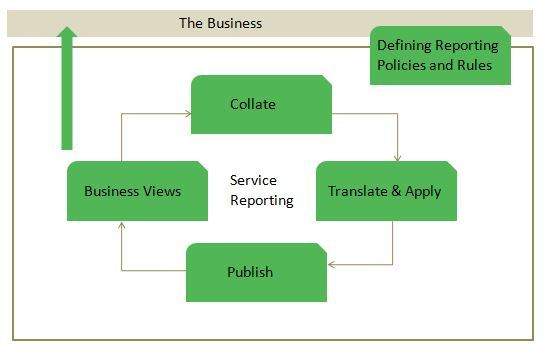
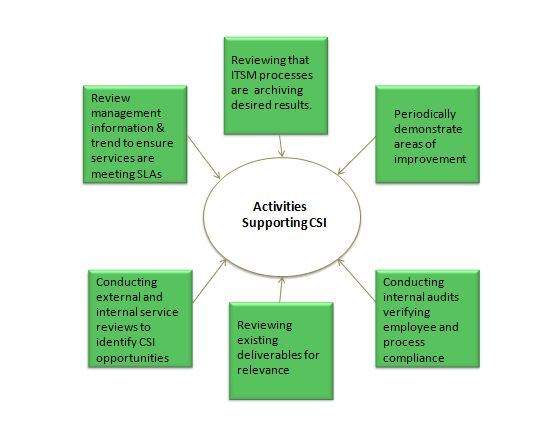
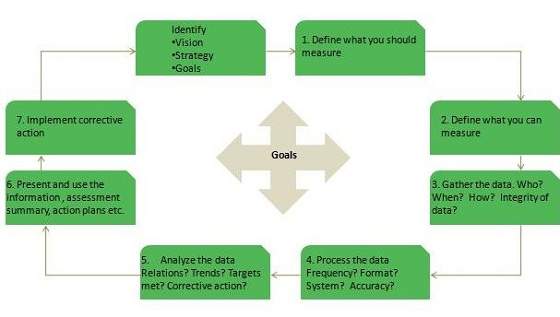
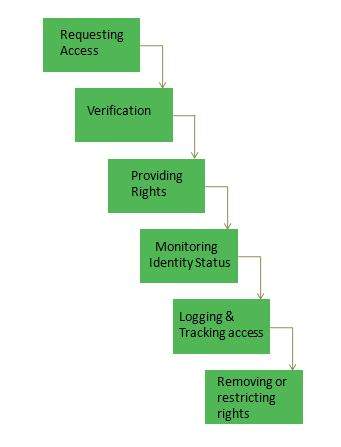
Que: Which process is responsible for ensuring that the CMDB has been updated correctly?
- Change Management
- Problem Management
- Configuration Management
- Release Management
Ans: C.
Que: Which of the following details must be recorded for every CI in the CMDB?
- Type identity
- Unique identifier
- Version number
- Copy number
Ans: Both A and B
Que: Items of information stored in the CMDB relating to a specific CI are known as?
- Components
- Features
- Characteristics
- Attributes
Ans: D.
Que: A Configuration Management Database (CMDB) can contain different Configuration Items (CIs). Which of the items below would NOT normally be regarded as a CI?
- A user name
- A video monitor
- A bought-in software package
- A procedure
Ans: A.
Que: For which of the following activities is the Service Desk NOT responsible?
- Impact analysis
- Root cause identification
- Categorisation and prioritisation
- Escalation
Ans: B.
Que: Which of the following is NOT part of the role of the Service Desk?
- Providing support to the user community
- Resolving the root causes of incidents
- Acting as day-to-day interface between IT services and users
- Monitoring the progress of incidents
Ans: B.
Que: The network managers have excessive workloads and have no time to proactively manage the network. One of the contributing factors to these large workloads is the frequency that users contact these managers directly. which ITIL process would improve this situation?
- Change Management
- Configuration Management
- Incident Management
- Problem Management
Ans: C.
Que: A computer operator notices the full storage capacity of her/his disk will soon be used. To which ITIL process must this situation be reported?
- Change Management
- Configuration Management
- Incident Management
- Problem Management
Ans: C.
Que: A serious incident has occurred. The assigned solution team is unable to resolve this incident within the agreed time. The Incident Manager is called in. Which form of escalation describes the above sequence of events?
- Formal escalation
- Functional escalation
- Hierarchical escalation
- Operational escalation
Ans: C.
Que: From which document can the Incident Management process obtain information about when and to whom it must escalate issues if required?
- The Service Improvement Program
- The Service Catalogue
- The organization chart
- The Service Level Agreement
Ans: D.
