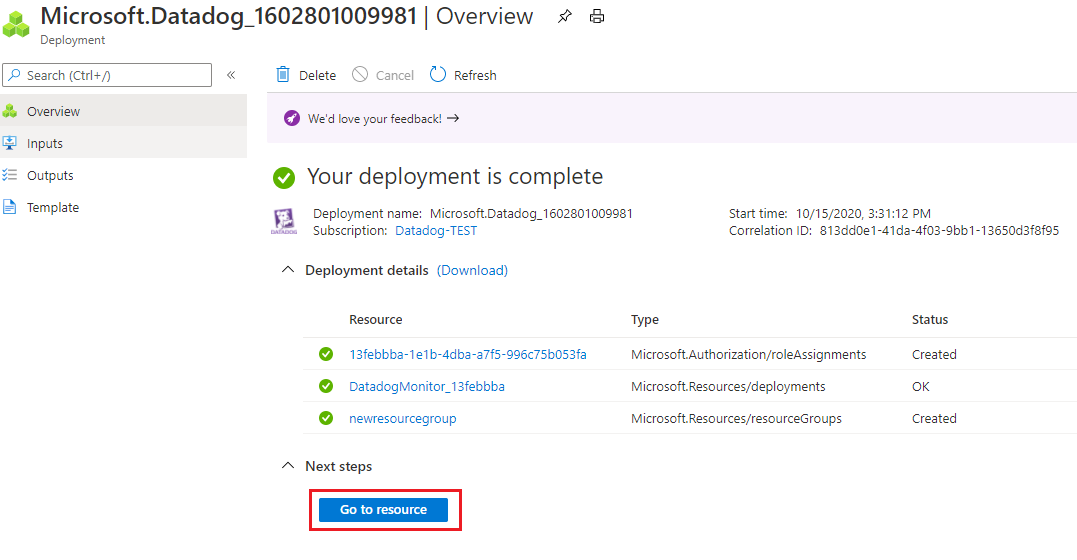
Unable to create Datadog - An Azure Native ISV Service resource
To set up the Azure Datadog integration, you must have Owner access on the Azure subscription. Ensure you have the appropriate access before starting the setup.
Single sign-on errors
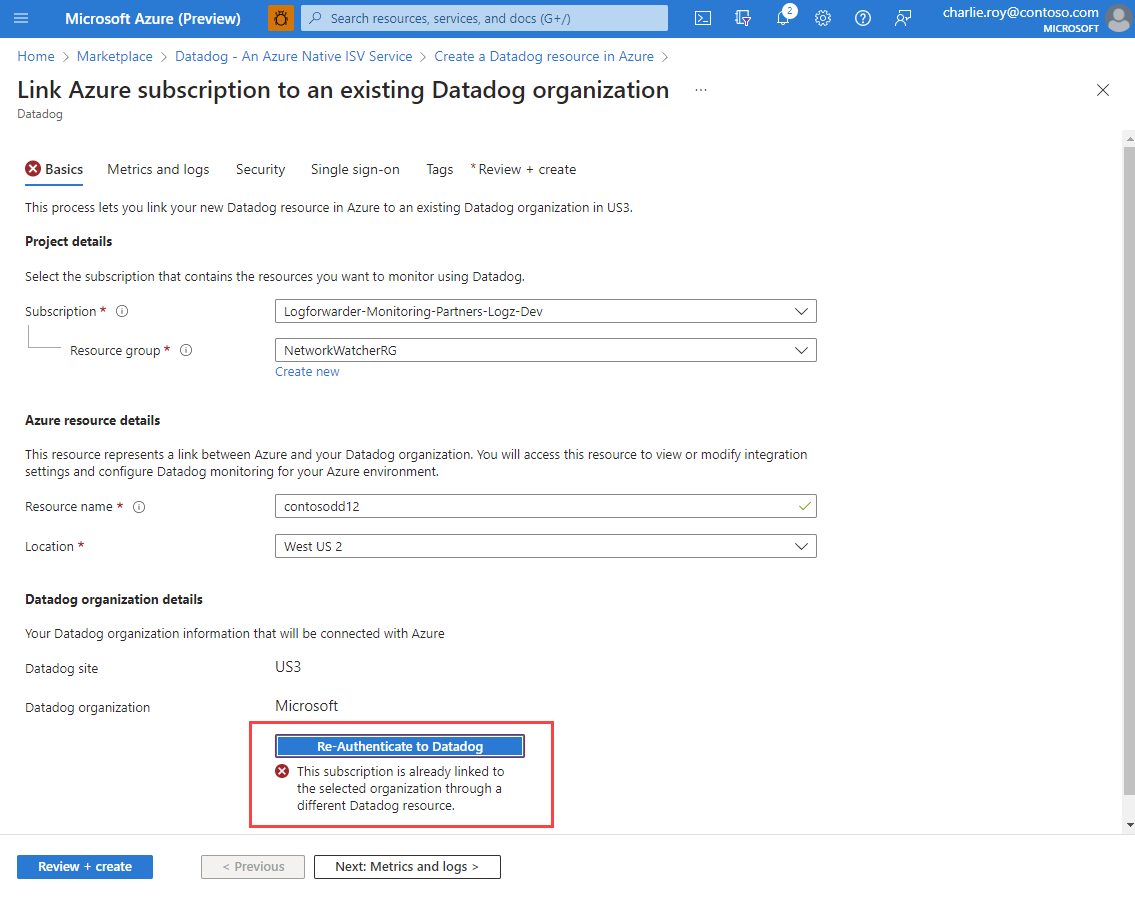
Unable to save Single sign-on settings
- This error happens where there's another Enterprise app that is using the Datadog SAML identifier. To find which app is using it, select Edit on the Basic SAML Configuration section.
