Overview And Steps to Create
In this blog, you’ll learn what Azure Bastion is, get a high-level overview of its architecture, and learn how to create your first Azure Bastion host.
What is Azure Bastion Host?
Azure Bastion is a fully platform-managed PaaS service that provides RDP/SSH over TLS i.e. port 443 to all the VMs in the network. Think of this as a managed Jump Box or Jump Server service provided by Microsoft.
Before we move on to Azure Bastion, let’s first understand what a Jump Box or Jump Host is. Jump Box is a virtual machine that sits over a virtual network and prevents all the other Virtual Machines from being exposed to the public.
This means that Jump Box acts as the doorway to all the RDP connections made to your VMs. Furthermore, while using a Jump Box, only a single port will be exposed instead of multiple ports that are exposed when we don’t use it.
Now, let’s come back to Azure Bastion. Azure Bastion is a managed Jump Box. What does managed means? It means that we can configure our Jump Box according to our needs. Remember, you cannot interact with it directly, but you can configure it. It supports both RDP (Remote Desktop Protocol) & SSH connections, and you can also play with its NSG (Network Security Group) to make your connection even more secure.
Well, I guess you’re stuck, aren’t you? No, not at all–relax. In this post, I’ll show you how to use Azure Bastion as well.
Azure Bastion Architecture
Azure Bastion deployment is per virtual network, not per subscription/account or virtual machine. Once you provision an Azure Bastion service in your virtual network, the RDP/SSH experience is available to all your VMs in the same virtual network.
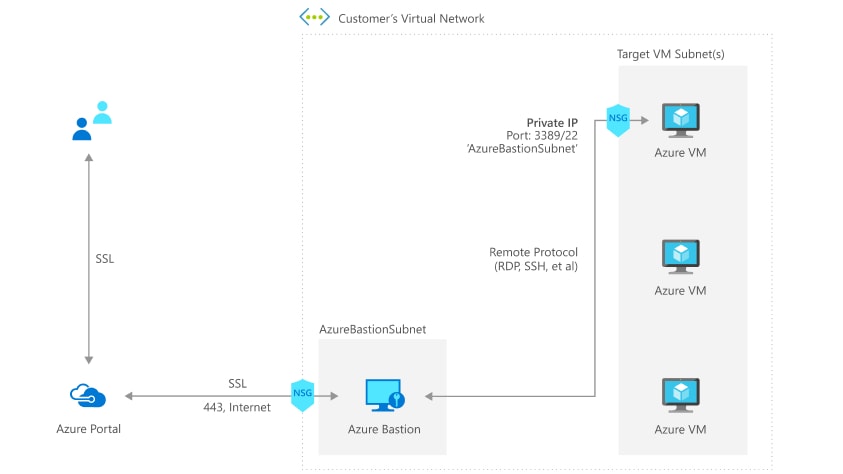
So here is how the connectivity works:
- You connect to the Azure management portal over HTTPS using any browser, then you select a virtual machine to connect to.
- Now the Azure portal connects to the Azure Bastion service using the Private IP on port 443.
- You get a new session in your browser and you can browse the desktop of the virtual machine and any other VMs inside your network using RDP or SSH.
Key benefits of Azure Bastion
RDP and SSH through the Azure portal : You can access RDP and SSH sessions directly from the Azure portal, using a seamless one-time experience.
Remote Session over TLS and firewall traversal for RDP/SSH : Azure Bastion uses an HTML5-based web client that automatically streams to home devices. Your RDP/SSH session happens over TLS on port 443. This allows traffic to pass through the firewall more securely. Bastion supports TLS 1.2 and higher.
No Public IP address required on the Azure VM : Azure Bastion opens an RDP/SSH connection to an Azure VM using the VM’s IP address. Your virtual machine does not need a public IP address.
