Introduction to Azure Firewall
Microsoft recently announced the availability of a long-awaited service required by the users of systems in the Azure environment , it is the’Azure Firewall. The Azure Firewall is a new managed service and fully integrated into the Microsoft public cloud, that allows you to secure the resources present on the Virtual Networks of Azure. This article will look at the main features of this new service, currently in preview, and it will indicate the procedure to be followed for its activation and configuration.
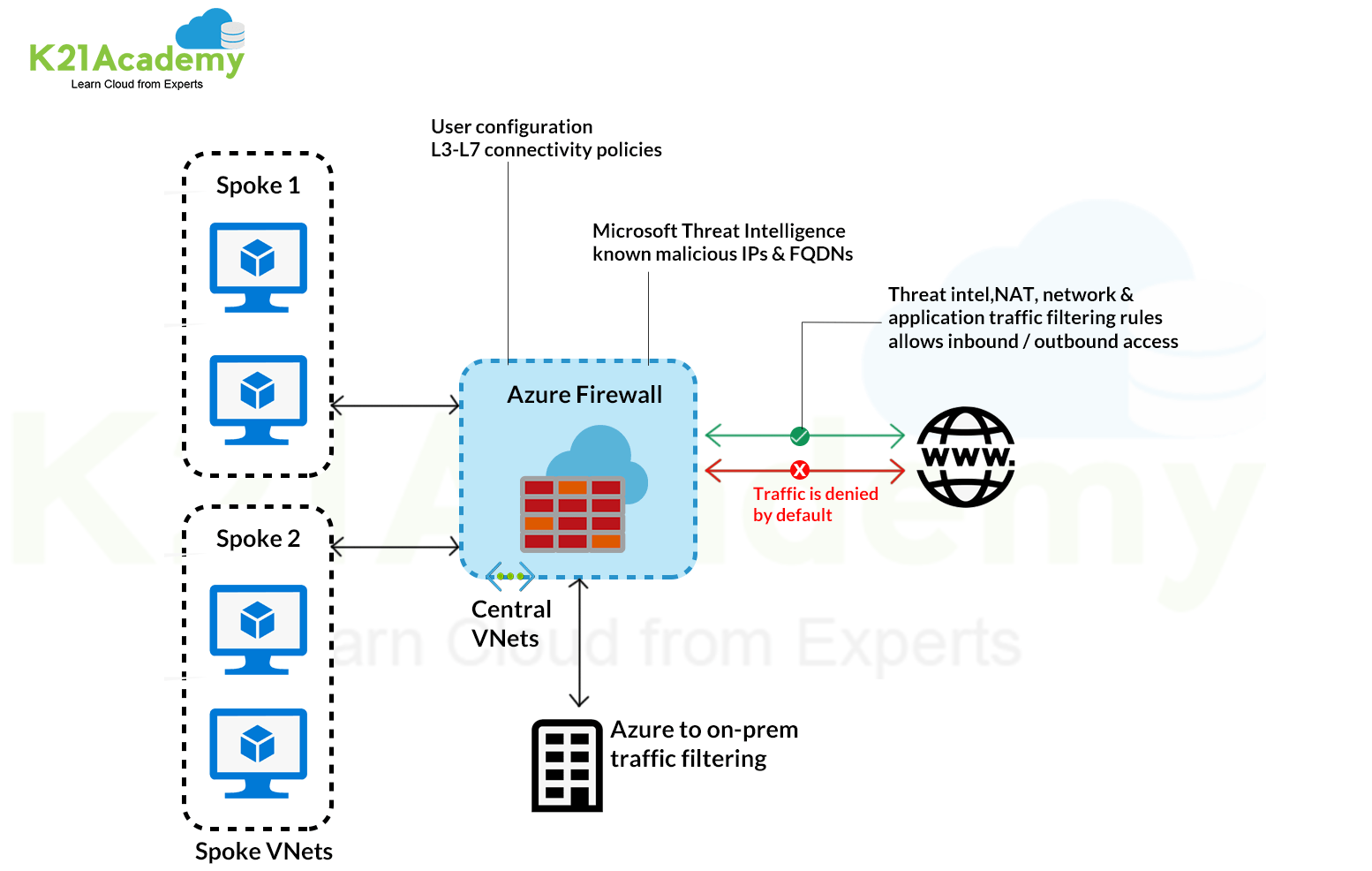
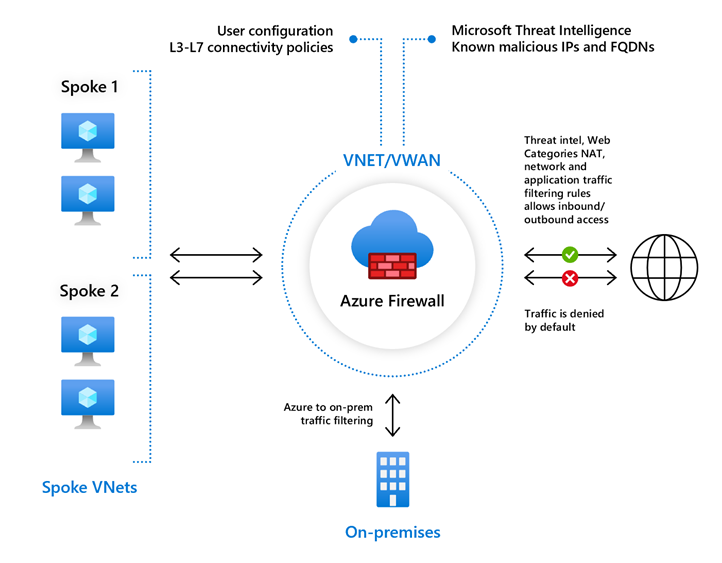
The Azure Firewall is a type of firewall stateful, which makes it possible to centrally control, through policy enforcement, network communication streams, all cross subscriptions and cross virtual networks. This service, in the presence of type of network architectures hub-and-spoke, lends itself to be placed in the Hub network, in order to obtain a complete control of the traffic.
