Azure is a cloud service which is provided by Microsoft. It allows companies to use Microsoft’s powerful computers and storage over the internet instead of having their own. This helps the companies to run their applications and store their data easily and in a secure way. With the help of Azure, users can create virtual computers, store files, build websites, manage databases, and much more. It provides services to users for machine learning and artificial intelligence too which means users can train computers to recognize images, understand speech, and make smart decisions.
Azure’s strength is its Kubernetes service, which helps the user manage and scale applications that run in containers. Azure also has advanced tools for developing, testing, and deploying software, making it easier for teams to work together. We can say that it provides a wide range of cloud services that help businesses to work more efficiently and are cost-effective as well.
What Is Azure Bastion?
Azure Bastion is a fully managed PaaS service that you provision to securely connect to virtual machines via private IP address. It provides secure and seamless RDP/SSH connectivity to your virtual machines directly over TLS from the Azure portal, or via the native SSH or RDP client already installed on your local computer. When you connect via Azure Bastion, your virtual machines don’t need a public IP address, agent, or special client software. Bastion service opens the RDP/SSH session/connection to your virtual machine over the private IP of your virtual machine, within your virtual network.
- Direct connection for RDP and SSH sessions in the Azure Portal and native client with a single click
- Support without the need for an agent in your VM or additional software on your browser
- Integration of existing firewalls and security perimeters using a modern HTML5-based web client and standard TLS ports
- Scalability with Bastion Standard to manage additional concurrent SSH and RDP connections
Bastion provides secure RDP and SSH connectivity to all of the VMs in the virtual network for which it’s provisioned. Using Azure Bastion protects your virtual machines from exposing RDP/SSH ports to the outside world, while still providing secure access using RDP/SSH.
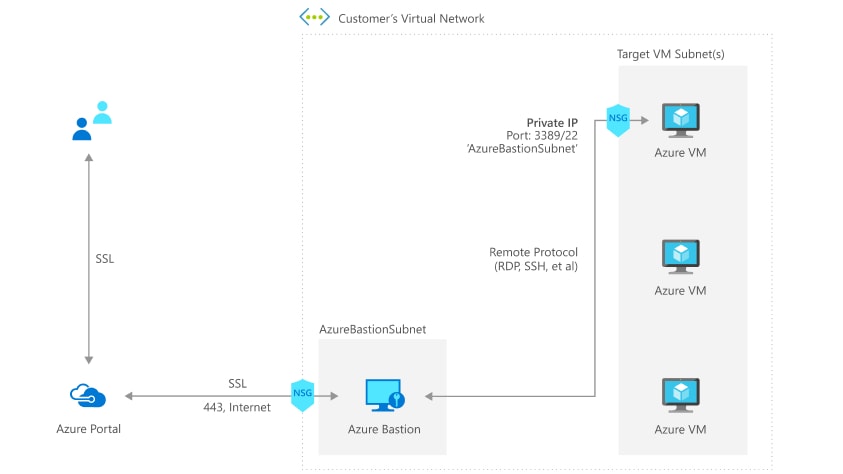
Architecture Of Azure Boston
- This section applies to all SKU tiers except the Developer SKU, which is deployed differently. Azure Bastion is deployed to a virtual network and supports virtual network peering. Specifically, Azure Bastion manages RDP/SSH connectivity to VMs created in the local or peered virtual networks.
- RDP and SSH are some of the fundamental means through which you can connect to your workloads running in Azure. Exposing RDP/SSH ports over the Internet isn’t desired and is seen as a significant threat surface. This is often due to protocol vulnerabilities. To contain this threat surface, you can deploy bastion hosts (also known as jump-servers) at the public side of your perimeter network. Bastion host servers are designed and configured to withstand attacks. Bastion servers also provide RDP and SSH connectivity to the workloads sitting behind the bastion, as well as further inside the network.
- Currently, by default, new Bastion deployments don’t support zone redundancies. Previously deployed bastions might, or might not, be zone-redundant. The exceptions are Bastion deployments in Korea Central and Southeast Asia, which do support zone redundancies.
