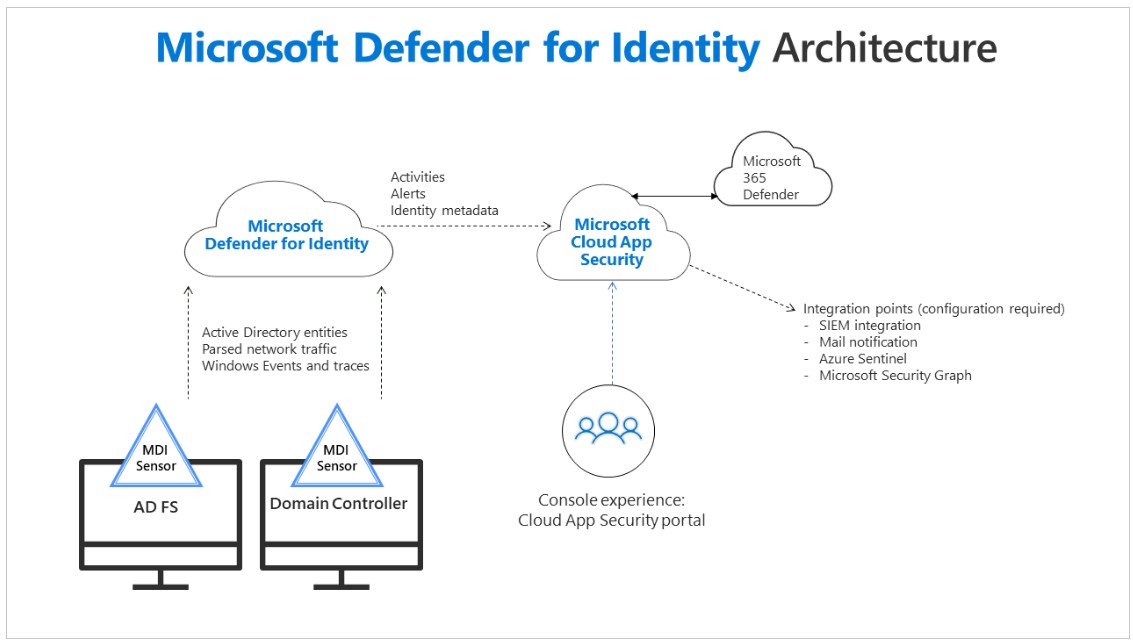
Microsoft Defender for Identity
- Enables you to identify, detect, and investigate advanced threats in your organization.
- Allows you to monitor user activities and information.
- Identify and investigate advanced threats throughout the entire cyber-attack kill chain:
- Reconnaissance – identify attempts by attackers to gain information.
- Compromised credentials – any attempts that compromise user credentials shall be detected.
- Lateral movements – attacks to gain access to sensitive accounts.
- Domain dominance – the attacker has the credentials to access your domain controller.
- Exfiltration – unauthorized data transfer.


No comments:
Post a Comment