Authentication and Authorization: Every App service comes with an Authentication and Authorization module that handles several things for our app.
- It will authenticate the user with a specified provider such as Facebook, Google, Twitter, Azure Active Directory, etc.
- It will store, validate, and refreshes tokens.
- It also manages the authenticated session.
- It injects identity formation into request headers.
How Authentication and Authorization works
First, the request from the client browser will come to the App service front-end. From that, the request will be forwarded to the Authentication and Authorization module. And that Authentication module will include all the Authorization and Authentication logic, which includes token management and also session management, etc., and it sits outside the web app code. That is the reason we don't need to change code between our web application to enable Authentication and Authorization for our app in Azure. We can able to slightly influence this Authentication and Authorization logic using the environment variable in terms of tracing.
Authentication and Authorization module handles several things for our app:
- Authenticates users with the specified provider
- Validate, store, and refreshes tokens
- Manages the authenticated session
- Injects identity information into request headers
- Logging & tracing
Other security areas
There are additional security areas that we need to be aware of for App service, which we can take advantage of them.
- ISO, SOC, and PCI complaint: If we are processing credit card information, the underlying environment is PCI compliant, but at the same time, you have to go for PCI compliance from the application layer perspective. But, from the environment perspective, Microsoft Azure App Service is PCI compliant
- IP Address whitelisting: In case if we want to limit the trigger to our App services form a specific trusted IP Address, then we can white list the same within the Azure portal for our app services.
- SSL communication: To encrypt the data at transit, we can enable SSL communication.
Managed Service Identity
This service is recently added to Azure. What we are going to do here is creating an identity for our app, and providing access to different services to that identity. By doing this, we don't need to store any userID-password to access certain Azure services. What we generally do is we go to the Azure portal and tell to ARM to create managed service identity for your Azure App Service. And when we trigger that, a service principle gets created in Azure active directory.
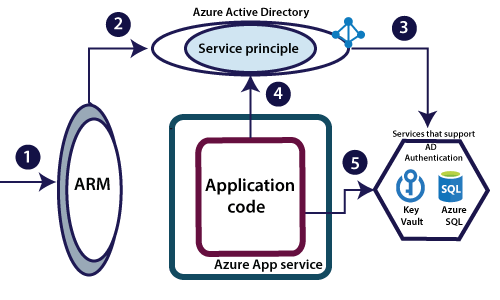
Example - if we want to Access a secret from Azure key vault. By submitting that token and having a proper access policy defined within Azure key vault, our application code will be able to retrieve the secret at run time and use that secret to access an on-premises resource.
App Service Environments security
If we are using App service environments, then we will get additional benefits in terms of security.
- Network security groups: We can associate with network security groups and control the traffic coming into our App service using network security groups.