The Azure Firewall features, currently available in this phase of public preview, are the following:
- High availability (HA) Built-in: high availability is integrated into the service and are not required specific configurations or add-ons to make it effective. This is definitely an element that distinguishes it compared to third-party solutions that, for the configuration of Network Virtual Appliance (NVA) in HA, typically require the configuration of additional load balancers.
- Unrestricted cloud scalability: Azure Firewall allows you to scale easily to adapt to any change of network streams.
- FQDN filtering: you have the option to restrict outbound HTTP/S traffic towards a specific list of fully qualified domain names (FQDN), with the ability to use wild card characters in the creation of rules.
- Network traffic filtering rules: You can create rules to allow or of deny to filter the network traffic based on the following elements: source IP address, destination IP address, ports and protocols.
- Outbound SNAT support: to the Azure Firewall is assigned a public static IP address, which will be used by outbound traffic (Source Network Address Translation), generated by the resources of the Azure virtual network, allowing easy identification from remote Internet destinations.
- Azure Monitor logging: all events of Azure Firewall can be integrated into Azure Monitor. In the settings of the diagnostic logs you are allowed to enable archiving of logs in a storage account, stream to an Event Hub, or set the sending to a workspace of OMS Log Analytics.
Azure Firewall is currently in a managed public preview, which means that to implement it is necessary to explicitly perform the enable via the PowerShell command Register-AzureRmProviderFeature.
Feature registration can take up to 30 minutes and you can monitor the status of registration with the following PowerShell commands:
Figure 03 – PowerShell commands to verify the status of enabling Azure Firewall
After registration, you must run the following PowerShell command:
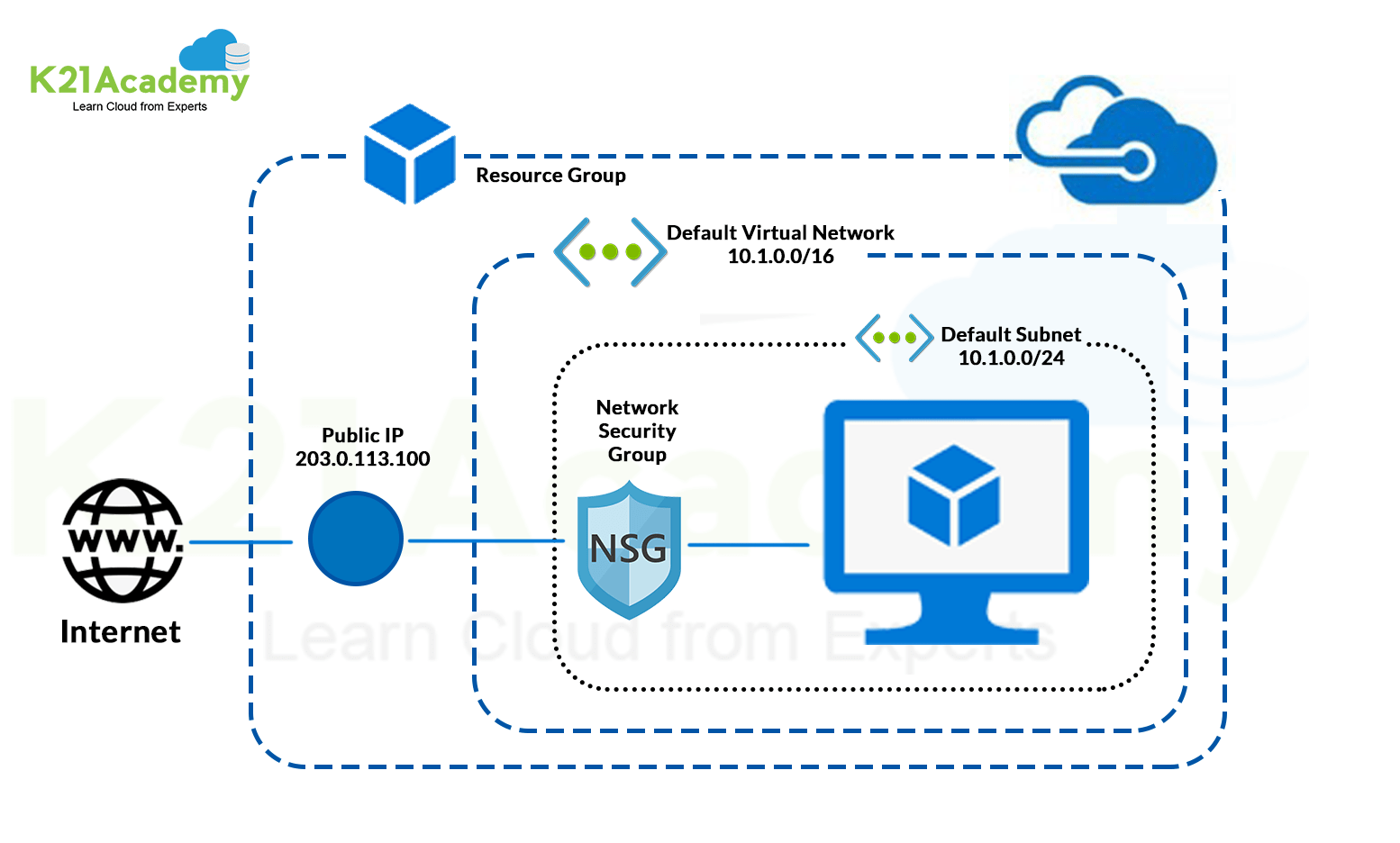
To deploy the Azure Firewall on a specific Virtual Network requires the presence of a subnet called AzureFirewallSubnet, that must be configured with a sunbnet mask at least /25.