No hassle of managing Network Security Groups (NSGs) : There is no need to use NSG for Azure Bastion subnet. Because Azure Bastion connects to the virtual machine via a private IP, you can configure NSG to only allow RDP/SSH from Azure Bastion. This takes the hassle out of managing NSGs when you need to securely connect to a virtual machine. For more information about NSGs, see NSGs. Network Security Groups.
No need to manage a separate bastion host on a VM : Azure Bastion is an Azure managed platform PaaS service with built-in power to provide you with secure RDP/SSH connections.
Host scaling
Azure Bastion supports hosting. The number of hosts (volumes) can be configured to control the number of RDP/SSH connections Azure Bastion can support. Increasing the number of hosts allows Azure Defense to handle more traffic. Reducing the number of events will reduce the number of supported integrations. Azure Bastion supports up to 50 hosts.
This feature is only available for Azure Bastion Standard SKU.
Azure Bastion Use Cases
Now let’s list some possible use-cases. Azure Bastion can be very useful (but not limited) to these scenarios:
- Your Azure-based VMs are running in a subscription where you’re unable to connect via VPN, and for security reasons, you cannot set up a dedicated Jump-host within that VNet.
- You want to give developers access to a single VM without giving them access to additional services like a VPN or other things running within the VNet.
- You want to implement Just in Time (JIT) Administration in Azure. You can deploy and enable Bastion Host on the fly and as you need it.
Azure Bastion Pricing and Features
- Secure and seamless RDP and SSH access to your virtual machines.
- No Public IP exposure on the VM.
- Help limit threats such as port scanning and other types of malware targeting your VMs.
- Uses a modern HTML5-based web client and standard SSL ports. This makes Firewall and other security rules very easy to manage.
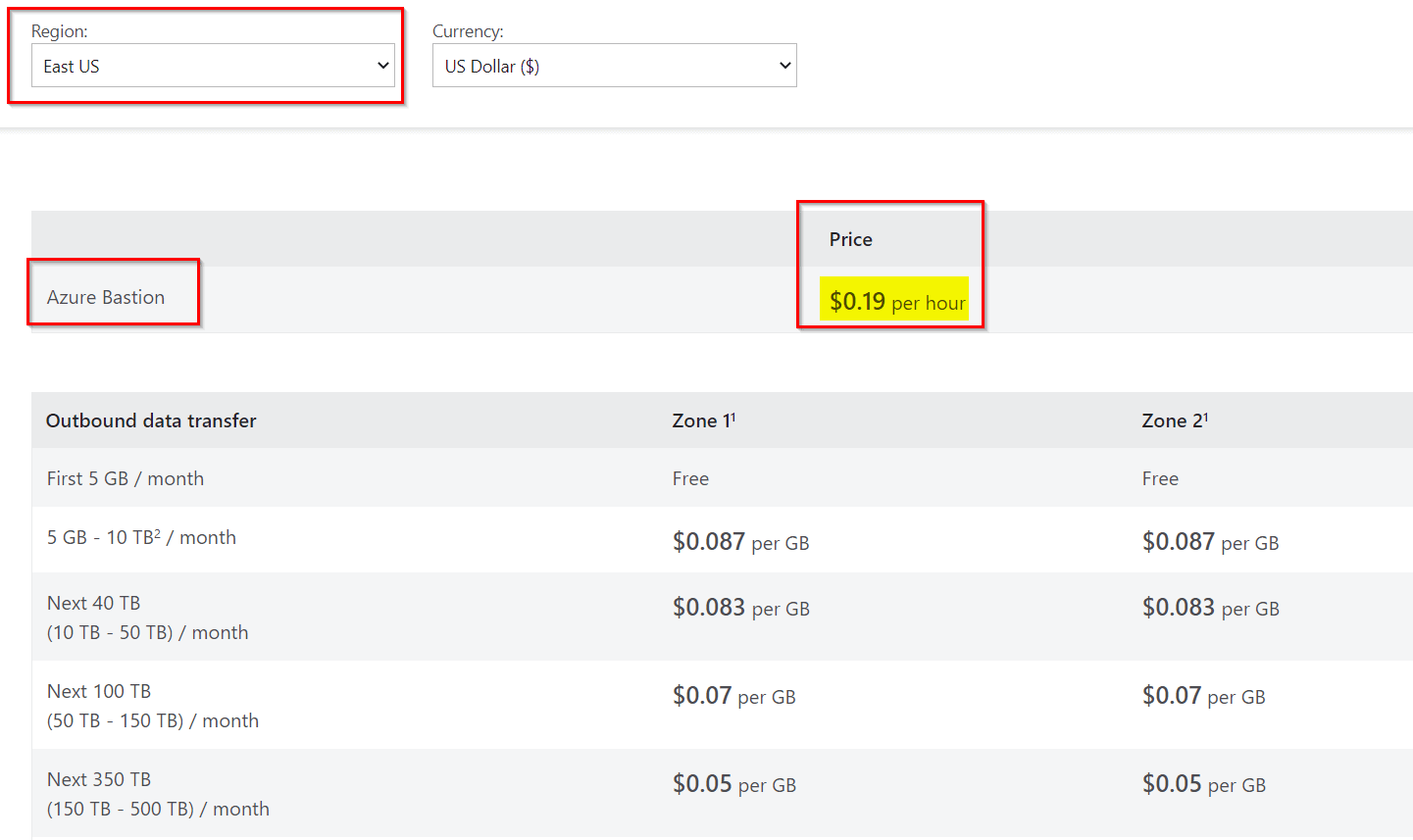
- Fixed charge for the service. This is the charge billed hourly for deploying the service. E.g. in an East US location, this charge is around $0.19 per hour.
- Outbound data transfer charges. This is the charge based on the total outbound data transfer. This is further tiered into various categories based on the total consumption.
How to Configure Azure Bastion?
1. Log into your Azure Portal and head to the search area. In the search box, search for Bastion. Go through the results and click on the Create button as soon as you see Bastion with Microsoft as its publisher.
