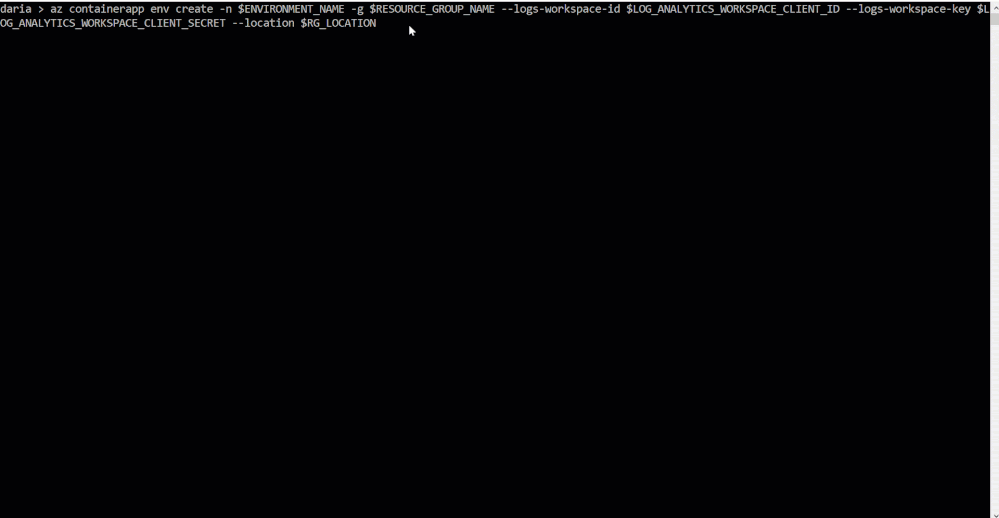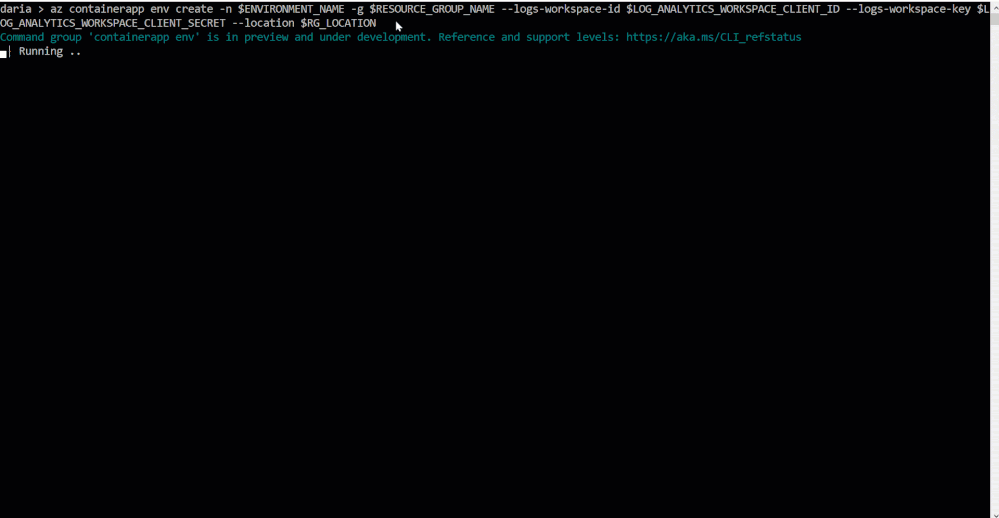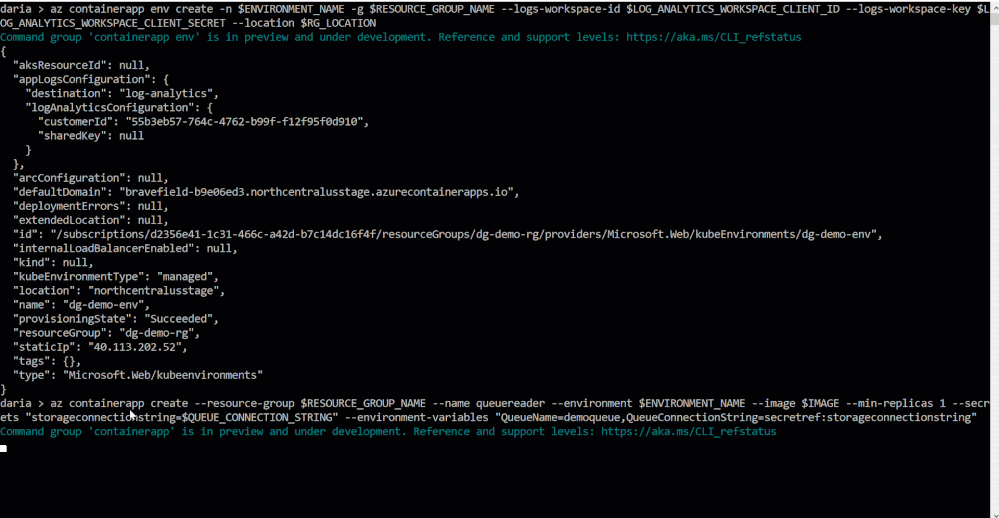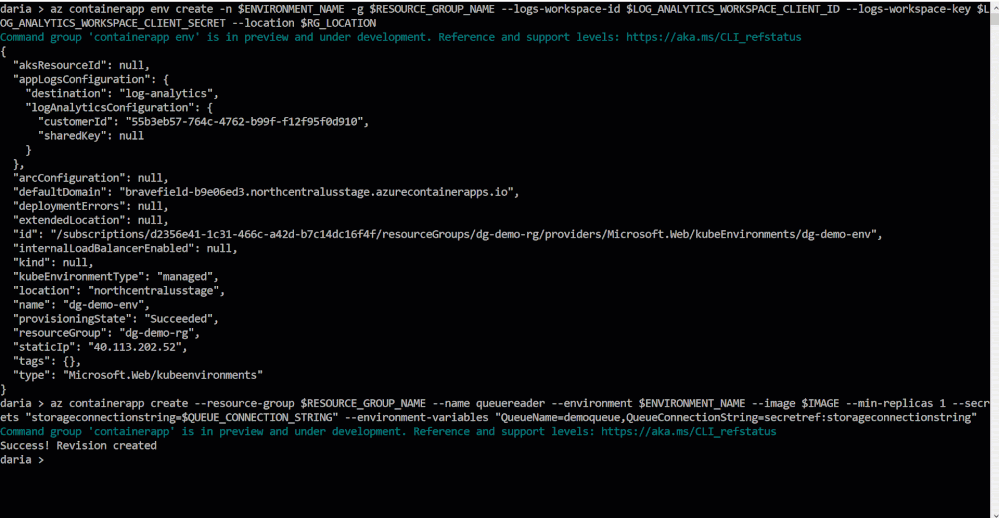
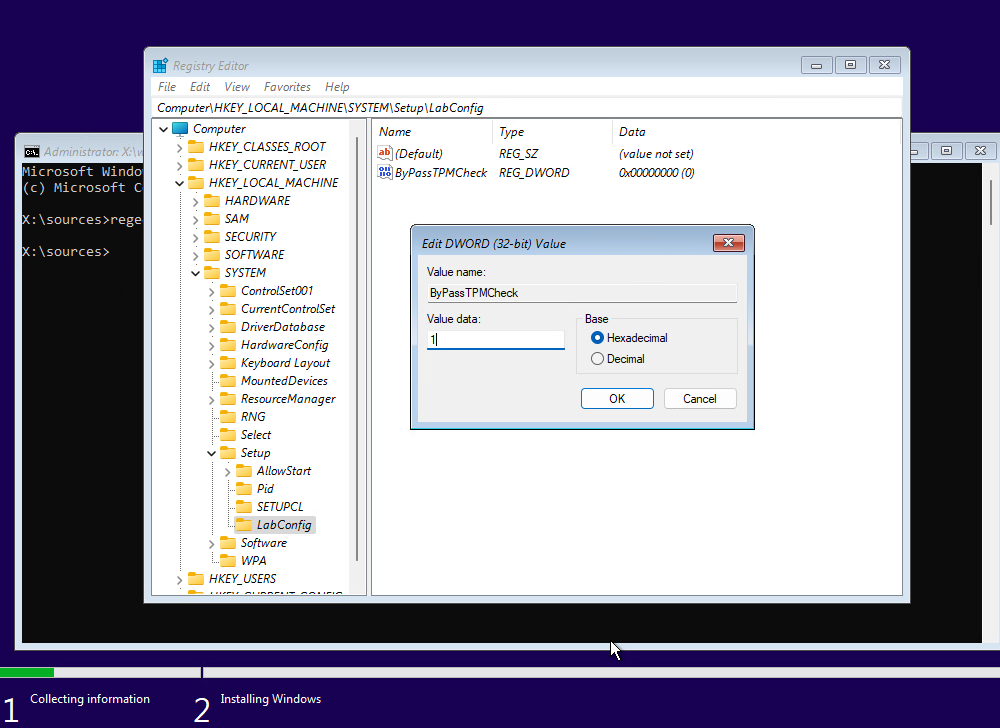
Create an Automator Config key
Open a command line interface and generate a 256-bit AES key in URL-encoded format using one of the methods below, depending on your operating system:
Generate a Key
Save the resulting value produced by this command for Step (3).
(2) Create a Container App
From Azure, create a new Container App.
