What is Azure Bastion?
Azure Bastion is a fully managed Platform-as-a-Service (PaaS) offering provided and maintained by Microsoft, including security and patch management.
Azure Bastion is deployed/associated at the level of each Azure Virtual Network (VNet) and supports all VMs within that VNet.
VMs are never exposed to the internet (no public IP addresses); only the Azure Bastion service is exposed and accessible via HTTPS through the Azure portal.
Bastion architecture
The following diagram illustrates RDP/SSH access through Azure Bastion. It is evident that to connect to any VM, one must go through a single access point, which is the bastion.

Azure Bastion pricing
The cost of Azure Bastion depends on the selected SKU (version), as there are both a basic version and a standard version. There is an hourly cost (starting from €0.198 per hour), to which outgoing data transfer consumption needs to be added.
While Azure Bastion provides significant security benefits, it’s essential to be aware that there is a notable usage cost associated with it and in my opinion, it is impossible to know the cost of Azure Bastion in advance.
Setting up Azure Bastion
Create a resource group to host the bastion, then create a bastion by going to the Azure search area and searching for ‘Bastion’.
Provide the necessary information for bastion creation:
- Name: The name of the bastion.
- Region: The location of the bastion host; it is recommended to use the same region as your VMs to avoid additional latency.
- Tier: Choose ‘Standard’ or ‘Basic’ based on your SKU requirements.
- Number of instances: In ‘Standard’ mode, you can adjust the number of instances. Beyond 2 instances, there is an additional cost, but it’s important to note that ‘Each instance can handle 25 simultaneous RDP connections and 50 simultaneous SSH connections for average workloads.’ So, having 2 instances is already sufficient.

For the virtual network, click on ‘New’.
Specify the name of the virtual network, then change the default subnet name to ‘AzureBastionSubnet.’ There is no specific explanation for the requirement to use this name, but it is mandatory.

Leave the other options as default.
Then “Review+create”
then “create”
After approximately 10 minutes, the Azure Bastion will be ready! It will appear in the list of bastions in your subscription, and, of course, for now, the list of active sessions is empty.
Access to a VM with Bastion
Now, let’s test our freshly created Azure Bastion! To connect to your virtual machine through Bastion, the connection must be initiated from the Azure portal.
Note that Azure Bastion deployment is per virtual network, not per subscription/account or virtual machine.
Once you provision the Azure Bastion service in your virtual network, the RDP/SSH experience is available to all your VMs in the same VNet and peered VNets. You will need to add peering between the two VNets: the one for the VM (and for each VM you want to put on the Bastion) and the one for the Bastion.
Add peering between your VM and the Bastion
Go to your VM Virtual Network
Search for ‘Peering’ under ‘Settings’ and click on ‘Add’.

Specify that you want to connect from this VM to the Bastion and vice versa and shoose the vnet to connect

Your VM are now peered to your Bastion

Connect to your VM From Bastion
You have two methods to connect to your VM, either directly from the VM by accessing Bastion under Operation or from Bastion by selecting the specific VM.

Provide your username and password to log in to the VM.
Troubleshooting
Sometimes, when you attempt to connect, you may encounter a black screen with the message “The network connection to the Bastion Host appears unstable.”
You can resolve this issue by following these steps:
- Click on the VM.
- Navigate to ‘Run command.’
- Select ‘SetRDPPort,’ and a ‘Run Command Script’ window will appear.
- Enter the RDP Port number (3389) and click ‘Run.’
- After the command runs successfully, return to the VM and connect via Bastion.
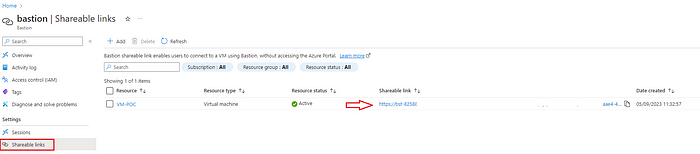
Shareable links with bastion
The Bastion Shareable Link feature enables users to establish connections to virtual machines or virtual machine scale sets using Azure Bastion, all without needing to access the Azure portal. However, before you can utilize this feature, it must be enabled.
- Navigate to your Bastion resource.
- On your Bastion page, in the left pane, click on ‘Configuration.’
- Within the Configuration page, select ‘Standard’ for the Tier option. This feature specifically requires the Standard SKU, as it empowers host scaling and enables customization of additional features. It’s crucial to note that once you’ve enabled this feature, you cannot downgrade to the Basic tier.

Now you have a new link called ‘Shareable Links.
On the Create shareable link page, select the resources for which you want to create a shareable link. You can select specific resources, or you can select all. A separate shareable link will be created for each selected resource. Click Apply to create links.

Once the links are created, you can view them on the Shareable links page.
After receiving the link, when the user opens the shareable link in their preferred browser to connect the VMs.
In the left corner, the user can select whether to see text and images copied to the clipboard. The user inputs the required information, then clicks Login to connect.

Transfer files to your Azure VM using Bastion
With the standard version of Bastion, we can now transfer files to our VM without having an open public IP address and without allowing the RDP port in the Network Security Group.
To do this, as previously mentioned, you will need to :
- have the Bastion Standard tier (rather than the Basic tier),
- enable the connection with a native RDP client in the Bastion configuration.

Connection Process
With your PowerShell tool (Do not run PowerShell in Admin mode, or you will encounter an error) , login to your Azure account with the command
az loginand if you have more than one subscription, set the subscription where your VM is (you just need the subscription name)
az account set --subscription "YourSubscriptionName"You must have previously determined the VM Resource ID.
Go to your VM’s properties to determine the resource ID.

Run the az network bastion rdp command, with the name of your Bastion host, the Resource Group name and your VM’s resource ID
az network bastion rdp --name "YourBastionName" --resource-group "BastionResourceGroupName" --target-resource-id "YourVMResourceId"the prompt will may be ask you to install the extension bastion. Say Yes to the installation.

If you have a different rdp port than 3389, use the option “ — resource-port” with ae network bastion rdp:
az network bastion rdp --name "YourBastionName" --resource-group "BastionResourceGroupName" --target-resource-id "YourVMResourceId" --resource-port "YourRDPport"Transfer file
That’s it; you can now perform the classic copy/paste of your files.
Roles and rights to use native RDP
Verify that the following roles are configured in order to connect to the VM:
- Reader role on the virtual machine.
- Reader role on the NIC with private IP of the virtual machine.
- Reader role on the Azure Bastion resource.
- Virtual Machine Administrator Login
which gives us for a specific user:

Troubleshooting
If you have this error (azure native rdp Invalid connection file) when you run the command “az network bastion rdp” :

Run Powershell without Admin right