Que: Which of the following is NOT a Problem Management responsibility?
- Ownership of an incident throughout its lifecycle
- Investigation & Diagnosis
- Raising Requests for Change
- Maintenance of a known error database
Ans: A.
Que: A known error occurs when?
- An error has occurred several times and has been passed to Problem Management
- An error occurs that has not been diagnosed and for which a circumvention does not yet exist
- A problem has been diagnosed and a resolution or circumvention exists
- The resolution of a problem has been implemented
Ans: C.
Que: If a customer complains that service levels are below those agreed in the SLA because of a number of related hardware incidents, who is responsible for investigating the underlying cause?
- The Incident Manager
- The Service Level Manager
- The Problem Manager
- The Availability Manager
Ans: C.
Que: A user complains to the Service Desk that an error continually occurs when using a specific application. This causes the connection with the network to be broken. Which ITIL process is responsible for tracing the cause?
- Availability Management
- Incident Management
- Problem Management
- Release Management
Ans: C.
Que: How does Problem Management support the Service Desk activities?
- It resolves serious incidents for the Service Desk.
- It studies all incidents resolved by the Service Desk.
- It relieves the Service Desk by communicating the resolution directly to the user.
- It makes information on a Known Error available to the Service Desk.
Ans: D.
Que: Under an ITIL Change Management process, once a change has been built, who should undertake testing?
- The change builder
- The Change Manager
- The Change Advisory Board
- An independent tester
Ans: D.
Que: Which of the following activities is the responsibility of Change Management?
- Reviewing changes to ensure they have worked
- Creating a change to rectify a known error
- Determining the release strategy for a major change
- Implementing a software change at a remote site
Ans: A.
Que:Within an ITIL compliant Change Management process, who decides on the categorisation of a proposed change?
- Change Manager
- Change Advisory Board
- Change Requestor
- Change Implementer
Ans: A.
Que: The data in the Configuration Management Database (CMDB) can only be modified after permission is granted to modify the infrastructure. Which process grants such permission?
- Change Management
- Configuration Management
- Incident Management
- Service Level Management
Ans: A.
Que: After a Change has been implemented, an evaluation is performed.What is this evaluation called?
- Forward Schedule of Changes (FSC)
- Post Implementation Review (PIR)
- Service Improvement Program (SIP)
- Service Level Requirement (SLR)
Ans: B.
Que: Which of the following activities is NOT part of the release process?
- Moving software from the DSL to the development environment
- Moving software from the DSL to the live environment
- Moving software from the development to the test environment
- Moving software from the live environment to the DSL
Ans: A.
Que: Which of the following best describes ‘reliability’?
- The combination of confidentiality, integrity and maintainability
- The ability of a service to remain functional even though some components have failed
- The ability of a CI to remain functional under given conditions
- The ability of a CI to be retained in, or restored to, an operational state
Ans: C.
Que: What is the description of the term Confidentiality as part of the Security Management process?
- Protection of the data against unauthorized access and use
- Ability to access data at any moment
- The capacity to verify that the data is correct
- The correctness of the data
Ans: A.
Que: Which of the following is NOT a responsibility of the IT Service Continuity planning team?
- Outlining possible measures to protect an IT service
- Deciding the business criticality of an IT service
- Testing the plans for recovery of an IT service
- Identifying the risks to an IT service
Ans: B.
Que: Which of the following would you NOT expect to see in an IT Service Continuity Plan?
- Contact lists
- The version number
- Reference to change control procedures
- Service Level Agreements
Ans: D.
Que: Which of these is not part of Capacity Management?
- Tuning
- Demand Management
- Application sizing
- Maintainability
Ans: D.
Que: Which of the ITIL processes is responsible for ensuring the organisation is aware of new and changing technology?
- Capacity Management
- Change Management
- Financial Management for IT Services
- Configuration Management
Ans: A.
Que: Which ITIL process draws up a (long-range) plan for the expected purchase of IT Services?
- Capacity Management
- Change Management
- Financial Management for IT Services
- Configuration Management
Ans: A.
Que: The Service Level Manager requires confirmation that the internal Service Desk can answer a certain percentage of calls within 10 seconds. In which document would the Service Desk’s agreement to this requirement be recorded?
- Internal Specification Sheet
- Operational Level Agreement
- Service Level Agreement
- An underpinning third party contract
Ans: B.
Que: In which two service Management processes would you be most likely to use a risk analysis and management methodology?
- Change & Cost Management
- Availability Management & IT Service Continuity Management
- Incident & Change Management
- Service Level Management & IT Service Continuity Management
Ans: B.