2. Enter your usual details such as Subscription, Resource Group, Instance name, Region, and Virtual Network as well.
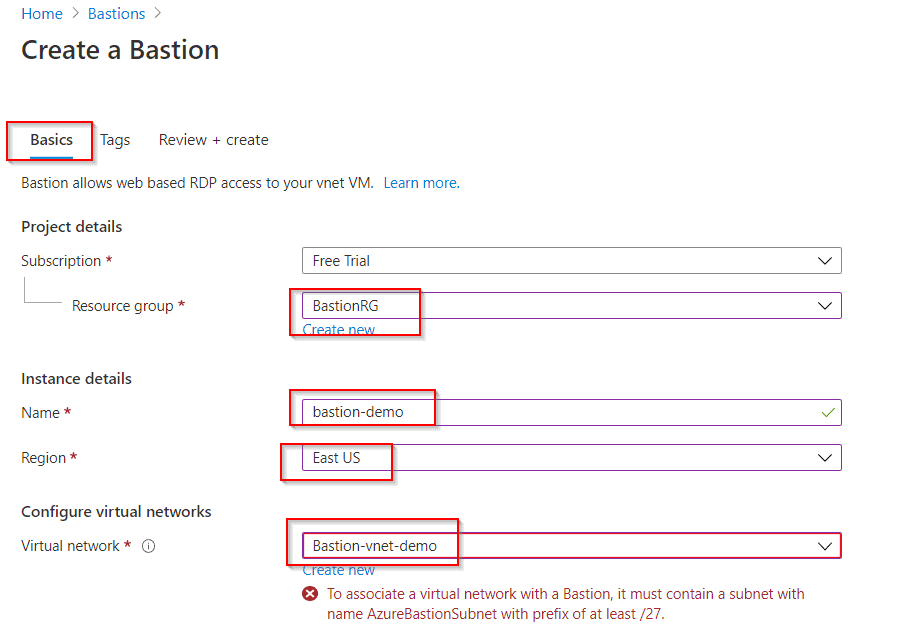
3. Once you reach the Subnet option, click on Manage Subnet Configuration.
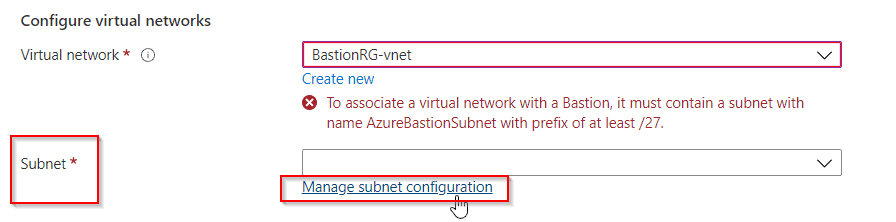
4. Now, click on Add Subnet and create a subnet with the name AzureBastionSubnet and a prefix of /27 or larger. Make sure you use this name only.
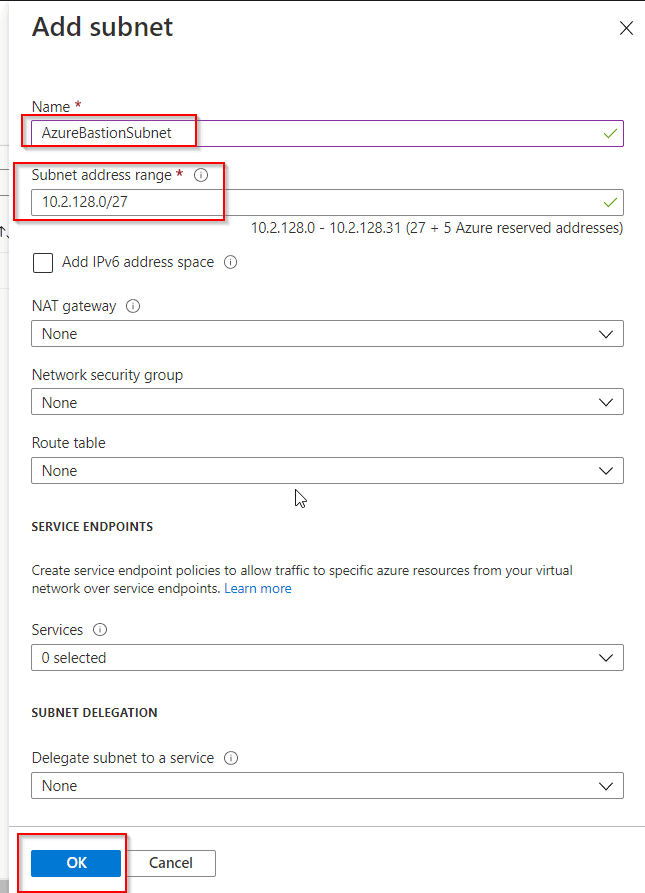
5. Head back over and select your Subnet on the Bastion creation page. Now you can opt to create a new Public IP address or use an existing one.