-min.png)
This figure shows the architecture of an Azure Bastion deployment. This diagram doesn’t apply to the Developer SKU. In this diagram:
- The Bastion host is deployed in the virtual network that contains the Azure Bastion Subnet subnet that has a minimum /26 prefix.
- The user connects to the Azure portal using any HTML5 browser.
- The user selects the virtual machine to connect to.
- With a single click, the RDP/SSH session opens in the browser.
- No public IP is required on the Azure VM.
Setting Up Azure Bastion: A Step-By-Step Guide
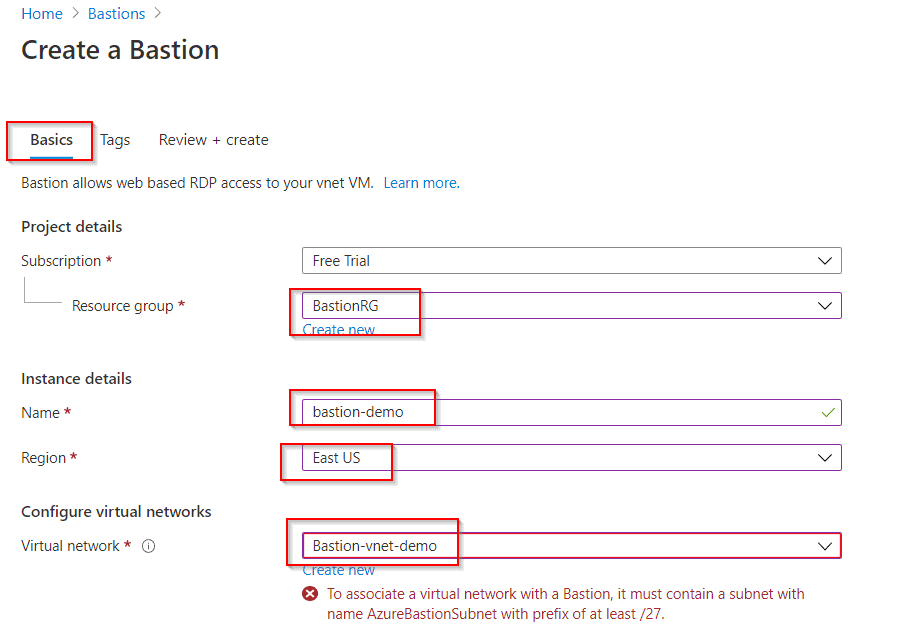