To resolve this issue, either disable the other app or use the other app as the Enterprise app to set up SAML SSO with Datadog. If you decide to use the other app, ensure the app has the required settings.
App not showing in Single sign-on setting page
First, search for the application ID. If no result is shown, check the SAML settings of the app. The grid only shows apps with correct SAML settings.
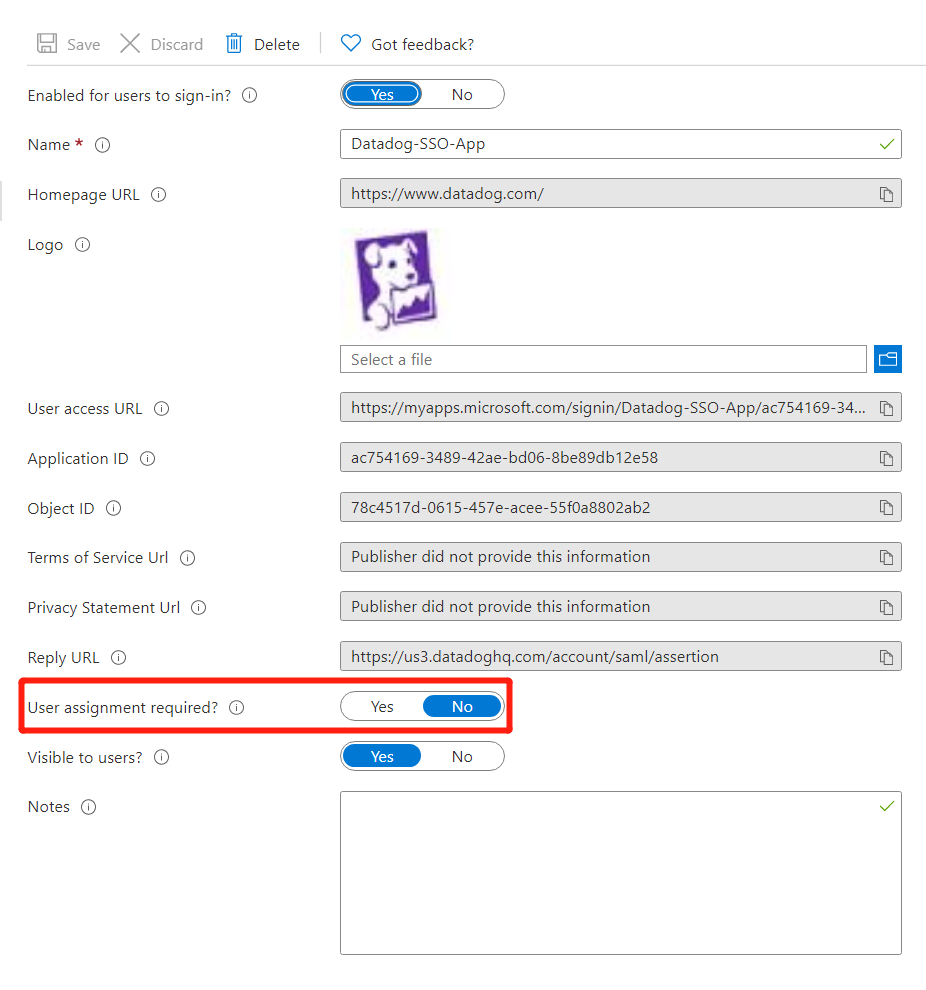
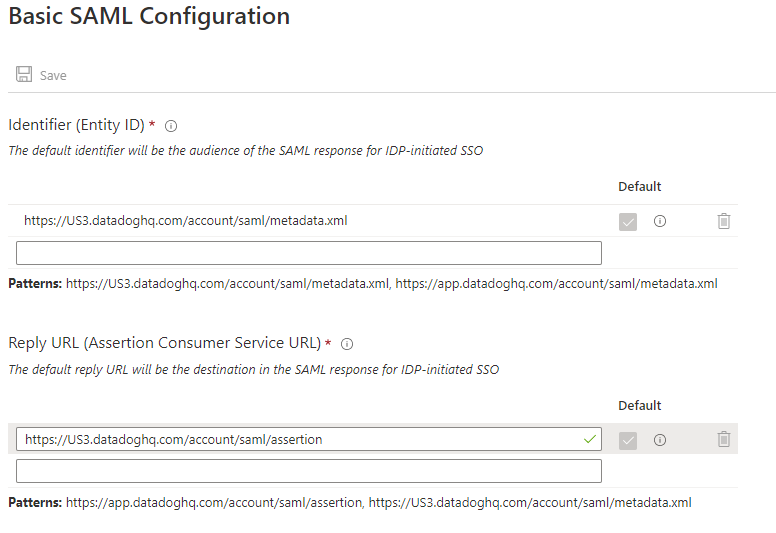
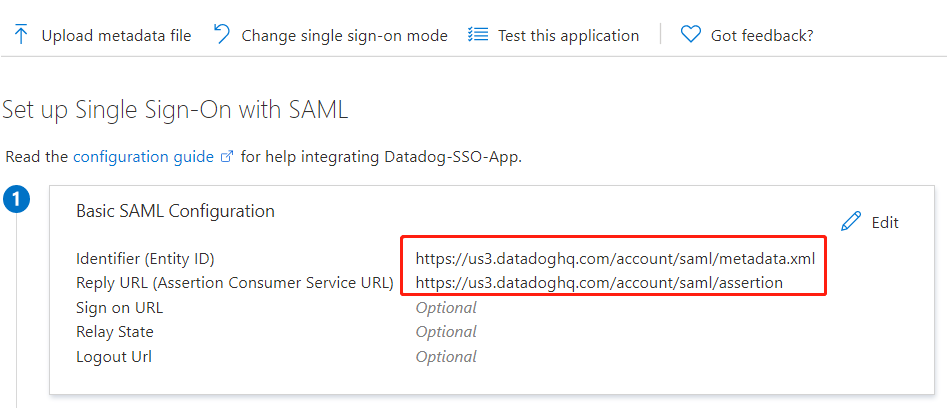
The Identifier URL must be
https://us3.datadoghq.com/account/saml/metadata.xml.The reply URL must be
https://us3.datadoghq.com/account/saml/assertion.The following image shows the correct values.
Guest users invited to the tenant are unable to access Single sign-on
- Some users have two email addresses in Azure portal. Typically, one email is the user principal name (UPN) and the other email is an alternative email.