6. If you create a new one then provide a name and use Standard SKU.
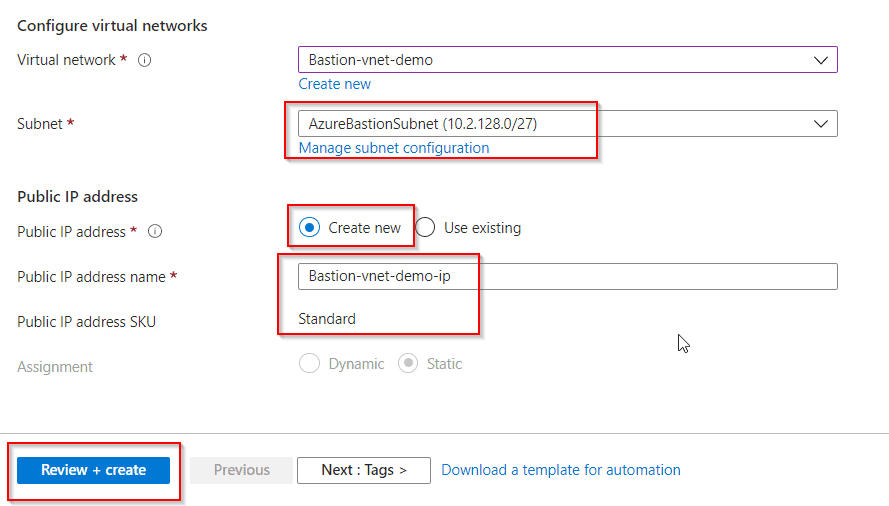
7. Then click on Review+Create. Then click on Create after validation passes.
Viola! Your Azure Bastion is ready.
Connect to the Virtual Machine
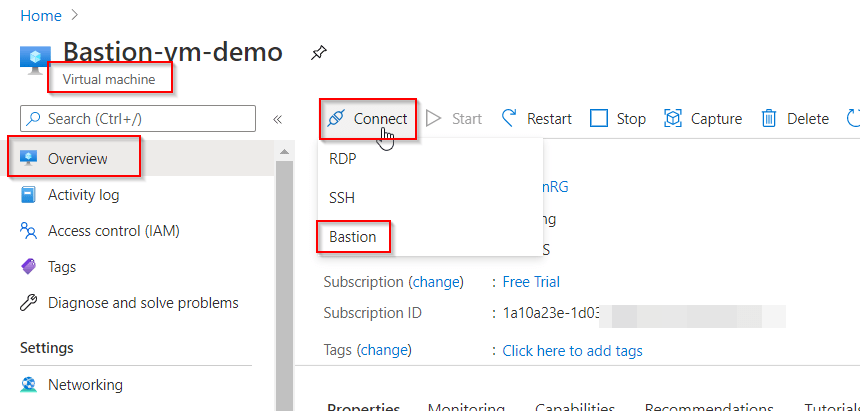
1. You can go to the Virtual Machines and select your newly created Bastion one and then click on Connect>Bastion, in the Overview section.
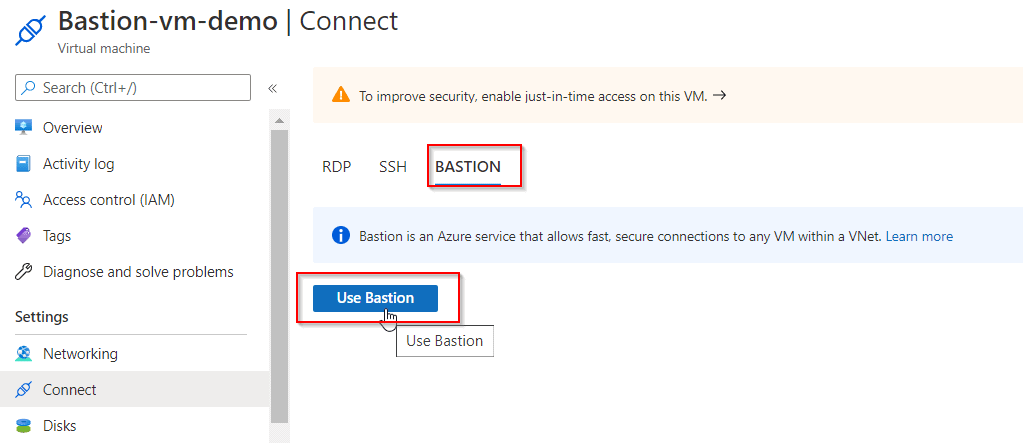
2. Now click on Use Bastion and enter your credentials.
You’re now logged in! Now a new browser window opens with the Virtual Machine on that tab.
Also, you can add NSGs to both your Bastion subnet as well as your VM subnets to further enhance security. Read the Azure documentation article “Working with NSG access and Azure Bastion” to get a leg up on which ports and protocols you need to allow to and from the Bastion subnet.

No comments:
Post a Comment