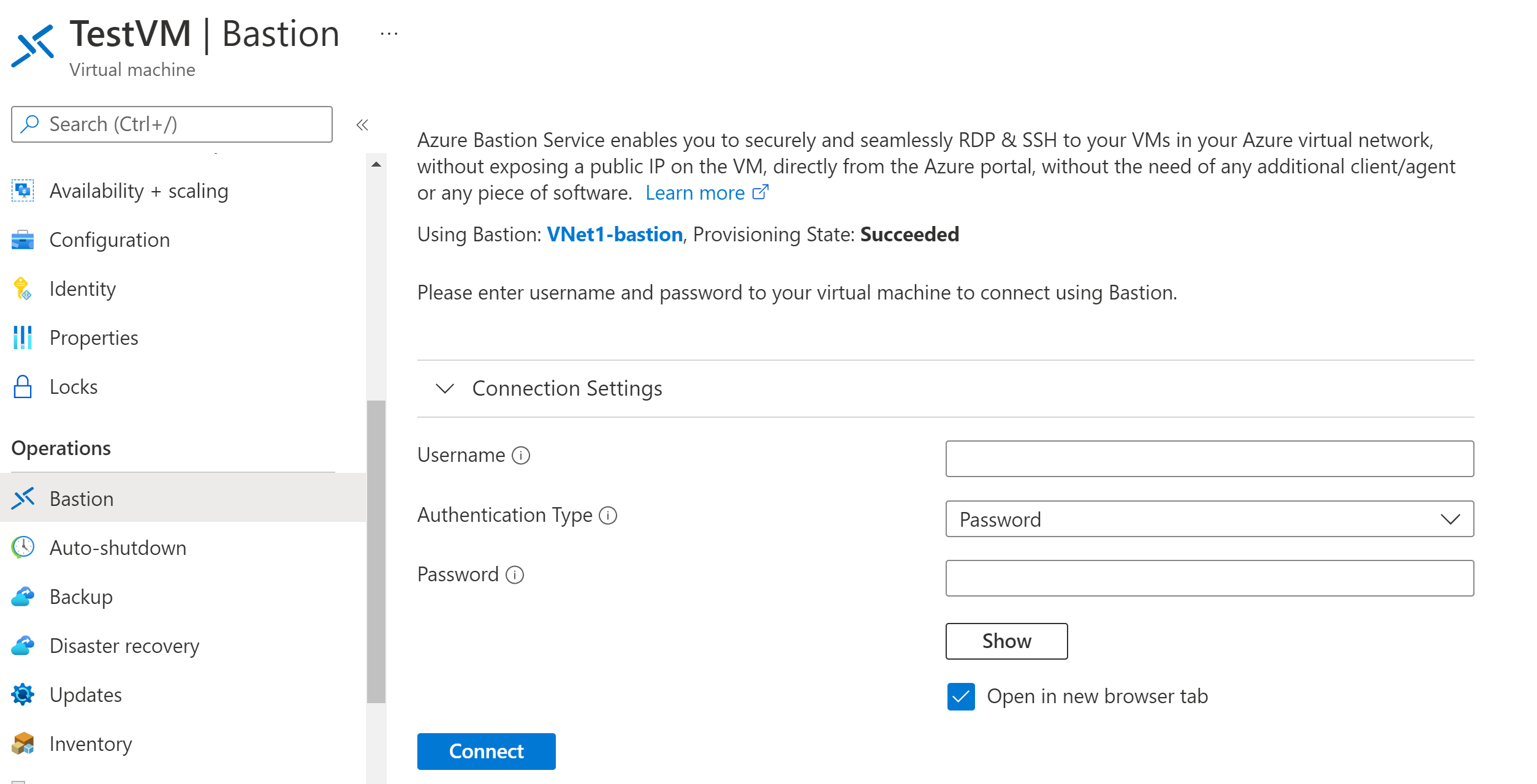
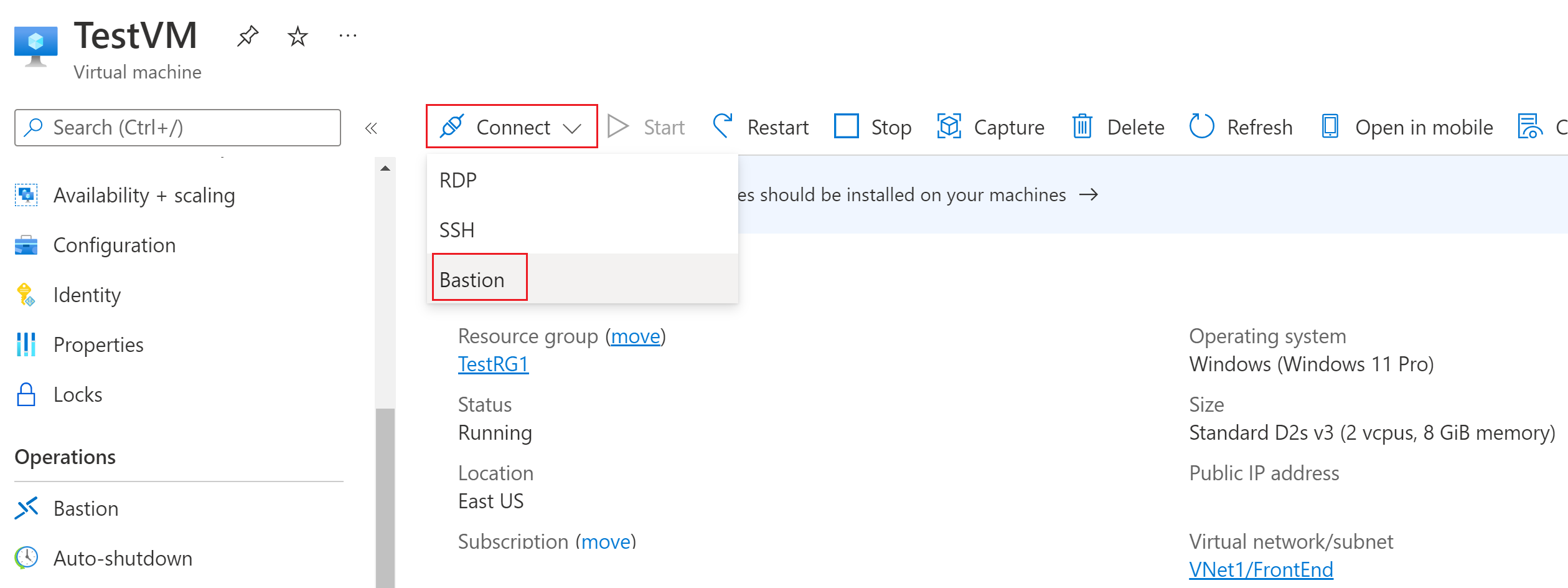
Step 1: Sign in to Azure Portal your azure portal and search for Azure bastion.
.jpg)
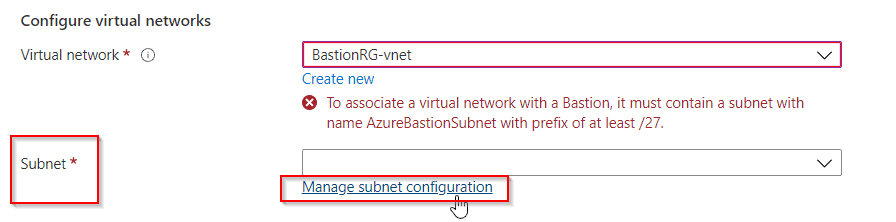
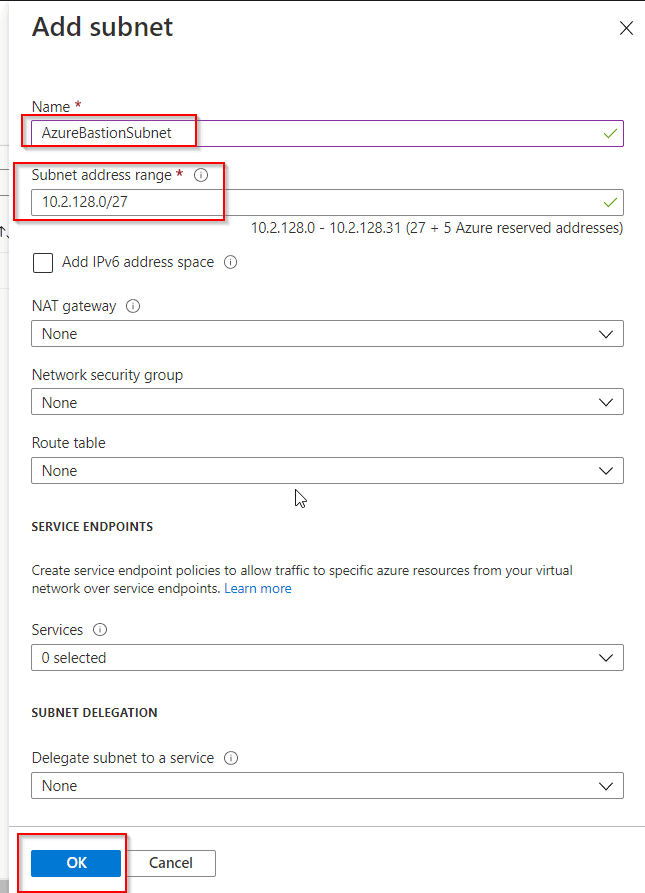
Step 2: Create a Azure bastion and then set up a subnet for Azure bastion.
