Amazon Web Services (AWS), a subsidiary of Amazon.com, has invested billions of dollars in IT resources distributed across the globe. These resources are shared among all the AWS account holders across the globe. These account themselves are entirely isolated from each other. AWS provides on-demand IT resources to its account holders on a pay-as-you-go pricing model with no upfront cost. Amazon Web services offers flexibility because you can only pay for services you use or you need. Enterprises use AWS to reduce capital expenditure of building their own private IT infrastructure (which can be expensive depending upon the enterprise’s size and nature). AWS has its own Physical fiber network that connects with Availability zones, regions and Edge locations. All the maintenance cost is also bared by the AWS that saves a fortune for the enterprises.
Security of cloud is the responsibility of AWS but Security in the cloud is Customer’s Responsibility. The Performance efficiency in the cloud has four main areas:-
- Selection
- Review
- Monitoring
- Tradeoff
Advantages of Amazon Web Services
- AWS allows you to easily scale your resources up or down as your needs change, helping you to save money and ensure that your application always has the resources it needs.
- AWS provides a highly reliable and secure infrastructure, with multiple data centers and a commitment to 99.99% availability for many of its services.
- AWS offers a wide range of services and tools that can be easily combined to build and deploy a variety of applications, making it highly flexible.
- AWS offers a pay-as-you-go pricing model, allowing you to only pay for the resources you actually use and avoid upfront costs and long-term commitments.
Disadvantages of Amazon Web Services
- AWS can be complex, with a wide range of services and features that may be difficult to understand and use, especially for new users.
- AWS can be expensive, especially if you have a high-traffic application or need to run multiple services. Additionally, the cost of services can increase over time, so you need to regularly monitor your spending.
- While AWS provides many security features and tools, securing your resources on AWS can still be challenging, and you may need to implement additional security measures to meet your specific requirements.
- AWS manages many aspects of the infrastructure, which can limit your control over certain parts of your application and environment.
AWS Global Infrastructure
The AWS global infrastructure is massive and is divided into geographical regions. The geographical regions are then divided into separate availability zones. While selecting the geographical regions for AWS, three factors come into play
- Optimizing Latency
- Reducing cost
- Government regulations (Some services are not available for some regions)
Each region is divided into at least two availability zones that are physically isolated from each other, which provides business continuity for the infrastructure as in a distributed system. If one zone fails to function, the infrastructure in other availability zones remains operational. The largest region North Virginia (US-East), has six availability zones. These availability zones are connected by high-speed fiber-optic networking.
There are over 100 edge locations distributed all over the globe that are used for the CloudFront (content delivery network). Cloudfront can cache frequently used content such as images and videos(live streaming videos also) at edge locations and distribute it to edge locations across the globe for high-speed delivery and low latency for end-users. It also protects from DDOS attacks.
AWS Management Console
The AWS management console is a web-based interface to access AWS. It requires an AWS account and also has a smartphone application for the same purpose. So When you sign in for first time, you see the console home page where you see all the services provided by AWS. Cost monitoring is also done through the console.
AWS resources can also be accessed through various Software Development Kits (SDKs), which allows the developers to create applications as AWS as its backend. There are SDKs for all the major languages(e.g., JavaScript, Python, Node.js, .Net, PHP, Ruby, Go, C++). There are mobile SDKs for Android, iOS, React Native, Unity, and Xamarin. AWS can also be accessed by making HTTP calls using the AWS-API. AWS also provides a Command Line Interface (CLI) for remotely accessing the AWS and can implement scripts to automate many processes. This Console is also available as an app for Android and iOS. For mobile apps, you can simply download AWS console app.
AWS Cloud Computing Models
There are three cloud computing models available on AWS.