When inviting guest user, use the home tenant UPN. By using the UPN, you keep the email address in-sync during the Single sign-on process. You can find the UPN by looking for the email address in the top-right corner of the user's Azure portal.
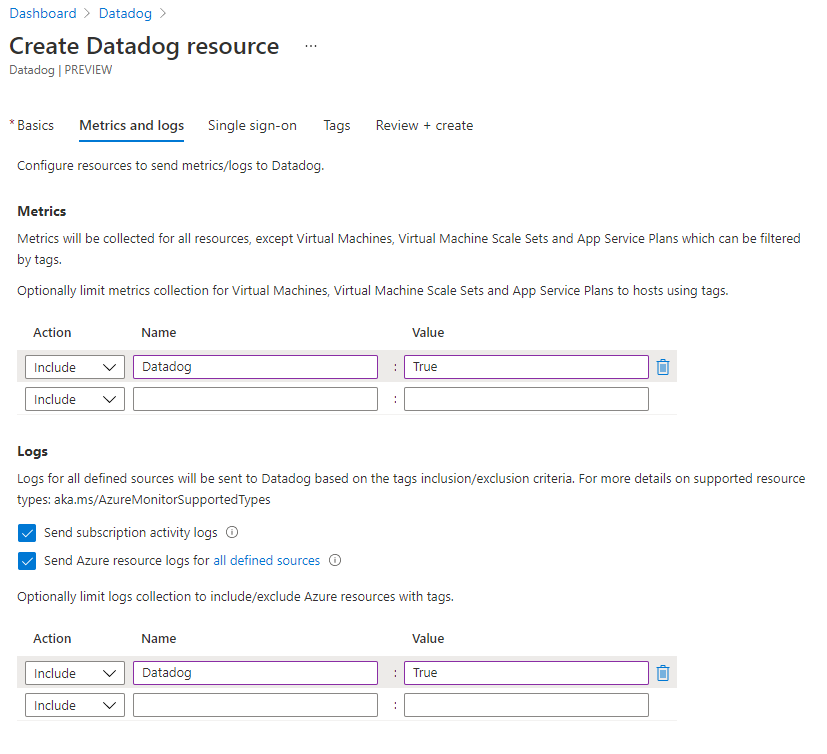
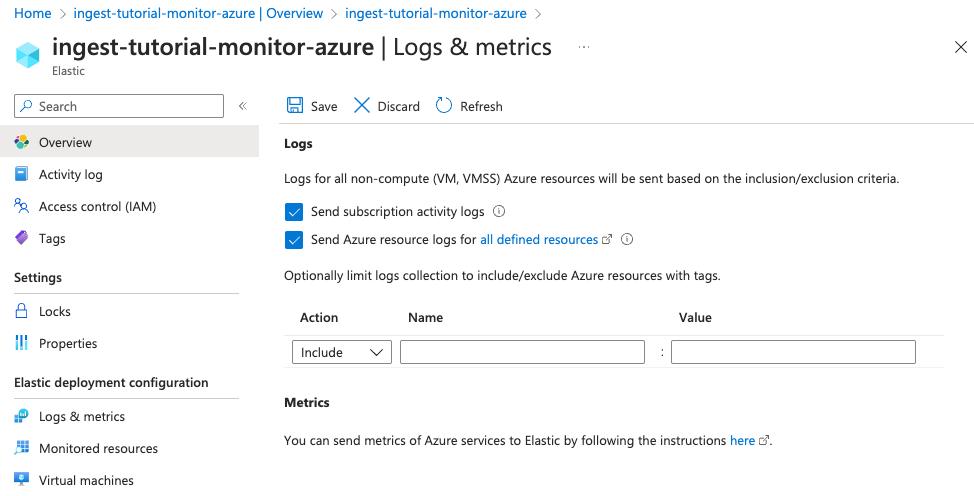
Logs not being emitted
Only resources listed in the Azure Monitor resource log categories emit logs to Datadog.
To verify whether the resource is emitting logs to Datadog:
Navigate to Azure diagnostic setting for the specific resource.
Verify that there's a Datadog diagnostic setting.
Resource doesn't support sending logs. Only resource types with monitoring log categories can be configured to send logs. For more information, see supported categories.
Limit of five diagnostic settings reached. Each Azure resource can have a maximum of five diagnostic settings. For more information, see diagnostic settings.
Export of Metrics data isn't supported currently by the partner solutions under Azure Monitor diagnostic settings.
Metrics not being emitted
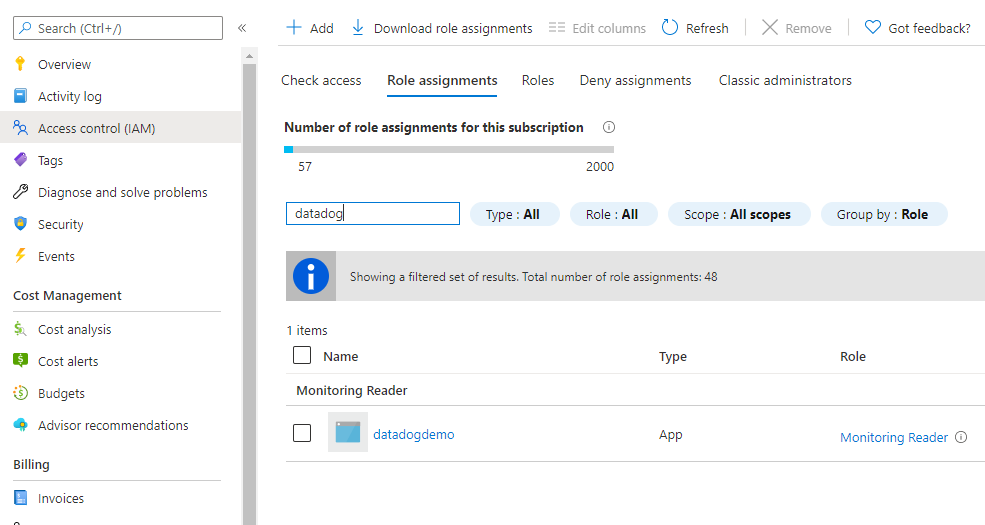
The Datadog resource is assigned a Monitoring Reader role in the appropriate Azure subscription. This role enables the Datadog resource to collect metrics and send those metrics to Datadog.
To verify the resource has the correct role assignment, open the Azure portal and select the subscription. In the left pane, select Access Control (IAM). Search for the Datadog resource name. Confirm that the Datadog resource has the Monitoring Reader role assignment.
Datadog agent installation fails
The Azure Datadog integration provides you with the ability to install Datadog agent on a virtual machine or app service. The API key selected as Default Key in the API Keys screen is used to configure the Datadog agent. If a default key isn't selected, the Datadog agent installation fails.
If the Datadog agent is configured with an incorrect key, navigate to the API keys screen and change the Default Key. You must uninstall the Datadog agent and reinstall it to configure the virtual machine with the new API keys.