.jpg)
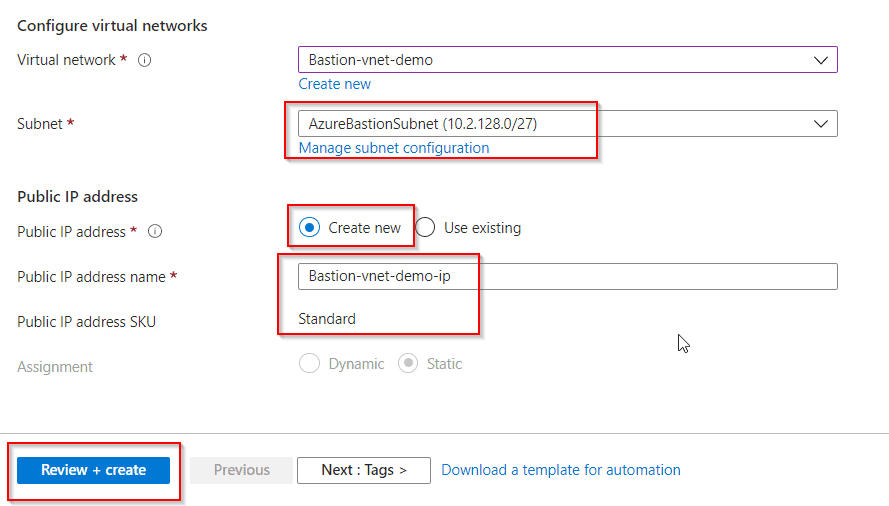
Step 3: Create a VM & Deploy your VM carefully. It might take 5-7 minutes to complete the setup.
.jpg)
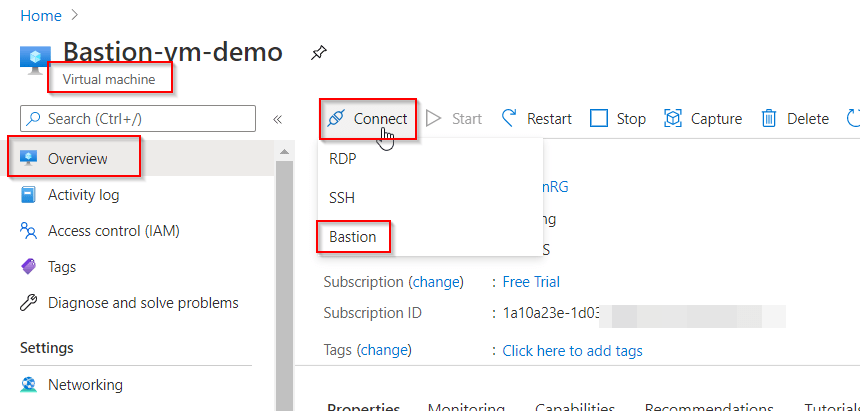
