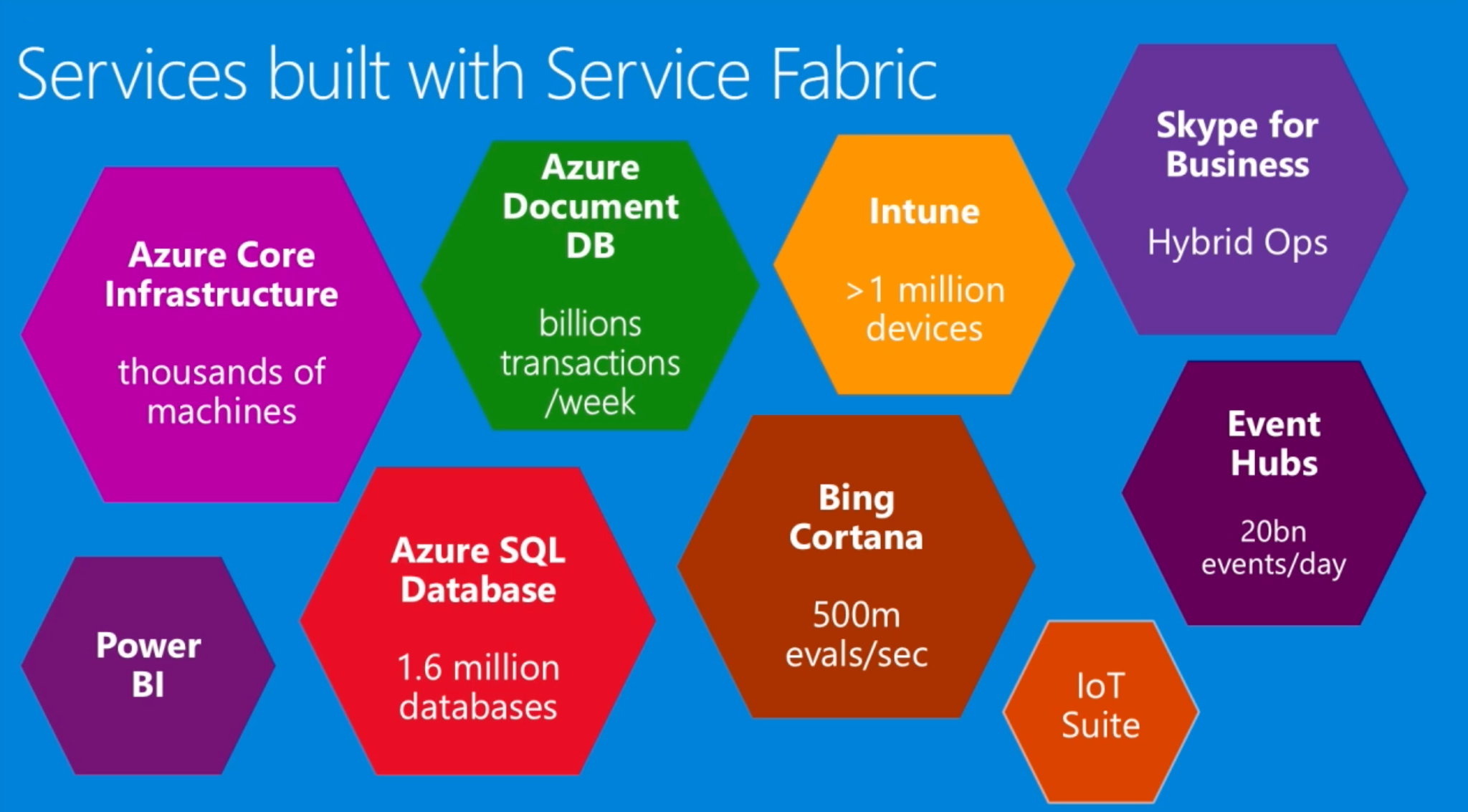
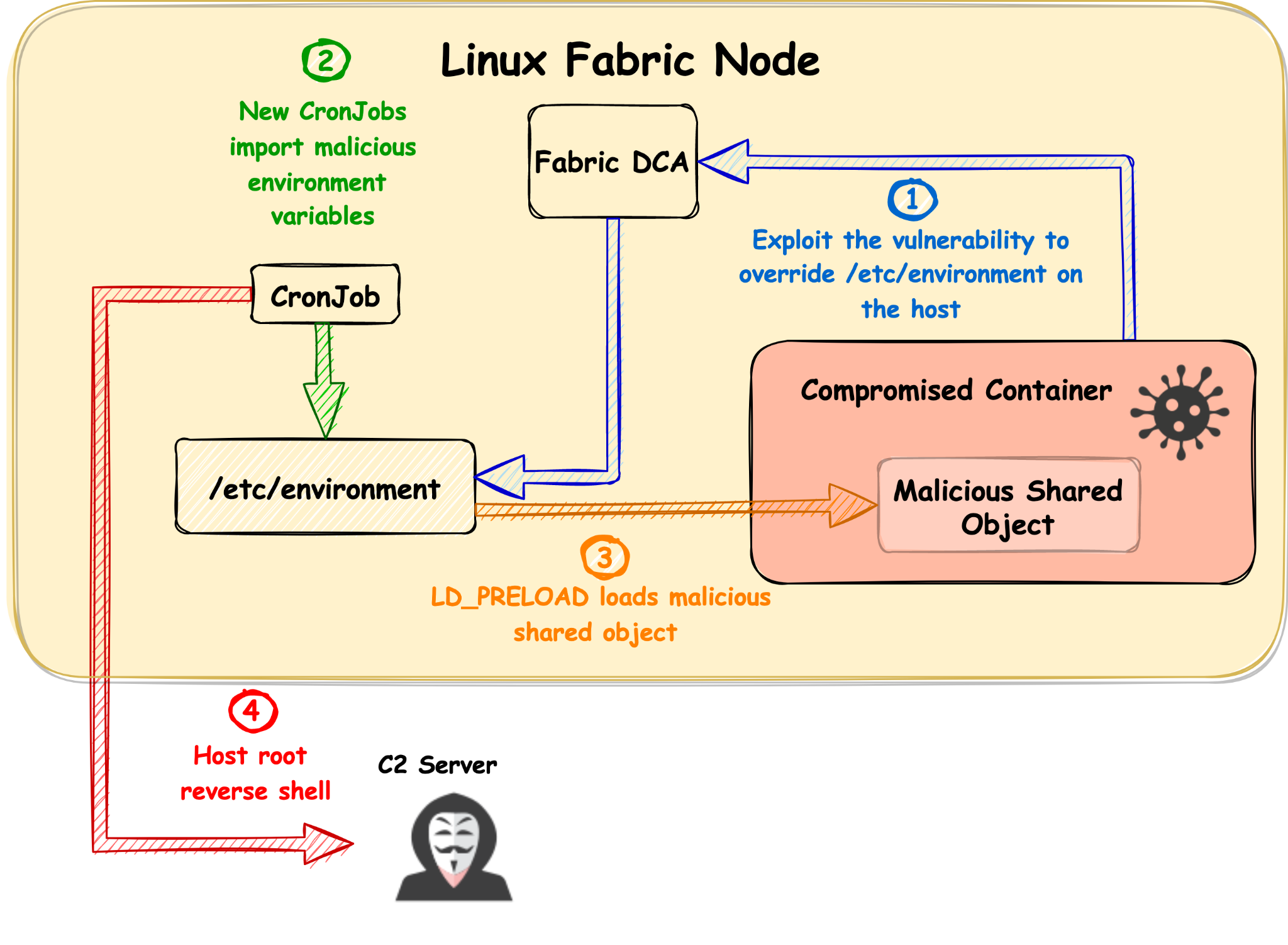
A Service Fabric cluster represents a set of hardware resources that you can deploy applications to. Typically, a cluster is made up of anywhere from 5 to many 1000s of machines, but the Service Fabric SDK includes a cluster configuration that can run on a single machine.
It is important to understand that the Service Fabric local cluster is not an emulator or simulator. It runs the same platform code found on multi-machine clusters. The only difference is that it runs the platform processes normally spread across five machines on one.
The SDK provides two ways to setup a local cluster: a Windows PowerShell script and the Local Cluster Manager system tray app. In this tutorial, we will use the PowerShell script.
[AZURE.NOTE] If you have already created a local cluster by deploying an application from Visual Studio, you can skip this section.
Launch a new PowerShell window as an administrator.
Run the cluster setup script from the SDK folder:
& "$ENV:ProgramFiles\Microsoft SDKs\Service Fabric\ClusterSetup\DevClusterSetup.ps1"
Cluster setup will take a few moments, after which you should see output that looks something like this:
You are now ready to try deploying an application to your cluster.
