Configure network access for Azure Elastic SAN
You can control access to your Azure Elastic storage area network (SAN) volumes. Controlling access allows you to secure your data and meet the needs of your applications and enterprise environments.
This article describes how to configure your Elastic SAN to allow access from your Azure virtual network infrastructure.
To configure network access to your Elastic SAN:
Prerequisites
- If you're using Azure PowerShell, install the latest Azure PowerShell module.
- If you're using Azure CLI, install the latest version.
- Once you've installed the latest version, run
az extension add -n elastic-santo install the extension for Elastic SAN. There are no extra registration steps required.
Limitations
The following list contains the regions Elastic SAN is currently available in, and which regions support both zone-redundant storage (ZRS) and locally redundant storage (LRS), or only LRS:
- South Africa North - LRS
- East Asia - LRS
- Southeast Asia - LRS
- Brazil South - LRS
- Canada Central - LRS
- France Central - LRS & ZRS
- Germany West Central - LRS
- Australia East - LRS
- North Europe - LRS & ZRS
- West Europe - LRS & ZRS
- UK South - LRS
- Japan East - LRS
- Korea Central - LRS
- Central US - LRS
- East US - LRS
- South Central US - LRS
- East US 2 - LRS
- West US 2 - LRS & ZRS
- West US 3 - LRS
- Sweden Central - LRS
- Switzerland North - LRS
Configure public network access
You enable public Internet access to your Elastic SAN endpoints at the SAN level. Enabling public network access for an Elastic SAN allows you to configure public access to individual volume groups over storage service endpoints. By default, public access to individual volume groups is denied even if you allow it at the SAN level. You must explicitly configure your volume groups to permit access from specific IP address ranges and virtual network subnets.
You can enable public network access when you create an elastic SAN, or enable it for an existing SAN using the Azure PowerShell module or the Azure CLI.
Use the Azure PowerShell module or the Azure CLI to enable public network access.
Configure a virtual network endpoint
You can configure your Elastic SAN volume groups to allow access only from endpoints on specific virtual network subnets. The allowed subnets can belong to virtual networks in the same subscription, or those in a different subscription, including a subscription belonging to a different Microsoft Entra tenant.
You can allow access to your Elastic SAN volume group from two types of Azure virtual network endpoints:
A private endpoint uses one or more private IP addresses from your virtual network subnet to access an Elastic SAN volume group over the Microsoft backbone network. With a private endpoint, traffic between your virtual network and the volume group are secured over a private link.
Virtual network service endpoints are public and accessible via the internet. You can Configure virtual network rules to control access to your volume group when using storage service endpoints.
Network rules only apply to the public endpoints of a volume group, not private endpoints. The process of approving the creation of a private endpoint grants implicit access to traffic from the subnet that hosts the private endpoint. You can use Network Policies to control traffic over private endpoints if you want to refine access rules. If you want to use private endpoints exclusively, don't enable service endpoints for the volume group.
To decide which type of endpoint works best for you, see Compare Private Endpoints and Service Endpoints.
Once network access is configured for a volume group, the configuration is inherited by all volumes belonging to the group.
The process for enabling each type of endpoint follows:
Configure a private endpoint
Important
- For Elastic SANs using locally-redundant storage (LRS) as their redundancy option, private endpoints are supported in all regions where Elastic SAN is available. Private endpoints aren't currently supported for elastic SANs using zone-redundant storage (ZRS) as their redundancy option.
There are two steps involved in configuring a private endpoint connection:
- Creating the endpoint and the associated connection.
- Approving the connection.
You can also use Network Policies to refine access control over private endpoints.
To create a private endpoint for an Elastic SAN volume group, you must have the Elastic SAN Volume Group Owner role. To approve a new private endpoint connection, you must have permission to the Azure resource provider operation Microsoft.ElasticSan/elasticSans/PrivateEndpointConnectionsApproval/action. Permission for this operation is included in the Elastic SAN Network Admin role, but it can also be granted via a custom Azure role.
If you create the endpoint from a user account that has all of the necessary roles and permissions required for creation and approval, the process can be completed in one step. If not, it requires two separate steps by two different users.
The Elastic SAN and the virtual network could be in different resource groups, regions, and subscriptions, including subscriptions that belong to different Microsoft Entra tenants. In these examples, we're creating the private endpoint in the same resource group as the virtual network.
You can create a private endpoint connection to your volume group in the Azure portal either when you create a volume group or when modifying an existing volume group. You need an existing virtual network to create a private endpoint.
When creating or modifying a volume group, select Networking, then select + Create a private endpoint under Private endpoint connections.
Fill out the values in the menu that pops up, select the virtual network and the subnet that your applications will use to connect. When you're done, select Add, and Save.
Configure an Azure Storage service endpoint
To configure an Azure Storage service endpoint from the virtual network where access is required, you must have permission to the Microsoft.Network/virtualNetworks/subnets/joinViaServiceEndpoint/action Azure resource provider operation via a custom Azure role to configure a service endpoint.
Virtual network service endpoints are public and accessible via the internet. You can Configure virtual network rules to control access to your volume group when using storage service endpoints.
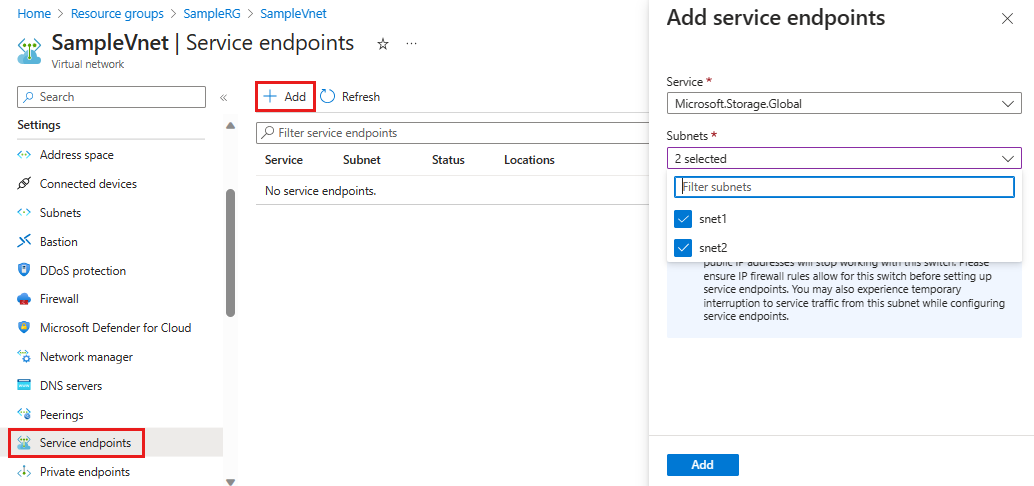
Navigate to your virtual network and select Service Endpoints.
Select + Add.
On the Add service endpoints screen:
- For Service select Microsoft.Storage.Global to add a cross-region service endpoint.
For Subnets select all the subnets where you want to allow access.
Select Add.
Configure virtual network rules
All incoming requests for data over a service endpoint are blocked by default. Only applications that request data from allowed sources that you configure in your network rules are able to access your data.
You can manage virtual network rules for volume groups through the Azure portal, PowerShell, or CLI.


No comments:
Post a Comment