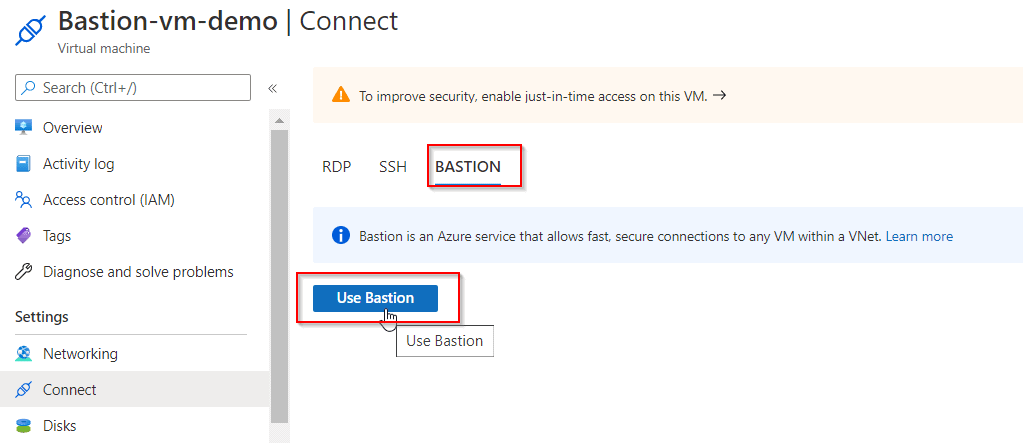
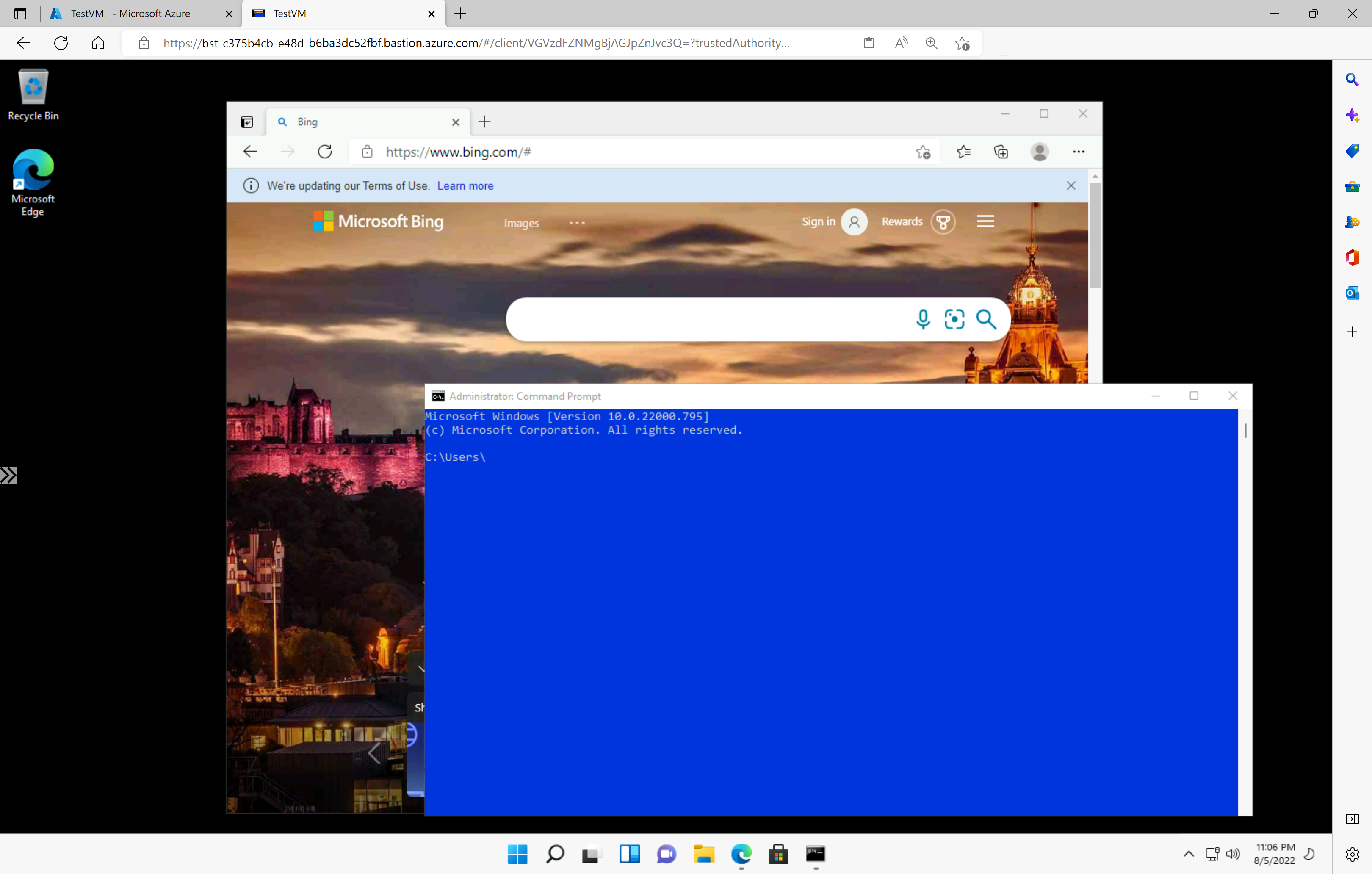
Step 4: Configure your Azure Bastion and Connect your VM Via Azure Bastion.