The Service Fabric SDK includes a rich set of frameworks and developer tooling for creating applications. If you are interested in learning how to create applications in Visual Studio, see Creating your first application in Visual Studio. In this tutorial, we will use an existing sample application (called WordCount) so that we can focus on the management aspects of the platform, including deployment, monitoring, and upgrade.
Launch a new PowerShell window as an administrator.
Import the Service Fabric SDK PowerShell module.
Import-Module "$ENV:ProgramFiles\Microsoft SDKs\Service Fabric\Tools\PSModule\ServiceFabricSDK\ServiceFabricSDK.psm1"
Create a directory to store the application that you will download and deploy, such as c:\ServiceFabric.
mkdir c:\ServiceFabric\ cd c:\ServiceFabric\
Download the WordCount application from here to the location you created.
Connect to the local cluster:
Connect-ServiceFabricCluster localhost:19000
Invoke the SDK's deployment command to create a new application, providing a name and a path to the application package.
Publish-NewServiceFabricApplication -ApplicationPackagePath c:\ServiceFabric\WordCountV1.sfpkg -ApplicationName "fabric:/WordCount" ```
If all goes well, you should see output like the following:
![Deploy an application to the local cluster][deploy-app-to-local-cluster]
To see the application in action, launch the browser and navigate to http://localhost:8081/wordcount/index. You should see something like this:
The WordCount application is very simple. It includes client-side JavaScript code to generate random five-character "words", which are then relayed to the application via an ASP.NET WebAPI. A stateful service keeps track of the number of words counted, partitioned based on the first character of the word. The application that we deployed contains a four partitions, so words beginning with A through G are stored in the first partition, H through N are stored in the second partition, and so on.
With the application deployed, let's look at some of the app details in PowerShell.
Query all deployed applications on the cluster:
Get-ServiceFabricApplicationAssuming that you have only deployed the WordCount app, you will see something like this:
Go to the next level by querying the set of services included in the WordCount application.
Get-ServiceFabricService -ApplicationName 'fabric:/WordCount'
Note that the application is made up of two services, the web front-end and the stateful service that manages the words.
Finally, take a look at the list of partitions for the WordCountService:
The set of commands you just used, like all Service Fabric PowerShell commands, are available for any cluster that you might connect to, local or remote.
For a more visual way to interact with the cluster, you can use the web-based Service Fabric Explorer tool by navigating to http://localhost:19080/Explorer in the browser.
[AZURE.NOTE] To learn more about Service Fabric Explorer, see Visualizing your cluster with Service Fabric Explorer
Service Fabric provides no-downtime upgrades by monitoring the health of the application as it rolls out across the cluster. Let's perform a simple upgrade of the WordCount application.
The new version of the application will now only count words that begin with a vowel. As the upgrade rolls out, we will see two changes in the application's behavior. First, the rate at which the count grows should slow, since fewer words are being counted. Second, since the first partition has two vowels (A and E) and all others contain only one each, its count should eventually start to outpace the others.
Download the v2 package from here to the same location where you downloaded the v1 package.
Return to your PowerShell window and use the SDK's upgrade command to register the new version in the cluster and begin upgrading fabric:/WordCount.
Publish-UpgradedServiceFabricApplication -ApplicationPackagePath C:\ServiceFabric\WordCountV2.sfpkg -ApplicationName "fabric:/WordCount" -UpgradeParameters @{"FailureAction"="Rollback"; "UpgradeReplicaSetCheckTimeout"=1; "Monitored"=$true; "Force"=$true}
You should see output in PowerShell that looks something like this as the upgrade begins.
While the upgrade is proceeding, you may find it easier to monitor its status from Service Fabric Explorer. Launch a browser window and navigate to http://localhost:19080/Explorer. Click Applications in the tree on the left and then choose Upgrades in Progress.
Note that the Upgrade Progress indicator represents the state of the upgrade within the upgrade domains of your cluster. As the upgrade proceeds through each domain, health checks are performed to ensure that the application is behaving properly before proceeding.
If you rerun the earlier query for the set of services included in the fabric:/WordCount application, you will notice that while the version of the WordCountService changed, the version of the WordCountWebService did not:
Get-ServiceFabricService -ApplicationName 'fabric:/WordCount'
This highlights how Service Fabric manages application upgrades, which is to only touch the set of services (or code/configuration packages within those services) that have changed, making the process of upgrading faster and more reliable.
Finally, return to the browser to observe the behavior of the new application version. As expected, the count progresses more slowly and the first partition ends up with slightly more of the volume.