Create a custom IPv6 address prefix using the Azure portal
A custom IPv6 address prefix enables you to bring your own IPv6 ranges to Microsoft and associate it to your Azure subscription. The range would continue to be owned by you, though Microsoft would be permitted to advertise it to the Internet. A custom IP address prefix functions as a regional resource that represents a contiguous block of customer owned IP addresses.
The steps in this article detail the process to:
Prepare a range to provision
Provision the range for IP allocation
Enable the range to be advertised by Microsoft
Differences between using BYOIPv4 and BYOIPv6
Important
Onboarded custom IPv6 address prefixes have several unique attributes which make them different than custom IPv4 address prefixes.
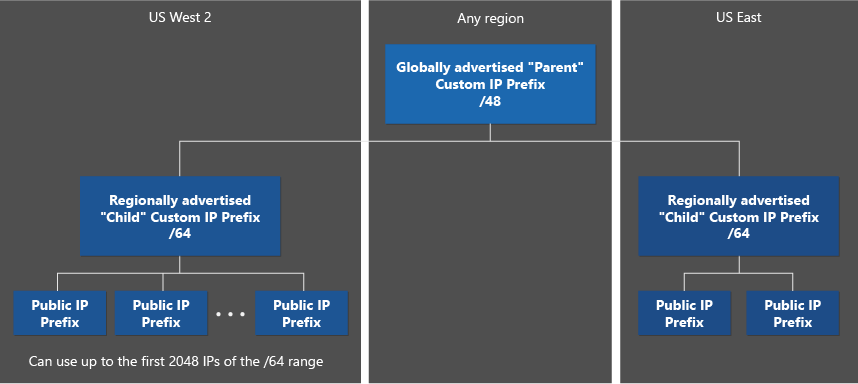
Custom IPv6 prefixes use a parent/child model. In this model, the Microsoft Wide Area Network (WAN) advertises the global (parent) range, and the respective Azure regions advertise the regional (child) ranges. Global ranges must be /48 in size, while regional ranges must always be /64 size. You can have multiple /64 ranges per region.
Only the global range needs to be validated using the steps detailed in the Create Custom IP Address Prefix articles. The regional ranges are derived from the global range in a similar manner to the way public IP prefixes are derived from custom IP prefixes.
Public IPv6 prefixes must be derived from the regional ranges. Only the first 2048 IPv6 addresses of each regional /64 custom IP prefix can be utilized as valid IPv6 space. Attempting to create public IPv6 prefixes that span beyond this will result in an error.
Prerequisites
- An Azure account with an active subscription. Create an account for free.
- A customer owned IPv6 range to provision in Azure. A sample customer range (2a05:f500:2::/48) is used for this example, but wouldn't be validated by Azure; you need to replace the example range with yours.
Note
For problems encountered during the provisioning process, please see Troubleshooting for custom IP prefix.
Pre-provisioning steps
To utilize the Azure BYOIP feature, you must perform and number of steps prior to the provisioning of your IPv6 address range. Refer to the IPv4 instructions for details. All these steps should be completed for the IPv6 global (parent) range.
Provisioning for IPv6
The following steps display the modified steps for provisioning a sample global (parent) IPv6 range (2a05:f500:2::/48) and regional (child) IPv6 ranges. Some of the steps have been abbreviated or condensed from the IPv4 instructions to focus on the differences between IPv4 and IPv6.
Provision a global custom IPv6 address prefix
The following flow creates a custom IP prefix in the specified region and resource group. No zonal properties are provided because the global range isn't associated with any particular region (and therefore no regional availability zones).
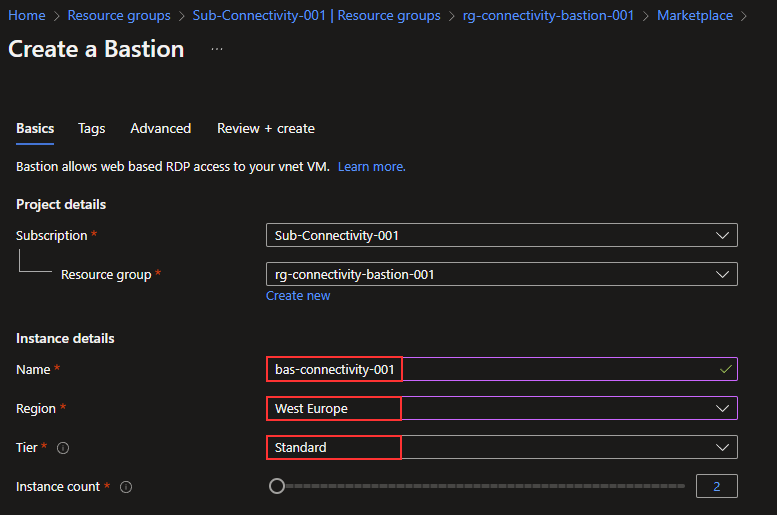
Sign in to Azure
Sign in to the Azure portal.
Create and provision a custom IP address prefix
In the search box at the top of the portal, enter Custom IP.
In the search results, select Custom IP Prefixes.
Select + Create.
In Create a custom IP prefix, enter or select the following information:
Setting Value Project details Subscription Select your subscription Resource group Select Create new.
Enter myResourceGroup.
