Amazon Inspector
- An automated security assessment service that helps you test the network accessibility of your EC2 instances and the security state of your applications running on the instances.
- Inspector uses IAM service-linked roles.
Features
- Inspector provides an engine that analyzes system and resource configuration and monitors activity to determine what an assessment target looks like, how it behaves, and its dependent components. The combination of this telemetry provides a complete picture of the assessment target and its potential security or compliance issues.
- Inspector incorporates a built-in library of rules and reports. These include checks against best practices, common compliance standards and vulnerabilities.
- Automate security vulnerability assessments throughout your development and deployment pipeline or against static production systems.
- Inspector is an API-driven service that uses an optional agent, making it easy to deploy, manage, and automate.
Concepts
- Inspector Agent – A software agent that you can install on all EC2 instances that are included in the assessment target, the security of which you want to evaluate with Inspector.
- Assessment run – The process of discovering potential security issues through the analysis of your assessment target’s configuration and behavior against specified rules packages.
- Assessment target – A collection of AWS resources that work together as a unit to help you accomplish your business goals. Inspector assessment targets can consist only of EC2 instances.
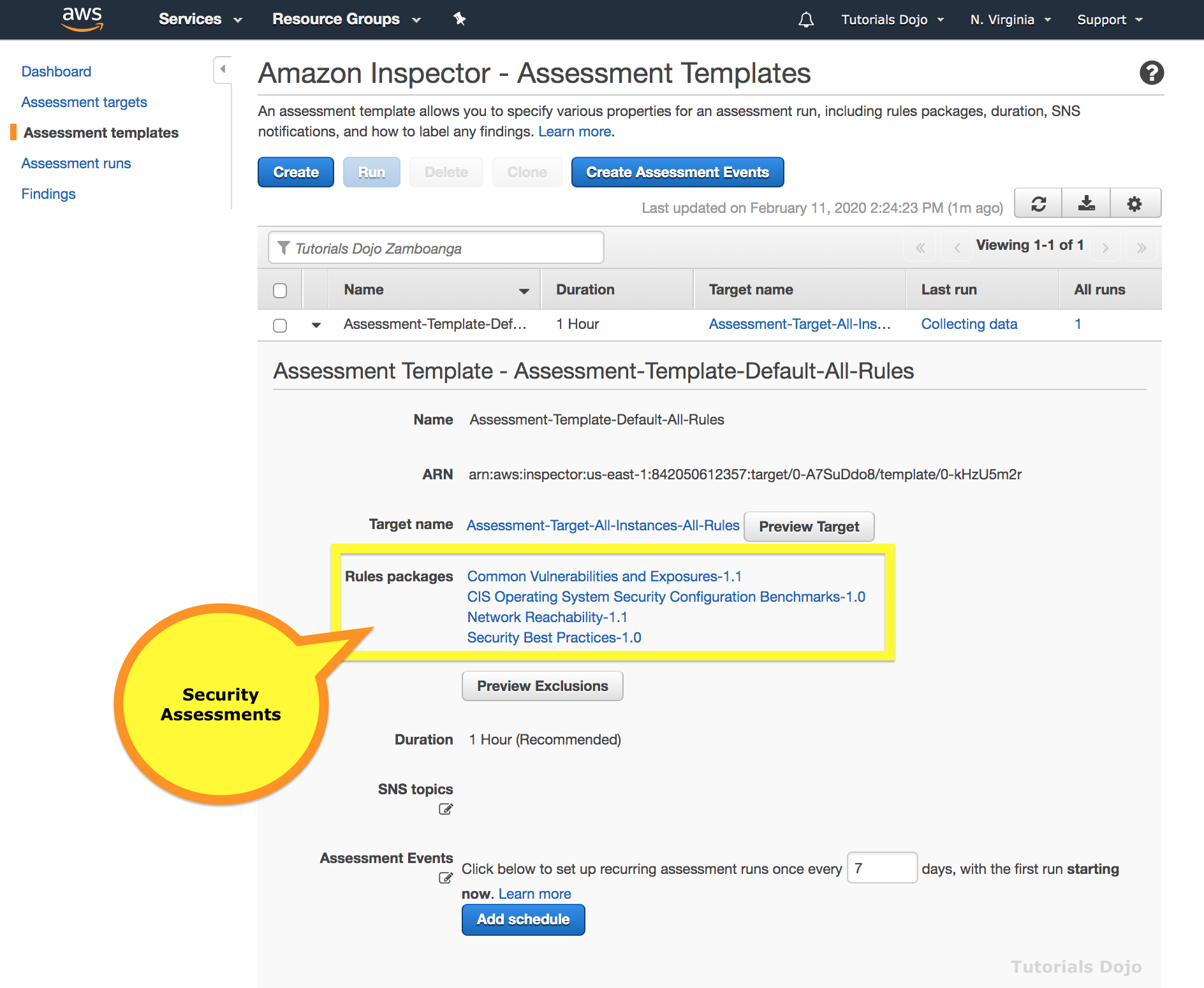
- Assessment template – A configuration that is used during your assessment run, which includes
- Rules packages against which you want Inspector to evaluate your assessment target,
- The duration of the assessment run,
- Amazon SNS topics to which you want Inspector to send notifications about assessment run states and findings,
- Inspector-specific attributes (key-value pairs) that you can assign to findings generated by the assessment run that uses this assessment template.
- After you create an assessment template, you can’t modify it.
- Finding – A potential security issue discovered during the assessment run of the specified target.
- Rule – A security check performed during an assessment run. When a rule detects a potential security issue, Inspector generates a finding that describes the issue.
- Rules package – A collection of rules that corresponds to a security goal that you might have.
- Telemetry – EC2 instance data collected by Inspector during an assessment run and passed to the Inspector service for analysis.
- The telemetry data generated by the Inspector Agent during assessment runs is formatted in JSON files and delivered in near-real-time over TLS to Inspector, where it is encrypted with a per-assessment-run, ephemeral KMS-derived key and securely stored in an S3 bucket dedicated for the service.
Rules Packages and Rules
- Inspector compares the behavior and the security configuration of the assessment targets to selected security rules packages.
- Rules are grouped together into distinct rules packages either by category, severity, or pricing.
- Each rule has an assigned severity level
- High, Medium, and Low levels all indicate a security issue that can result in compromised information confidentiality, integrity, and availability within your assessment target.
- The Informational level simply highlights a security configuration detail of your assessment target.
- The findings generated by rules in the Network Reachability package show whether your ports are reachable from the internet through an internet gateway, a VPC peering connection, or a VPN through a virtual gateway. These findings also highlight network configurations that allow for potentially malicious access, such as mismanaged security groups, ACLs, IGWs, and so on.
Assessment Reports
- A document that details what is tested in the assessment run, and the results of the assessment.
- You can view the following types of assessment reports:
- Findings report – this report contains the following information:
- Executive summary of the assessment
- EC2 instances evaluated during the assessment run
- Rules packages included in the assessment run
- Detailed information about each finding, including all EC2 instances that had the finding
- Full report – this report contains all the information that is included in a findings report, and additionally provides the list of rules that passed on all instances in the assessment target.
Pricing
- Pricing is based on two dimensions
- The number of EC2 instances included in each assessment
- The type(s) of rules package you select: host assessment rules packages and/or the network reachability rules package


No comments:
Post a Comment