.jpg)
Step 5: Now Configure the Network Security Groups Rules and Verify the Connectivity properly.
.jpg)
Step 6: Clean it Up And Optimize it very carefully.
.jpg)
Advantages Of Azure Bastion
- There are several benefits we have to opt the Azure Boston to set up virtual machines via private IP address. Following table illustrates some main key benefits of using Azure Boston:
Benefit | Description |
|---|
RDP and SSH through the Azure portal | You can get to the RDP and SSH session directly in the Azure portal using a single-click seamless experience. |
|---|
Remote Session over TLS and firewall traversal for RDP/SSH | Azure Bastion uses an HTML5 based web client that is automatically streamed to your local device. Your RDP/SSH session is over TLS on port 443. This enables the traffic to traverse firewalls more securely. Bastion supports TLS 1.2. Older TLS versions aren’t supported. |
|---|
No Public IP address required on the Azure VM | Azure Bastion opens the RDP/SSH connection to your Azure VM by using the private IP address on your VM. You don’t need a public IP address on your virtual machine. |
|---|
No hassle of managing Network Security Groups | you don’t need to apply any NSGs to the Azure Bastion subnet. Because Azure Bastion connects to your virtual machines over private IP, you can configure your NSGs to allow RDP/SSH from Azure Bastion only. This removes the hassle of managing NSGs each time you need to securely connect to your virtual machines. |
|---|
No need to manage a separate bastion host on a VM | Azure Bastion is a fully managed platform PaaS service from Azure that is hardened internally to provide you secure RDP/SSH connectivity. |
|---|
Protection against port scanning | Your VMs are protected against port scanning by rogue and malicious users because you don’t need to expose the VMs to the internet. |
|---|
Hardening in one place only | Azure Bastion sits at the perimeter of your virtual network, so you don’t need to worry about hardening each of the VMs in your virtual network. |
|---|
Protection against zero-day exploits | The Azure platform protects against zero-day exploits by keeping the Azure Bastion hardened and always up to date for you. |
|---|
Disadvantages Of Azure Bastion
The following are the disadvantages of Azure Bastion:
