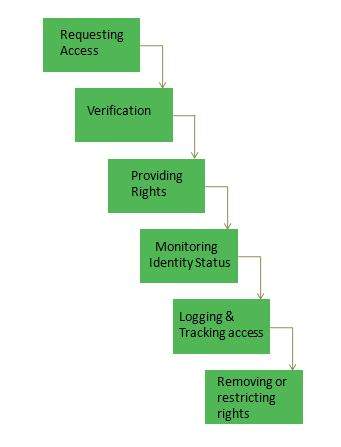
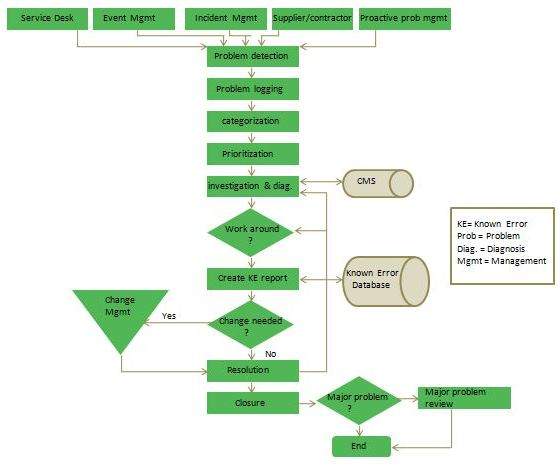
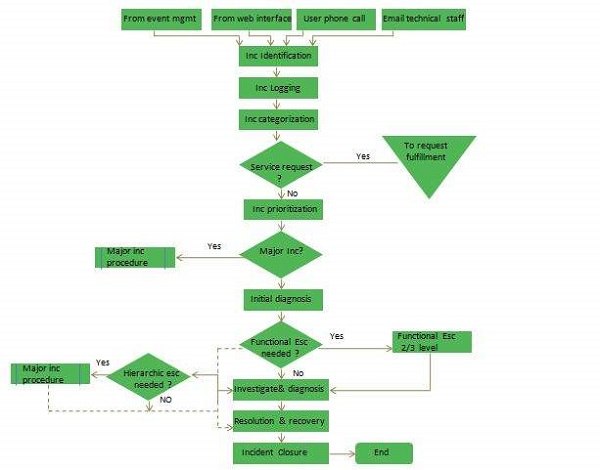
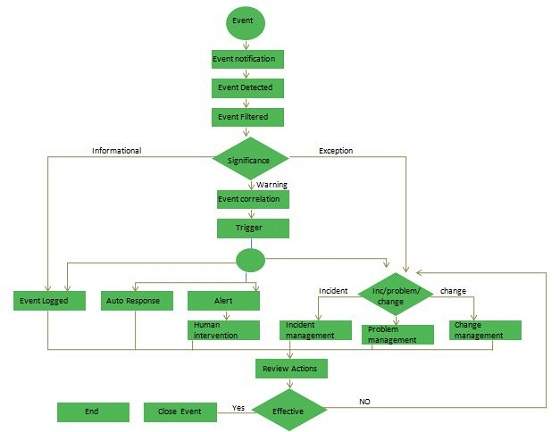
Continuous Service Improvement (CSI) deals with measures to be taken to improve the quality of services by learning from past successes and failures. Its purpose is to align and realign IT Services to the changing needs by identifying and implementing improvements to the changing business needs.
Objectives
Here are the serveral objectives of Continual Service Improvement −
- Review and analyze improvement opportunities in each lifecycle phase
- Review and analyze Service Level achievement results
- Improve cost effectiveness of delivering IT services without sacrificing customer satisfaction
- Identify and implement individual activities to improve IT service quality
- Ensures applicable quality management methods are used to support continual improvement activities
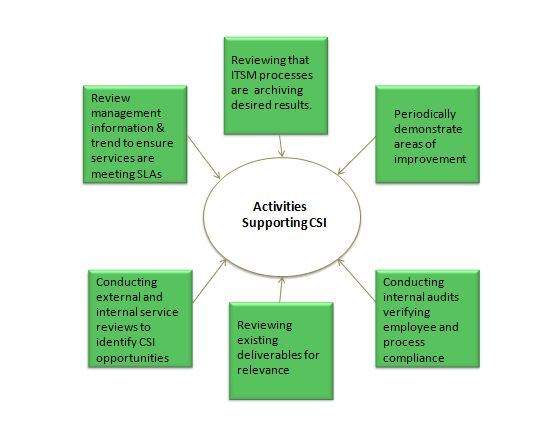
Activities Supporting CSI
The activities that support CSI do not happen automatically and thus required to be owned within IT organization which is capable of handling the responsibilities and processes the appropriate authority to make things happen. Here are the activities supporting Continual Service Improvement.
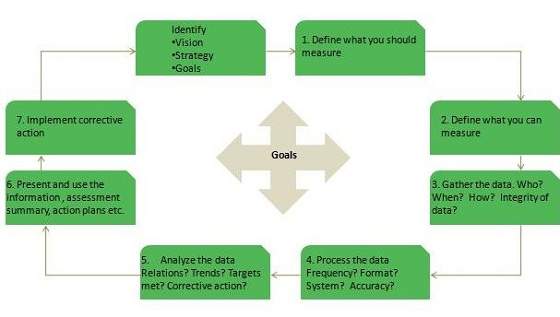
CSI Process Model
The steps involved in CSI are self explanatory as described in the following diagram
Perspectives of Benefits
Here are the four perspectives of benefits that are taken into consideration while discussing outcomes of CSI −
Improvement
This is comparison of result of current state of service to previous.
Benefits
It is the gain achieved through realization of improvements.
Return on Investment
It is the difference between benefits and amount expanded to achieve that benefit.
Value on Investment
It is the extra value created by establishment of benefits that include non-monetary or long-term outcomes.