- Web Application Firewall: It is a feature of application Gateway that provides centralized protection of your web applications from common exploits and vulnerabilities. The web application firewall is based on rules from the OWASP core rule sets 3.0 or 2.2.9
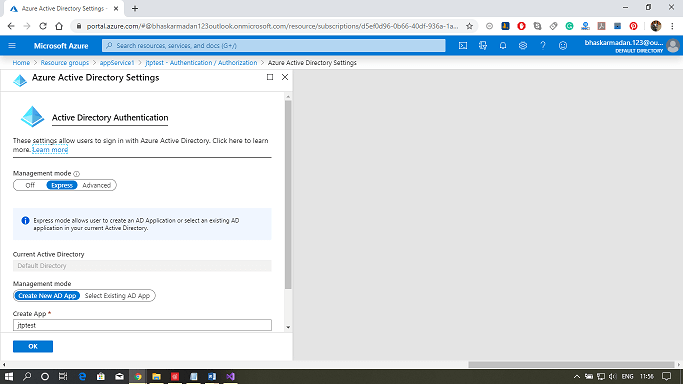
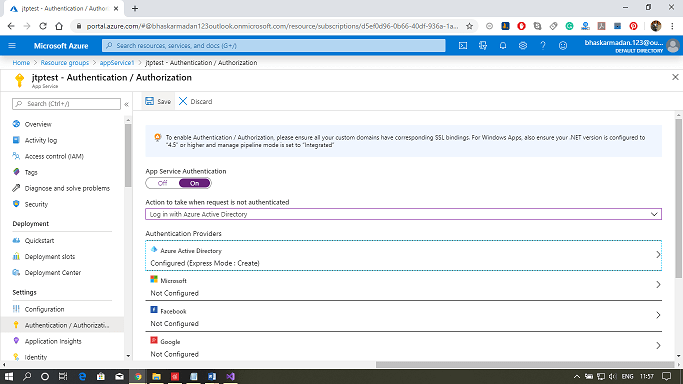
Enabling authentication with Azure active directory for Web App
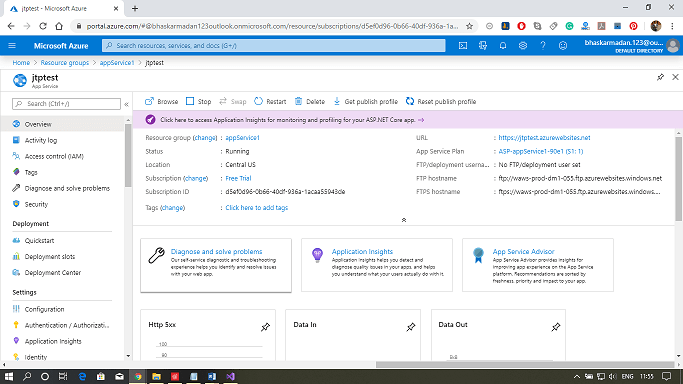
Step 1: Open your API App and click on Authentication/Authorization.
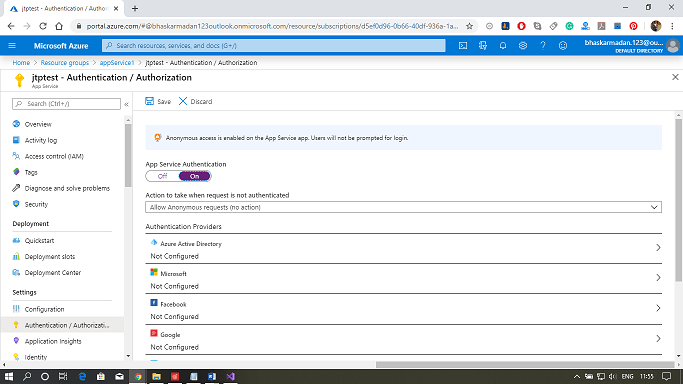
Step 2: Click on the toggle button showing switch on/off. Switch it on.
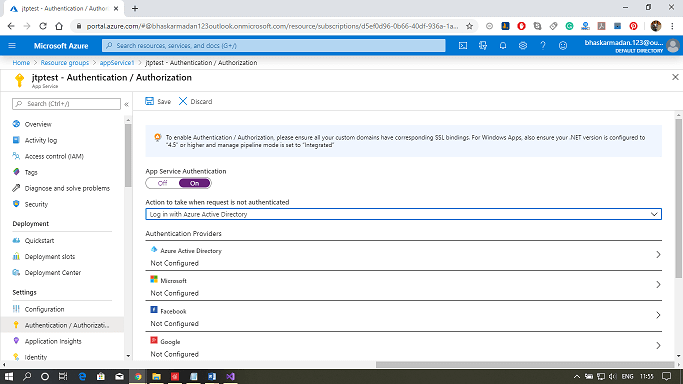
Step 3: Now select the Action to take when the request is not authenticated as "Login with Azure Active Directory."
Step 4: Now, configure the Azure Active Directory with the express mode. After that, click on create and then click on save.

No comments:
Post a Comment