- Distance to Azure data centers could cause slow performance.
- Local Boston data laws might be complicated to follow on Azure.
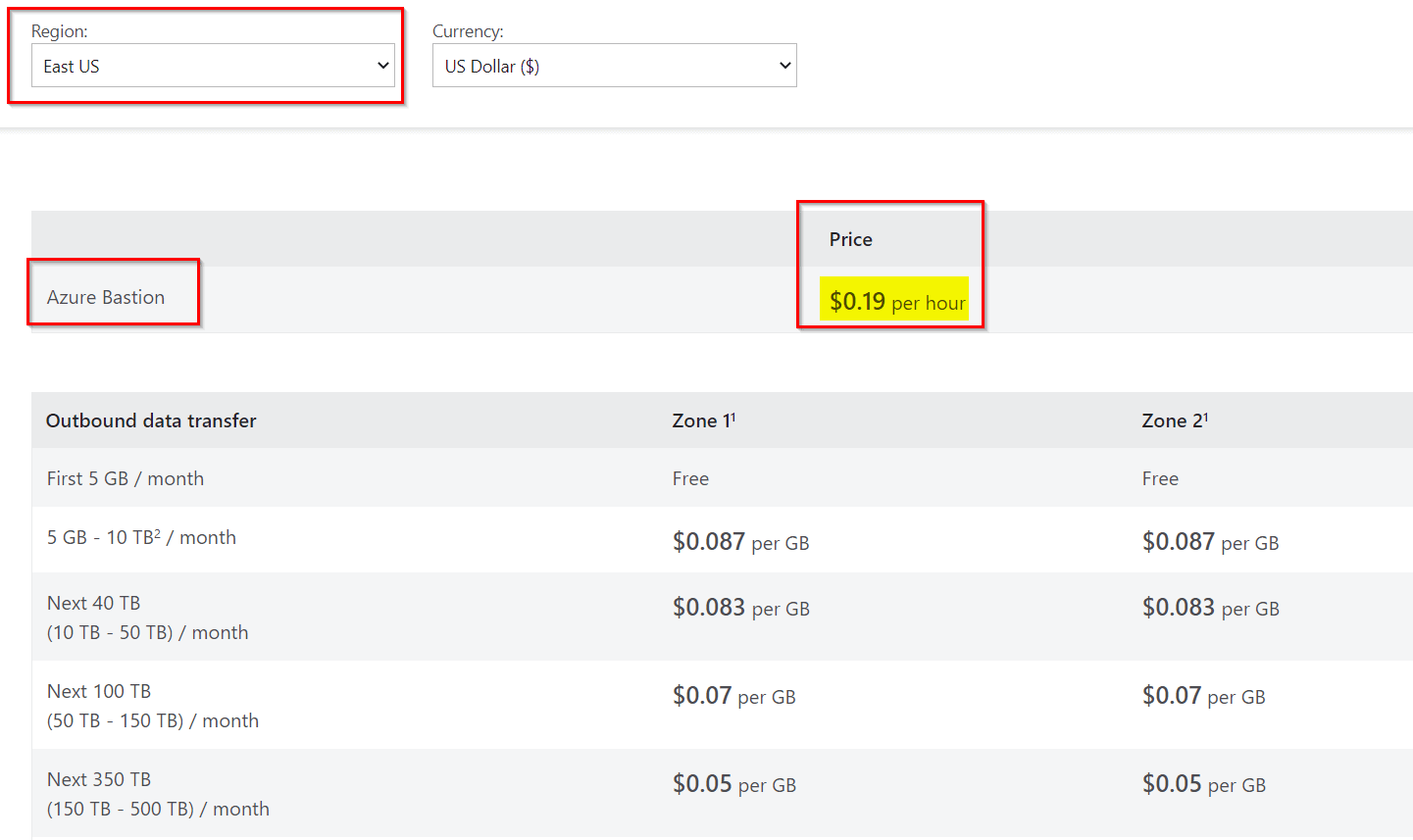
- Using Azure can get expensive depending on how much you use it.
- Azure depends on good internet access, which can be unstable in some areas.
- With Azure, Microsoft manages the infrastructure instead of you. This means you have less control, which some may see as a drawback.
Conclusion
In summary, Azure Bastion provides a secure and easy way for organizations to access their Azure virtual machines over the internet. It offers enhanced security, simplified management, and can help meet compliance rules. This makes Azure Bastion a helpful service for many companies using Azure. However, organizations need to evaluate if Azure Bastion fits their particular needs before deploying it. Aspects like cost, ability to scale, and how it integrates with current systems should be considered. Though it has many benefits, Azure Bastion may not be suitable for every organization.
Azure Bastion – FAQ’s
What Do You Mean By Azure Bastion?
Azure Bastion is a fully managed PaaS service that you provision to securely connect to virtual machines via private IP address. It provides secure and seamless RDP/SSH connectivity to your virtual machines.
Why Is There A Need Of The Azure Bastion?
Bastion provides secure RDP and SSH connectivity to all of the VMs in the virtual network for which it’s provisioned. Using Azure Bastion protects your virtual machines from exposing RDP/SSH ports to the outside world, while still providing secure access using RDP/SSH.
How To Build The Azure Bastion?
Sign in to Azure Portal your azure portal and search for Azure bastion. Create a Azure bastion and then set up a subnet for Azure bastion.
Explain Any Two Features Of Azure Bastion.
- You can get to the RDP and SSH session directly in the Azure portal using a single-click seamless experience.
- Your VMs are protected against port scanning by rogue and malicious users because you don’t need to expose the VMs to the internet.
What Are The Limitations Of The Azure Bastion?
Using Azure can get expensive depending on how much you use it and it also depends on good internet access, which can be unstable in some areas.

-min.png)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)
.jpg)