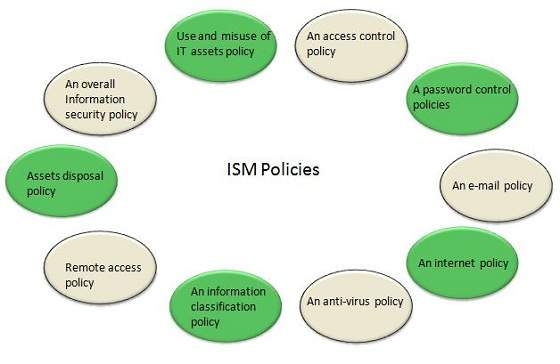
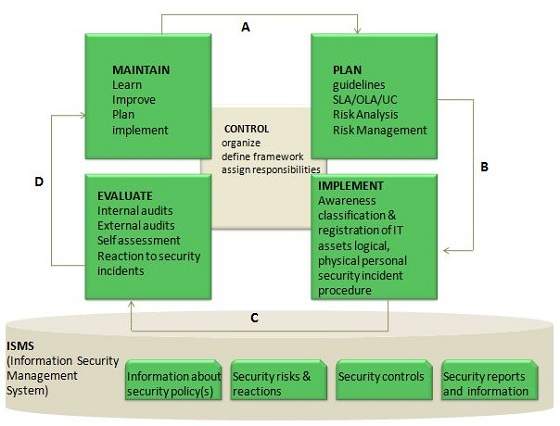
Overview
Assets
Asset is something that has financial value with a depreciation rate attached to it. It has a cost and organization uses it for its asset value calculation.
It doesn’t have direct impact on delivering services. Anything such as servers, buildings, blackberries, switches, routers etc. comes under assets.
Configuration Items (CIs)
Configuration item is subset of service assets and have direct impact on delivering services. All servers, networks, applications that have impact on production are known as configuration item.
Building is an asset but not CI. Document is a CI not an asset.
Hence Service Assets and Configuration Management (SACM) deals with maintaining up-to-date and verified database of all assets and CIs which are also made available to other service management processes.
- Configuration Manager is the process owner of this process.
- SACM uses Configuration Management System (CMS) which contains one or more Configuration Management Databases (CMDB).
CIs Types
CIs are categorized into six as shown in the following diagram −
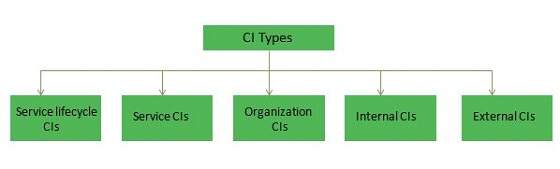
Service Lifecycle CIs
Service lifecycle CIs gives clear picture on:
- Services
- How services will be delivered?
- What benefits are expected?
- Service cost
Service CIs
Service CIs refers to −
- Service model
- Service package
- Release package
- Service resource assets
- Service capability assets
Organization CIs
Organization CIs are internal to an organization but independent of the service provider.
Internal CIs
CIs which are delivered by individual projects are known as Internal CIs.
External CIs
External CIs refer to external customer requirements and agreements, releases from supplier and external services.
Interface CIs
These CIs are required to deliver end-to-end service across a Service Provider Interface (SPI).
Configuration Management System (CMS)
SACM uses Configuration Management System (CMS) which contains one or more Configuration Management Databases (CMDB). The database contains information associated with a CI such as supplier, cost, purchase date, renewal date for licenses and maintenance contracts and other related documents such as SLA etc.
There are also other attributes for Configuration Items such as −
- Unique Identifier
- CI type
- Name/description
- Supply date
- Location
- Status
- License details
- Related document masters
- Related software masters
- Historical data
- Relationship type
- Application SLA
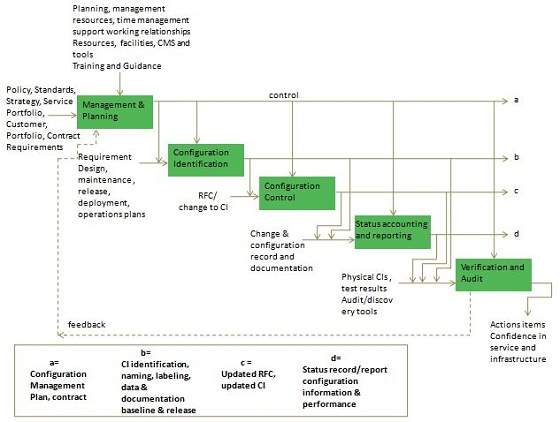
- Service Assets and Configuration Process
SACM process comprises of following five activities −
- Management and Planning
- Configuration identification
- Configuration control
- Status accounting and reporting
- Verification and Audit
All of the above mentioned activities are described in the following diagram −