As an organization, you need to adopt a business continuity and disaster recovery (BCDR) strategy that keeps your data safe and your apps and workloads online when planned and unplanned outages occur.
Site Recovery helps ensure business continuity by keeping business apps and workloads running during outages. Site Recovery replicates workloads running on physical and virtual machines (VMs) from a primary site to a secondary location.
What is Windows Active Directory?
Active Directory (AD): Active Directory is a database and a set of services connecting users with the network resources required by them to get their work done. The database (or directory) has critical information related to your IT environment, including what users and computers there are and who’s allowed to do what. The services control most of the activity going on in your IT environment so basically, Windows AD provides authentication and authorization to applications, file services, and other resources in a network.
What is Azure Active Directory?
Azure Active Directory (AAD): If we want to manage access to the Azure Cloud application and associated resources then we need Azure AD. This helps your employees to access external resources, such as Azure services, Azure portal, And other applications.
Azure AD is a Microsoft cloud-based identity and access management service, which helps your employees sign in and access resources in:
1) External resources, such as Microsoft Office 365, the Azure portal, and thousands of other SaaS applications.
2) Internal resources, such as apps on your corporate network and intranet, along with any cloud apps developed by your own organization.
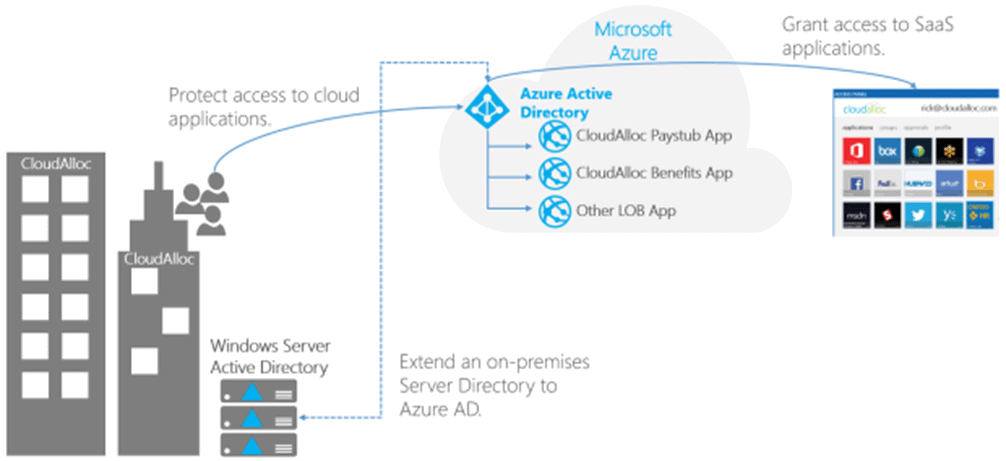
If we have a traditional on-premise set up with AD and want to integrate it with Azure AD so that we can manage access to the Cloud application, we can do it easily by using AD Connect.
In layman’s terms, the Azure Active Directory is not an extension of an on-premises directory. Rather, it’s a copy that contains the same objects and identities.
How Does Azure Active Directory Work?
Azure AD a cloud-based service for identity and access management that falls into the identity as a service (IDaaS) category, is a secure online authentication store for both individual user profiles and groups of user profiles.
It manages access through user accounts, which have a username and a password. Users can be organized into different groups, which can have different access privileges for individual applications. Identities from Microsoft or third-party software as a service (SaaS) can also be created for cloud applications to grant user access through.
To connect users to SaaS applications, Azure Active Directory uses SSO which allows each user to access the full suite of applications they have permission for, without having to repeatedly log in each time. It creates access tokens (that may be created with expiry dates) that are stored locally on employee devices.
Windows AD vs. Azure AD
| Concept | Windows Active Directory | Azure Active Directory |
|---|---|---|
| Provisioning Users | Organizations create internal users manually or use an in-house or automated provisioning system, like the Microsoft Identity Manager, to integrate with an HR system. | Existing AD organizations use Azure AD Connect to sync identities to the cloud. It adds support to automatically create users from cloud HR systems and provision identities in SCIM-enabled SaaS apps to automatically provide apps with the necessary details to allow access for users. |
| Admin Management (AKS) | Organizations will use a combination of domains, organizational units, and groups in AD to delegate administrative rights to manage the directory monitored resources. | Azure AD provides built-in roles with its Azure AD RBAC system, with limited support for creating custom roles to delegate privileged access to the identity system, the apps, and the resources it controls. |
| Infrastructure Apps | Active Directory forms the basis for many infrastructure on-premises components, like DNS, DHCP, IPSec, WiFi, NPS, and VPN access | In a new cloud world, Azure AD is the new control plane for accessing apps and relying on networking controls. When users authenticate, Conditional access (CA) controls which users have access to which apps under required conditions. |
| Traditional and legacy apps | Most on-premises apps use LDAP, Windows-Integrated Authentication (NTLM and Kerberos), or Header-based authentication to control access to users | Azure AD can provide access to these types of on-premises apps using Azure AD application proxy agents running on-premises. With this method, Azure AD can authenticate Active Directory users on-premises using Kerberos while you migrate or need to coexist with legacy apps. |
| Mobile | Active Directory doesn’t natively support mobile devices without third-party solutions. | Microsoft Intune (mobile device management solution) is integrated with Azure AD. It provides device state information to the identity system to evaluate during authentication. |
| Windows desktops | Active Directory provides the ability to domain join Windows devices to manage them using Group Policy, System Center Configuration Manager, or other third-party solutions. | Windows devices can be joined to Azure AD. Conditional access can check if a device is Azure AD joined as part of the authentication process. Windows devices can also be managed with Microsoft Intune wherein conditional access will consider whether a device is compliant (up-to-date security patches and virus signatures) before allowing access to the apps. |
Azure AD Concepts
1) Identity: Anything that can be authenticated. It can be a user with a username & password, applications, or other services that require authentication.
2) Account: Identity with data associated.
3) Azure AD Account: Identity created using Azure AD or other Microsoft cloud services.
4) Azure Tenant: An Instance of Azure AD is created when an organization signs up for a Microsoft Cloud service subscription.
5) Azure AD Directory: Each Azure Tenant has a dedicated and trusted Azure AD Directory.
6) User Subscription: To pay for Azure cloud services used.
Benefits Of Azure Active Directory
- Azure AD is highly available and spread across 32 datacentres in different geographies.
- Using Azure AD access to applications on cloud or on-premise can be simplified.
- Single Sign-On to access thousands of SaaS applications & On-premise applications.
- Multi-Factor Authentication, Conditional Access, Privileged Identity Management, and Dynamic Group.
Azure AD Features & Licensing
Azure AD works on licensing model. You can access Azure AD with these two licenses:
- Microsoft Online Services
- Azure AD Premium Licenses
If you have Office 365 or Microsoft Azure license, then you will get all the non-paid Azure features, otherwise, you can get Azure premium features through Power BI premium licenses:
- Premium P1
- Premium P2 licenses
Features of Azure AD
- Application Management: It Manages your cloud and on-premises apps using services like Application Proxy, the My Apps portal, single sign-on, and Software as a Service (SaaS) apps.
- Authentication: Users can manage Azure AD self-service password reset feature, Multi-Factor Authentication, custom banned password list, and smart lockout.
- Azure Active Directory for developers: It builds apps that can sign in all the Microsoft identities, and fetch tokens to call Microsoft Graph, and other Microsoft or custom APIs
- Business-to-Business: You can manage your guest users and external partners while also maintaining control over your own corporate data at the same time.
- Business-to-Customer (B2C): With Azure AD users can customize and control how others sign up, sign in, and manage their profiles when using their apps.
- Managed identities for Azure resources: Provide your Azure services with an automatically managed identity in Azure AD that can authenticate any Azure AD-supported authentication service, including Key Vault.
- Reports and monitoring: Users can gain insights into the security and usage patterns in their working environment.
- Privileged identity management (PIM): This feature includes access to resources in Azure AD and Azure, including some other Microsoft Online Services, like Microsoft 365 or Intune. Users can manage, control, and monitor access within their organization.
- Identity protection: Detect potential vulnerabilities affecting your organization’s identities, configure policies to respond to suspicious actions, and accordingly take appropriate steps to resolve them.
- Identity governance: Manage your organization’s identity through employee, business partner, vendor, service, and app access controls.
- Enterprise users: Manage license assignments, app access, and setting up delegates using groups and administrator roles.
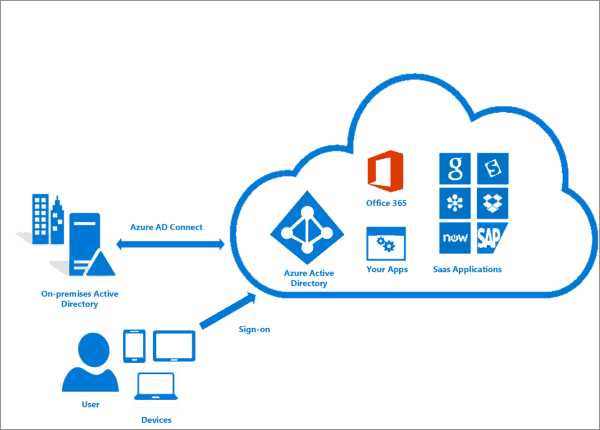
Azure AD Connect
It is used to integrate the on-premise directories (Active Directories) with Azure Active Directory which provides a common identity for accessing both cloud and on-premise resources.
There are various features of Azure AD Connect:
1) Password Hash Synchronization: Sign-in method that synchronizes a hashed user on-premised AD password with Azure AD.
2) Pass-through authentication: Sign-in method that provides access to users to use the same password on-premise and on the cloud.
3) Synchronization: Responsible for creating users, groups, and other objects and also validate if the identity information of your on-premise users and groups match with the cloud.
4) Health Monitoring: A central place to view the activity and also provide monitoring.
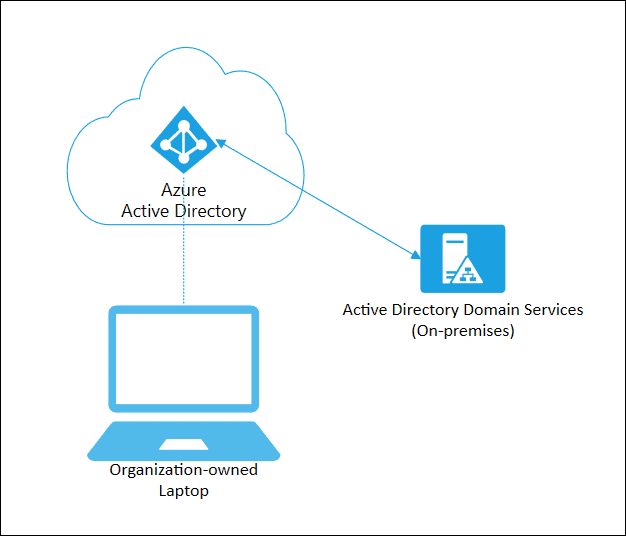
Azure AD Join
- Azure AD join is used to connect devices directly to Azure AD and we need not join to the on-premises AD.
- Azure AD joined devices are signed in for using an organizational Azure AD Account
- Devices that are Azure AD joined can still authenticate to on-premises servers like file, print, and other applications.
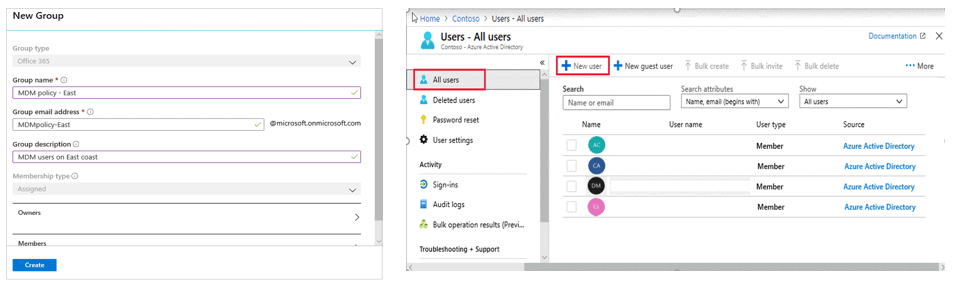
Creating And Managing Users & Groups In Azure AD
There are many ways to add users and groups to Azure Active Direct.
- By syncing from an on-premises Windows Server AD using AAD Sync. This is how most enterprise customers will get their users added to the directory and requires some additional server configuration on-premises to setup.
- Manually using the Azure Management Portal.
- Using PowerShell and the Azure Active Directory cmdlets
- Programmatically using the Azure AD Graph API. This is an extremely powerful option that essentially gives you full control of how users are added to the directory.
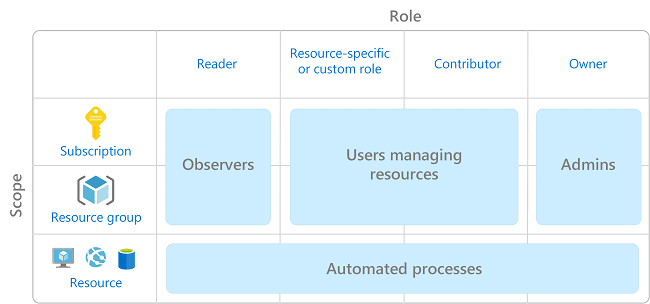
Access To Azure Resources
It is a very difficult and important task for any organization to manage access to Azure resources.
- Role-based access control (RBAC) helps you manage who has access to Azure resources, what they can do with those resources, and what areas they have access to.
- RBAC is an authorization system built on Azure Resource Manager that provides fine-grained access management of Azure resources.
- We can segregate duties and the amount of access to the users in a team that they need to perform their tasks using RBAC.
- It’s a best practice to grant users the least privilege to get their work done.
Conclusion
Azure AD is not simply a cloud version of AD, they do many different things. AD is great at managing traditional on-premise infrastructure and applications while Azure AD is great at managing user access to cloud applications. You can use both together, or if you want to have an experience of a purely cloud-based environment you can just use Azure AD. And it mostly depends on your need of service that for which you want to go and we have already discussed the difference between their services.

No comments:
Post a Comment