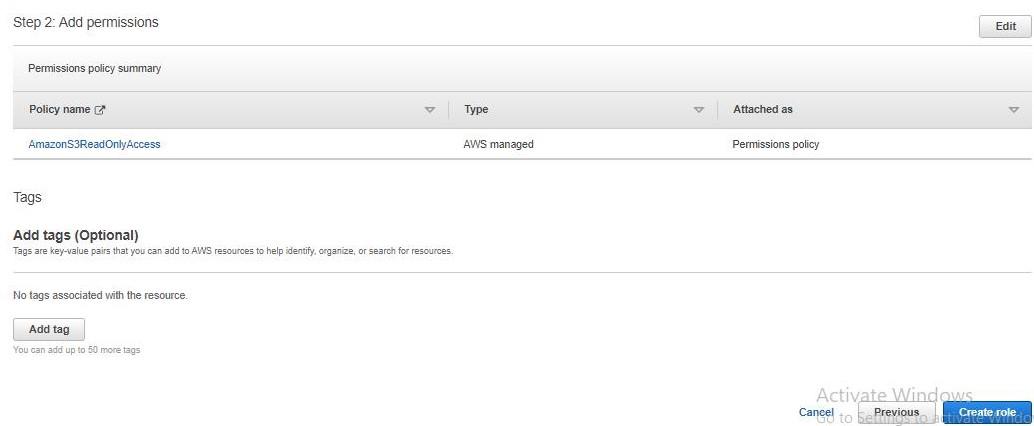
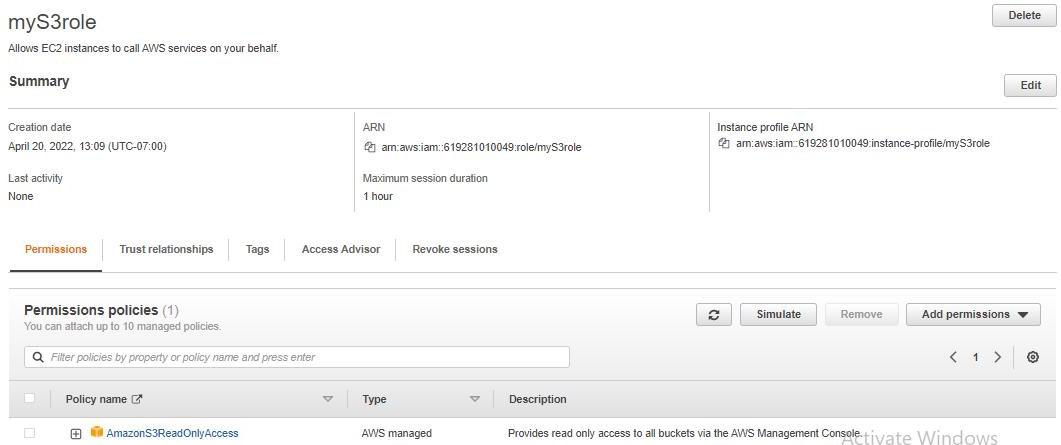
Amazon EC2 – Creating an Elastic Cloud Compute Instance
This article will educate you all about Amazon EC2. EC2 or Elastic Compute Cloud is a scalable computing service launched on the AWS cloud platform. In simpler words, EC2 is nothing but a virtual computer on which we can perform all our tasks and we have the authority to configure, launch or even dissipate this virtual computer. Hereby configuration, I mean RAM, ROM, storage, and so on, along with an extra secured environment. In return, AWS asks us to pay the bill for using their platform and their resources.
Advantages of EC2
- EC2 instances can be easily scaled up or down as per the requirement, providing a highly scalable and flexible infrastructure.
- EC2 instances are charged based on usage, making it cost-effective as you only pay for what you use.
- It can be easily deployed and managed using Amazon Web Services (AWS) management console, APIs, or CLI.
- It can be deployed in multiple availability zones to ensure high availability and data durability.
- It can be customized with different operating systems, applications, and network configurations.
Disadvantages of EC2 instances
- EC2 instances have limited customization options, which may not be sufficient for some applications.
- it can be expensive, especially when scaling up, and it can be challenging to control costs.
- This is vulnerable to security risks, such as unauthorized access, data breaches, and cyberattacks.
- EC2 instances can be complex to set up and manage, especially for non-technical users.
- It may experience latency due to the location of the instances and the data center, which can affect application performance.
Use cases of EC2 instances
- EC2 instances can be used to host websites, applications, and APIs in the cloud.
- It can be used to process large amounts of data using tools like Apache Hadoop and Apache Spark.
- It can be used to perform demanding computing tasks, such as scientific simulations and financial modeling.
- EC2 instances can be used to develop, test, and deploy software, allowing teams to quickly spin up resources as needed.
Now, let us look at the step-by-step process for creating an EC2 instance.