Select or create a new Resource Group
Set the Container App Name to "keeperautomator" or whatever you prefer
Select the region where you would like the service hosted
Create a new Apps Environment or select an existing environment
Click
Next : Container >
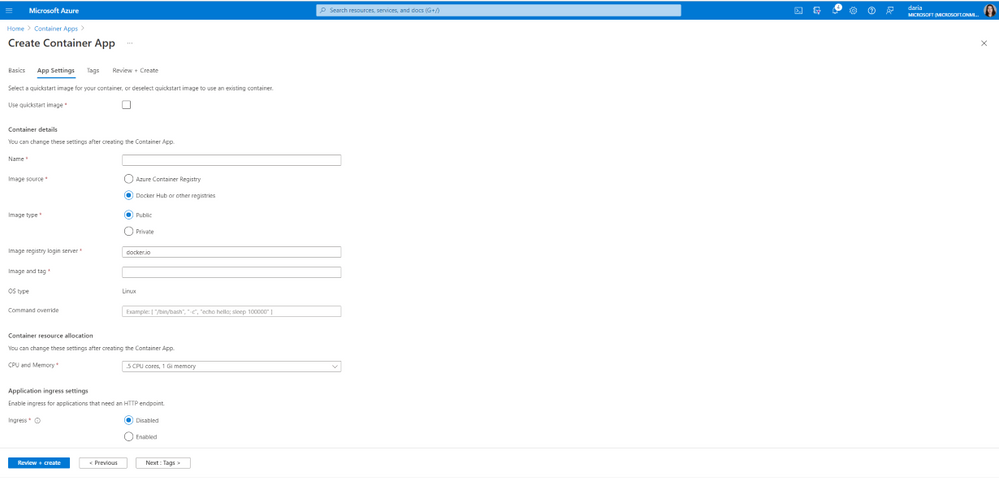
(3) Setup Container Details
In the "Container" step, make the following selections:
Uncheck the "Use quickstart image"
Select "Docker Hub or other registries"
Select "Public"
Select Registry login server as
docker.ioSet the Image and tag as
keeper/automator:latestFor CPU and Memory, 0.5 CPU cores and 1Gi memory is sufficient, but this can be updated based on your volume of new device logins.
Create an environment variable called
AUTOMATOR_CONFIG_KEYwith the value from Step 1 above of the setup guide.Create an environment variable called
AUTOMATOR_PORTwith the value of8089Create an environment variable called
SSL_MODEwith the value ofnoneClick "Next : Bindings >"
Click "Next : Ingress >"
(4) Ingress Setup
On the Ingress setup screen, select the following:
EnableIngressIngress traffic
Accepting traffic from anywhere(we'll modify this in a later step)Ingress type
HTTPTarget port set to
8089
(5) Create Container App
Click "Review + Create" and then click "Create"
After a few minutes, the container app will be created and automatically start up.
Clicking on "Go to Resource" will take you to the container environment.
(6) Customize the Ingress Setup
To restrict communications to the Keeper Automator service, click on the "Ingress" link on the left side of the screen.
Click on "Ingress"
Select "Allow traffic from IPs configured below, deny all other traffic"
Click "Add" to add two of Keeper's IPs and any of your IPs required for testing the service.
Click Save
(7) Set up Scaling, Health Probes and Volume Mount
In order to prevent Azure from downscaling to zero instances, it's important to set the minimum number of instances to 1.
Click on "Scale and replicas"
Click "Edit and deploy"
Click on the "Scale" tab
For now, let's set the Min / max both to 1.
Next, click on the "Container" tab, click on the container image name
Click on the "Health probes" tab on the upper right
Under "Liveness probes":
Enable liveness probes
Transport:
HTTPPath:
/healthPort:
8089Initial delay seconds:
5Period seconds:
30
Under "Startup probes":
Enable startup probes
Transport:
HTTPPath:
/healthPort:
8089Initial delay seconds:
5Period seconds:
30
Under "Volume Mounts":
Select "Ephemeral Storage"
Add volume name
automatordataAdd Mount Path as
/usr/mybin/config
Finish the configuration
Click on
SaveThen click on
Createto build the new configurationAfter a few minutes, the new containers should start up
(8) Retrieve the Application URL
From the Overview section of the Container App, on the right side is the "Application URL" that was assigned. Copy this and use this Application URL in the next step.
For example, https://craigautomator1.xyx-1234.azurecontainerapps.io
(9) Login to Keeper Commander
Keeper Commander is required to perform the final step of Automator configuration. This can be run from anywhere, it does not need to be installed on the server.
On your workstation or server, install Keeper Commander CLI. The installation instructions including binary installers are here:
https://docs.keeper.io/secrets-manager/commander-cli/commander-installation-setup
After Commander is installed, launch Keeper Commander, or from an existing terminal you can type keeper shell to open the session, then login using the login command. In order to set up Automator, you must login as a Keeper Administrator, or an Admin with the ability to manage the SSO node.
(10) Create the Automator
Create the Automator using a series of commands, starting with automator create
The Node Name (in this case "Azure Cloud") comes from the Admin Console UI as seen below.
The output of the command will display the Automator settings, including metadata from the identity provider.
Note that the "URL" is not populated yet. This is the Application URL from Step 8.
Run the "automator edit" command as displayed below, which sets the URL and also sets up the skills (team, team_for_user and device).
Next we exchange keys: The enterprise private key encrypted with the Automator public key is provided to Automator:
Initialize the Automator with the new configuration
Enable the service
At this point, the configuration is complete.
For external health checks, you can use the below URL:
https://<server>/health
Example curl command: