AWS DynamoDB :
Amazon DynamoDB is a fully-managed (“serverless”) and NoSQL (nonrelational) database service, available on Amazon Web Services. DynamoDB is highly scalable, meaning you can start really small and grow very big without needing to re-deploy or re-architect. It also offers a flexible model which uses automatic scaling of throughput capacity, this means that it scales compute capacity based on demand, saving money and lowering entry costs. This makes it a great fit for mobile, gaming, IoT, and other high-growth and high-volume applications.
The Amazon DynamoDB Advantage
Amazon DynamoDB offers multiple advantages over other NoSQL database management systems such as Apache Cassandra and MongoDB. The integration between DynamoDB and other AWS services is especially beneficial. If you are already an AWS user, it’s a great choice.
SIMPLE SET-UP
As a serverless database service, setting up is easy. Simply open the AWS Management Console and utilize the wizard. Conversely, in order to set up an on-premises MongoDB instance, you need to follow a long list of instructions and may have to resolve authentication errors.
AWS SECURITY
Security for DynamoDB is governed by AWS Identity and Access Management (IAM). You can also use other AWS security features to enhance the controls. Although MongoDB is secure, there have been security breaches in the past due to improper configuration and management.
AMAZON DYNAMODB ACCELERATOR (DAX)
DAX is a fully managed, secure, and scalable DynamoDB cache service. It is suitable for read-intensive workloads and provides major improvements in DynamoDB’s response time. DAX clusters are hosted by and run in Amazon Virtual Private Cloud (Amazon VPC). A DAX client should be installed on the Amazon EC2 instance hosting your application in VPC. All requests are routed via the DAX client, which fetches data, if available, from the DAX cluster (a cache hit).
If data is not available in the cluster, it will be extracted from DynamoDB (a cache miss). Results will be provided to your application via the DAX cluster. Caching data in DAX clusters reduces overall read requests on DynamoDB tables, which can save you money. Companies such as Tinder, Expedia, and Genesys all use DAX to enhance the customer experience by providing sub-millisecond response times to customer queries.
DynamoDB Auto Scaling
- When you use the AWS Management Console to create a new table, DynamoDB auto scaling is enabled for that table by default.
- Uses the AWS Application Auto Scaling service to dynamically adjust provisioned throughput capacity on your behalf, in response to actual traffic patterns.
- You create a scaling policy for a table or a global secondary index. The scaling policy specifies whether you want to scale read capacity or write capacity (or both), and the minimum and maximum provisioned capacity unit settings for the table or index. The scaling policy also contains a target utilization, which is the percentage of consumed provisioned throughput at a point in time.
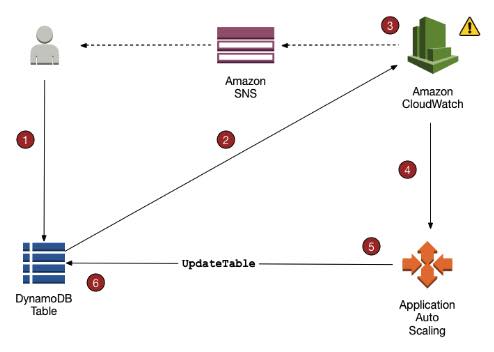
- DynamoDB auto scaling doesn’t prevent you from manually modifying provisioned throughput settings.
- If you enable DynamoDB auto scaling for a table that has one or more global secondary indexes, AWS highly recommends that you also apply auto scaling uniformly to those indexes.
Security
- Encryption
- Encrypts your data at rest using an AWS Key Management Service (AWS KMS) managed encryption key for DynamoDB.
- Encryption at rest can be enabled only when you are creating a new DynamoDB table.
- After encryption at rest is enabled, it can’t be disabled.
- Uses AES-256 encryption.
- The following are encrypted:
- DynamoDB base tables
- Local secondary indexes
- Global secondary indexes
- Authentication and Access Control
- Access to DynamoDB requires credentials.
- Aside from valid credentials, you also need to have permissions to create or access DynamoDB resources.
- Types of Identities
- AWS account root user
- IAM user
- IAM role
- You can create indexes and streams only in the context of an existing DynamoDB table, referred to as subresources.
- Resources and subresources have unique Amazon Resource Names (ARNs) associated with them.
- A permissions policy describes who has access to what.
- Identity-based Policies
- Attach a permissions policy to a user or a group in your account
- Attach a permissions policy to a role (grant cross-account permissions)
- Identity-based Policies
- Policy Elements
- Resource – use an ARN to identify the resource that the policy applies to.
- Action – use action keywords to identify resource operations that you want to allow or deny.
- Effect – specify the effect, either allow or deny, when the user requests the specific action.
- Principal – the user that the policy is attached to is the implicit principal.
- Policy Elements
- Web Identity Federation – Customers can sign in to an identity provider and then obtain temporary security credentials from AWS Security Token Service (AWS STS).

No comments:
Post a Comment