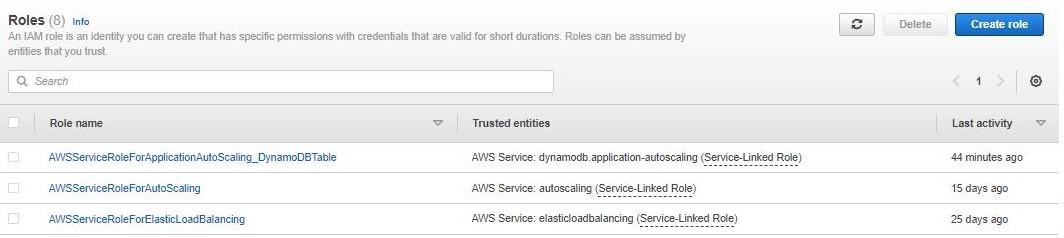
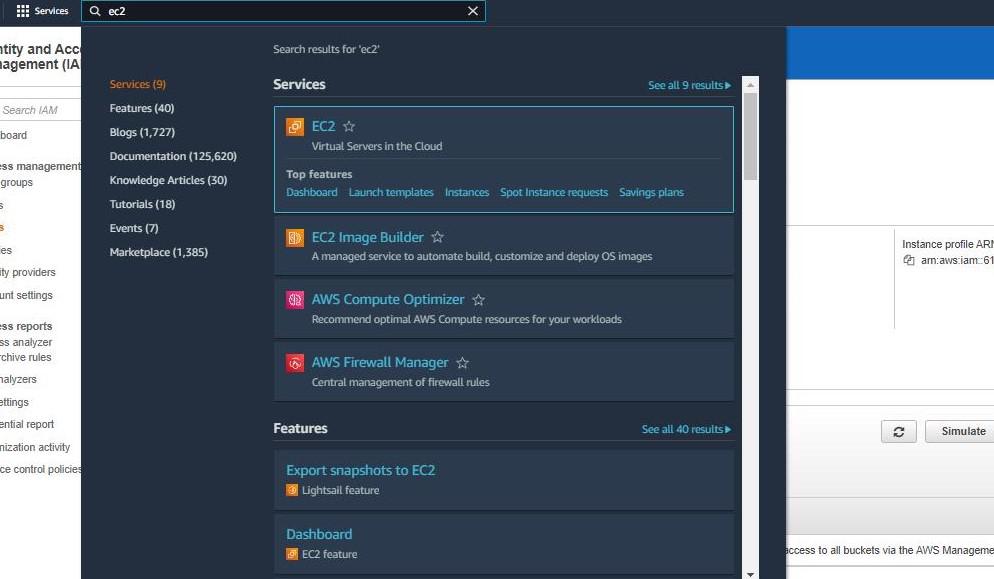
Step 1: First, login into your AWS account and click on “services” present on the left of the AWS management console, i.e. the primary screen. And from the drop-down menu of options, tap on “EC2”. Here is the image attached to refer to.

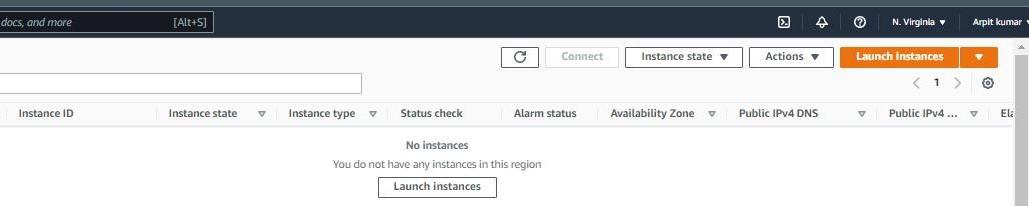
Under Resources >> Click on “Instances running” — It will show if any EC2 instances are running or not.
Click on launch instance
Click on launch instance, after clicking on it you will be redirected to a launch page where we can create instance.
Create a name for the instance.
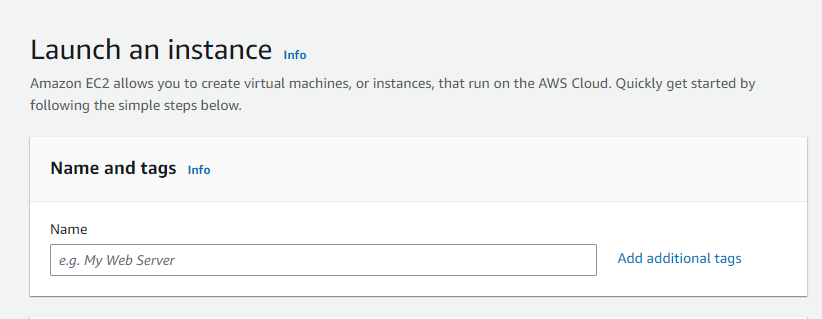
Naming instance
Name the instance.
Select AMI – Required operating system from the available.