To deploy Azure Firewall from the Azure portal, you must select Create a resource, Networking and later See all:
Filtering for Firewall will also appear the new resource Azure Firewall:
By starting the creation process you will see the following screen that prompts you to enter the necessary parameters for the deployment:
In order to bring outbound traffic of a given subnet to the firewall you must create a route table that contains a route with the following characteristics:
Although Azure Firewall is a managed service, you must specify Virtual appliance as next hop. The address of the next hop will be the private IP of Azure Firewall.
The route table must be associated with the virtual network that you want to control with Azure Firewall.
At this point, for systems on the subnet that forwards the traffic to the Firewall, is not allowed outgoing traffic, as long as it is not explicitly enabled:
Azure Firewall provides the following types of rules to control outbound traffic.
- Application rules: to configure access to specific fully qualified domain names (FQDNs) from a given subnet.
- Network rules: enable the configuration of rules that contain the source address, the protocol, the address and port of destination.
















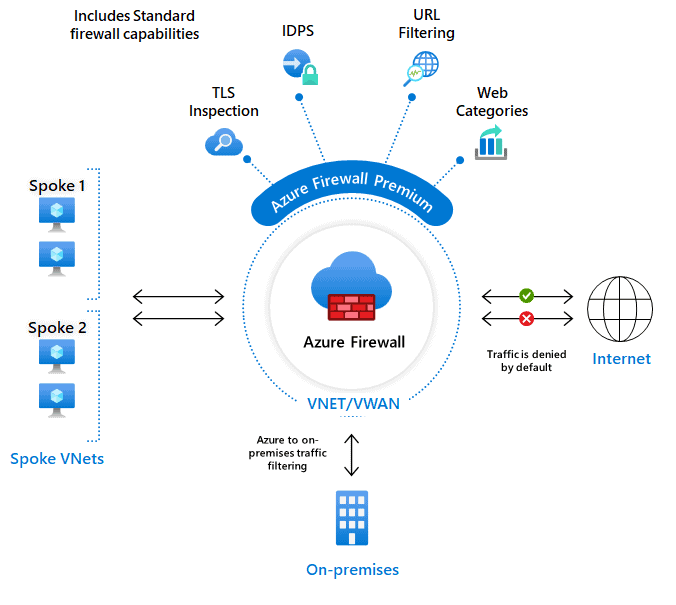
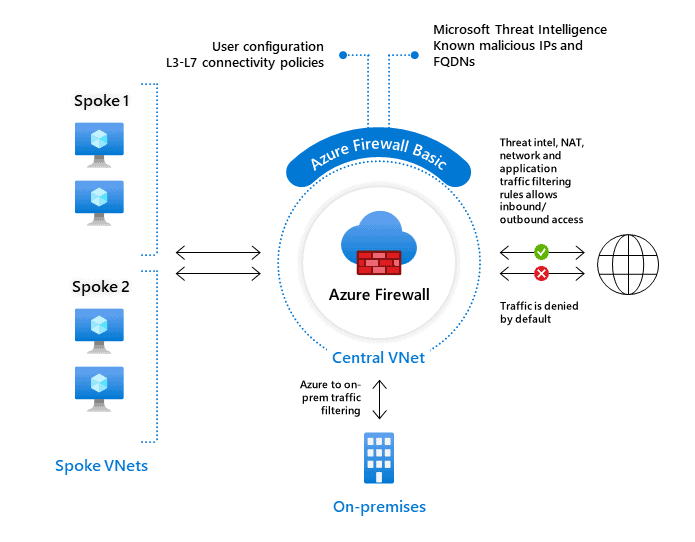 How does Firewall Azure Work?
How does Firewall Azure Work?