Select OK.Instance details Name Enter myCustomIPv6GlobalPrefix. Region Select West US 2. IP Version Select IPv6. IP prefix range Select Global. Global IPv6 Prefix (CIDR) Enter 2a05:f500:2::/48. ROA expiration date Enter your ROA expiration date in the yyyymmdd format. Signed message Paste in the output of $byoipauthsigned from the pre-provisioning section. Availability Zones Select Zone-redundant. 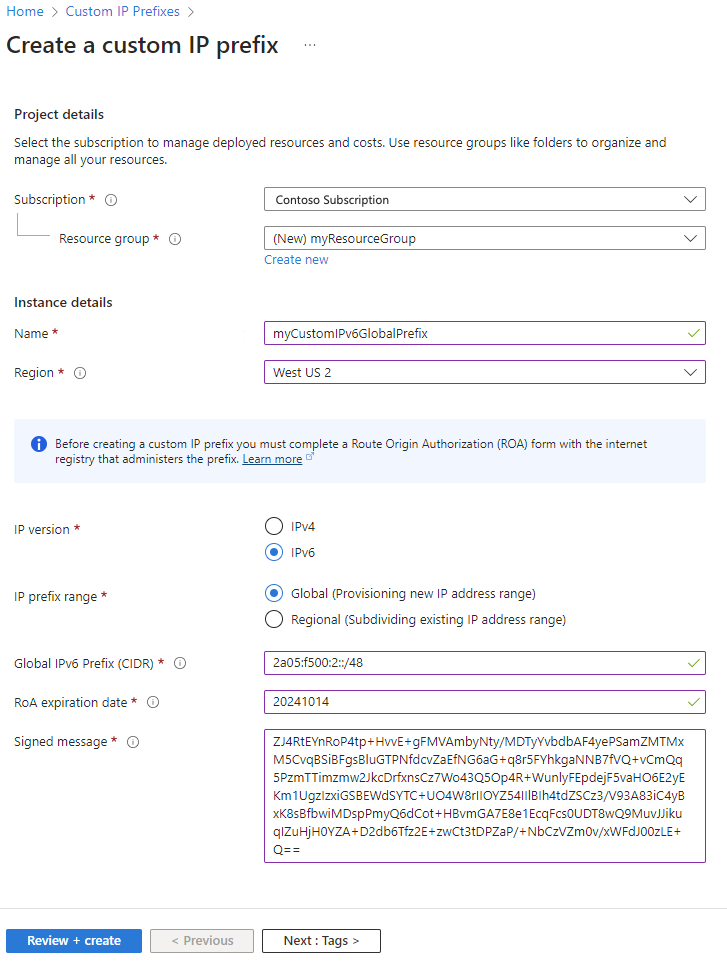
Select the Review + create tab or the blue Review + create button at the bottom of the page.
Select Create.
The range is pushed to the Azure IP Deployment Pipeline. The deployment process is asynchronous. You can check the status by reviewing the Commissioned state field for the custom IP prefix.
Provision a regional custom IPv6 address prefix
After the global custom IP prefix is in a Provisioned state, regional custom IP prefixes can be created. These ranges must always be of size /64 to be considered valid. The ranges can be created in any region (it doesn't need to be the same as the global custom IP prefix), keeping in mind any geolocation restrictions associated with the original global range. The "children" custom IP prefixes will be advertised locally from the region they're created in. Because the validation is only done for global custom IP prefix provision, no Authorization or Signed message is required. (Because these ranges will be advertised from a specific region, zones can be utilized.)
In the same Create a custom IP prefix page as before, enter or select the following information:
| Setting | Value |
|---|---|
| Project details | |
| Subscription | Select your subscription |
| Resource group | Select Create new. Enter myResourceGroup. Select OK. |
| Instance details | |
| Name | Enter myCustomIPv6RegionalPrefix. |
| Region | Select West US 2. |
| IP Version | Select IPv6. |
| IP prefix range | Select Regional. |
| Custom IP prefix parent | Select myCustomIPv6GlobalPrefix (2a05:f500:2::/48) from the drop down menu. |
| Regional IPv6 Prefix (CIDR) | Enter 2a05:f500:2:1::/64. |
| ROA expiration date | Enter your ROA expiration date in the yyyymmdd format. |
| Signed message | Paste in the output of $byoipauthsigned from the pre-provisioning section. |
| Availability Zones | Select Zone-redundant. |
Similar to IPv4 custom IP prefixes, after the regional custom IP prefix is in a Provisioned state, public IP prefixes can be derived from the regional custom IP prefix. These public IP prefixes and any public IP addresses derived from them can be attached to networking resources, though they aren't yet being advertised.
Important
Public IPv6 prefixes derived from regional custom IPv6 prefixes can only utilize the first 2048 IPs of the /64 range.
Commission the custom IPv6 address prefixes
When you commission custom IPv6 prefixes, the global and regional prefixes are treated separately. In other words, commissioning a regional custom IPv6 prefix isn't connected to commissioning the global custom IPv6 prefix.
The safest strategy for range migrations is as follows:
- Provision all required regional custom IPv6 prefixes in their respective regions. Create public IPv6 prefixes and public IP addresses and attach to resources.
- Commission each regional custom IPv6 prefix and test connectivity to the IPs within the region. Repeat for each regional custom IPv6 prefix.
- After all regional custom IPv6 prefixes (and derived prefixes/IPs) have been verified to work as expected, commission the global custom IPv6 prefix, which will advertise the larger range to the Internet.
To commission a custom IPv6 prefix (regional or global) using the portal:
In the search box at the top of the portal, enter Custom IP and select Custom IP Prefixes.
Verify the custom IPv6 prefix is in a Provisioned state.
In Custom IP Prefixes, select the desired custom IPv6 prefix.
In Overview page of the custom IPv6 prefix, select the Commission button near the top of the screen. If the range is global, it begins advertising from the Microsoft WAN. If the range is regional, it advertises only from the specific region.