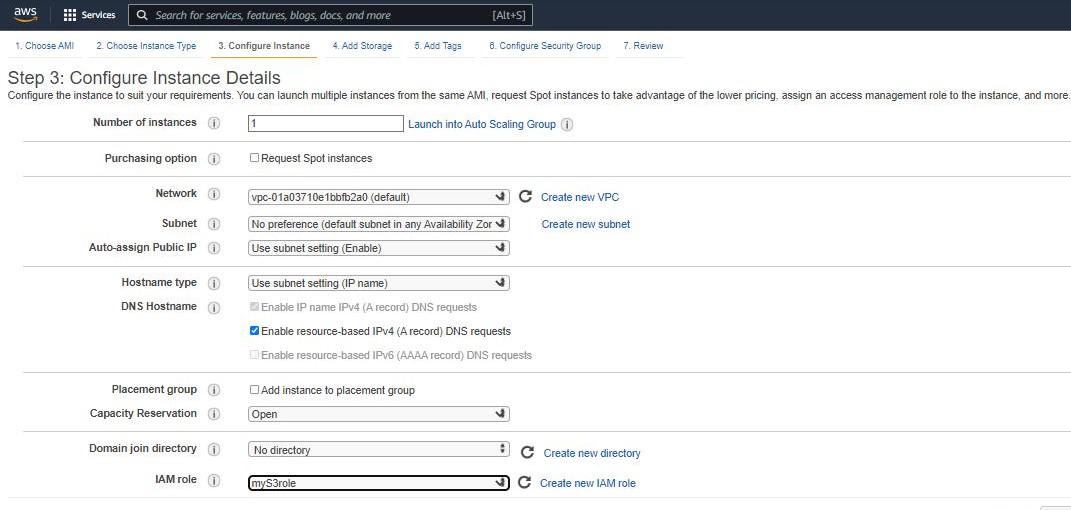
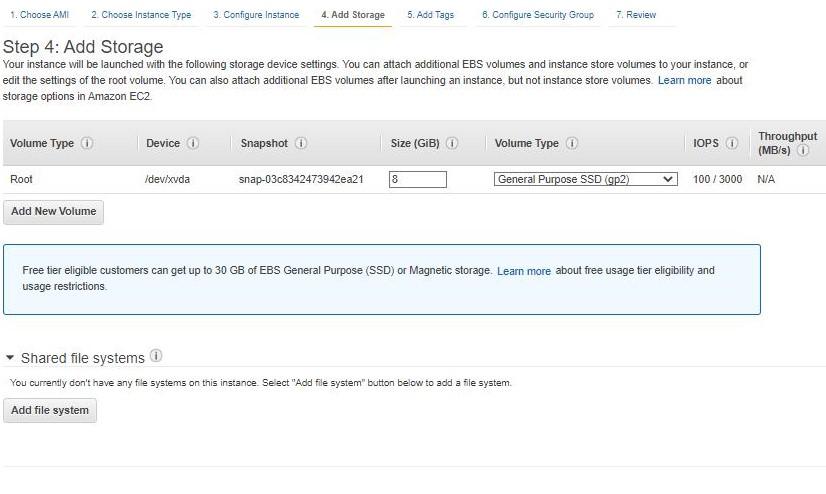
- Infrastructure as a Service (IaaS): It is the basic building block of cloud IT. It generally provides access to data storage space, networking features, and computer hardware(virtual or dedicated hardware). It is highly flexible and gives management controls over the IT resources to the developer. For example, VPC, EC2, EBS.
- Platform as a Service (PaaS): This is a type of service where AWS manages the underlying infrastructure (usually operating system and hardware). This helps the developer to be more efficient as they do not have to worry about undifferentiated heavy lifting required for running the applications such as capacity planning, software maintenance, resource procurement, patching, etc., and focus more on deployment and management of the applications. For example, RDS, EMR, ElasticSearch.
- Software as a Service(SaaS): It is a complete product that usually runs on a browser. It primarily refers to end-user applications. It is run and managed by the service provider. The end-user only has to worry about the application of the software suitable to its needs. For example, Saleforce.com, Web-based email, Office 365 .