Network Security
Azure provides various protection methods for securing a service in a network. I have listed down some of the basic network security tools with a short description.
Network Security Group (NSG)
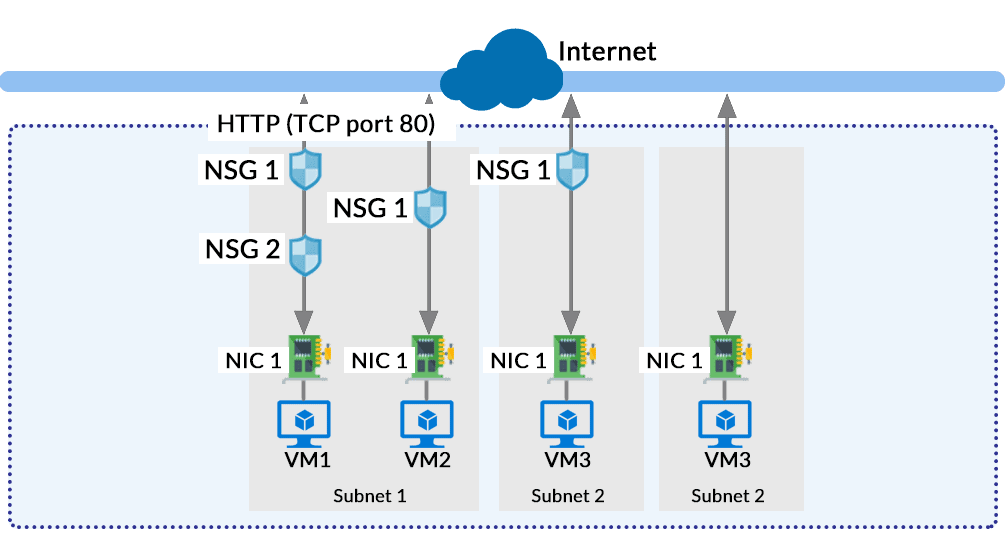
The Network Security Group in Azure acts like a firewall at the network level. It filters the traffic passing through Azure Resources in a virtual network. NSG is a group of security rules that defines the priority, source or destination, protocol, direction, port range and action. Using these rules, NSG allows or deny inbound and outbound traffic. The rules for entering traffic inside a resource is also called ‘Ingress‘, and the rules for exiting the traffic or going out of the resource is called ‘Egress‘. When all the rules are created, the NSG can be used in a Virtual Machine that will interact with a network.
Service Endpoints
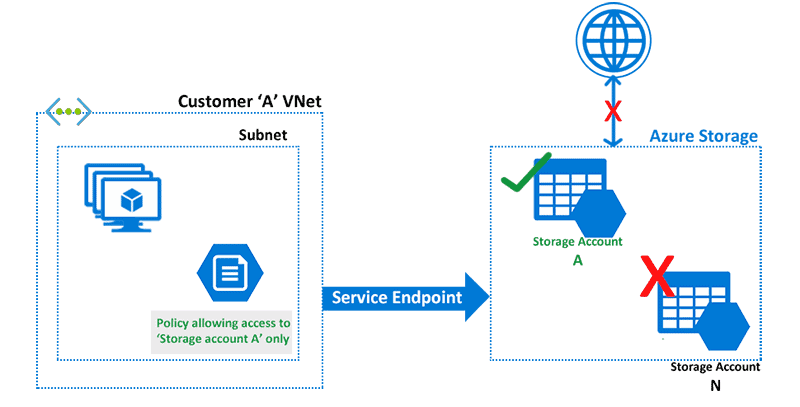
Service Endpoints in Azure provides secure connectivity over the optimized route of the Azure Network. Without needing a public IP address, Service Endpoints allows Private IP address in a VNet to reach the endpoint of an Azure Service. It is simple to set up and improves security for the Azure resources in a network. The services here can be Azure Storage, Azure Database, etc.
Web Application Firewall (WAF)
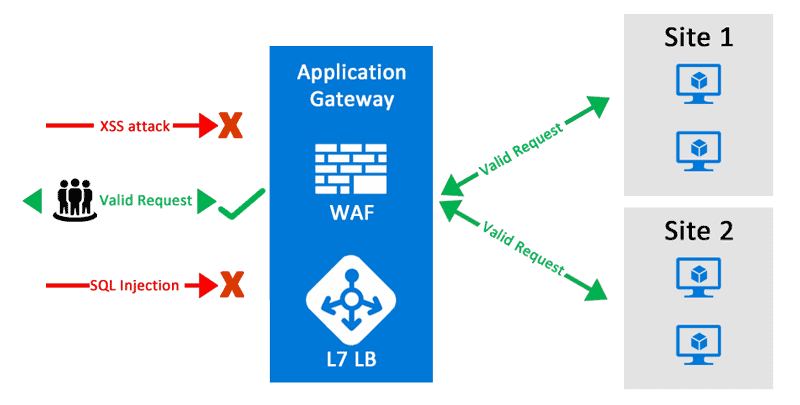
Web applications are a common target for hackers to steal user information. So, protection from the most common attacks like SQL injection, cross-site scripting, etc., is a must. Web Application Firewall by Azure is a firewall for protecting the web application from these common threats. It provides an easy setup for applying various protection of layers that results in better security management. A user can deploy the WAF with other services like Azure Application Gateway, Azure Content Delivery Network (CDN) and Azure Front Door.

No comments:
Post a Comment