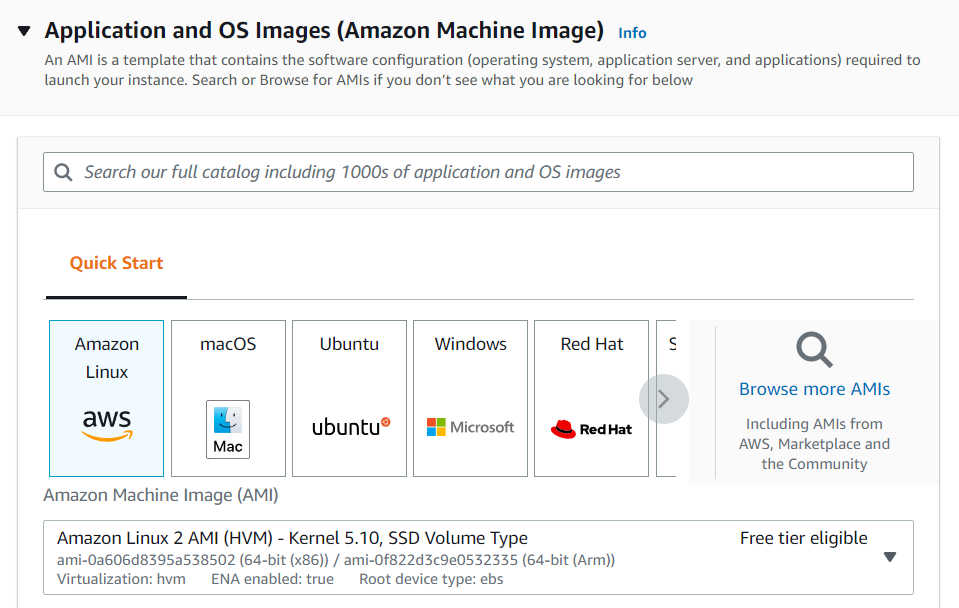
Selecting AMI
Amazon Machine Image
I am selecting windows AMI as we need to create windows instance.
By default, it selects a free tier storage.(IF YOU ARE ELIGIBLE FOR FREE TIER)
From the available storage specifications, select a free tier eligible storage service.
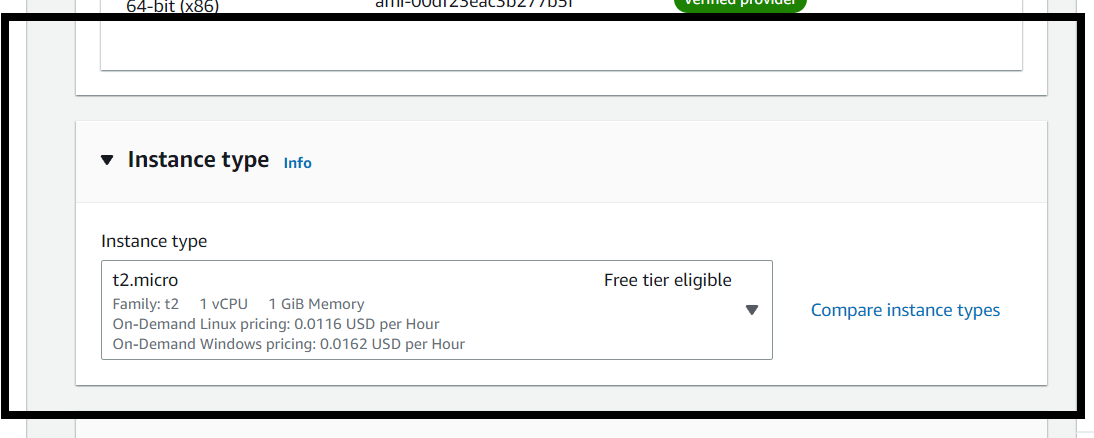
Select instance type
Select instance type
By default, instance type is “t2.micro” which is free tier eligible service.
Do not select any other which leads to billing amount.
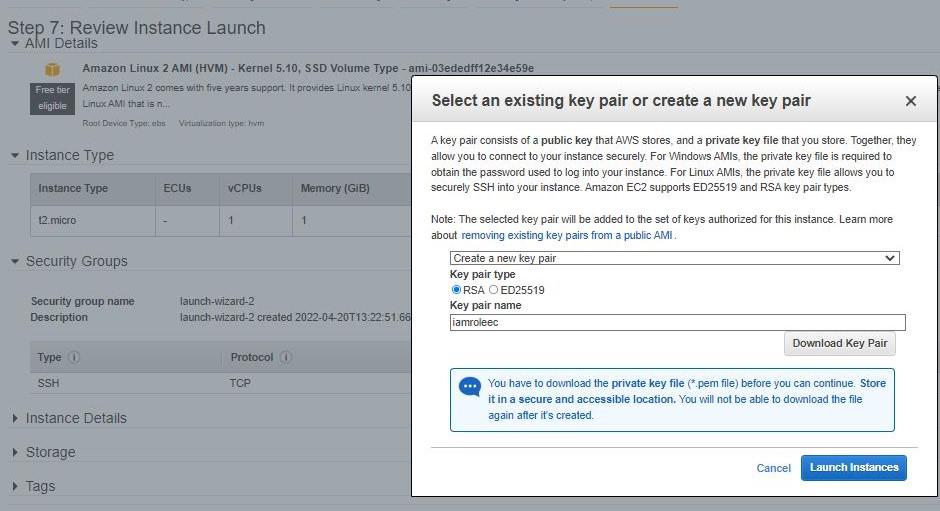
Now, create a key value pair, by clicking on “Create new key pair”. A window will pop for creating key-pair as shown below.
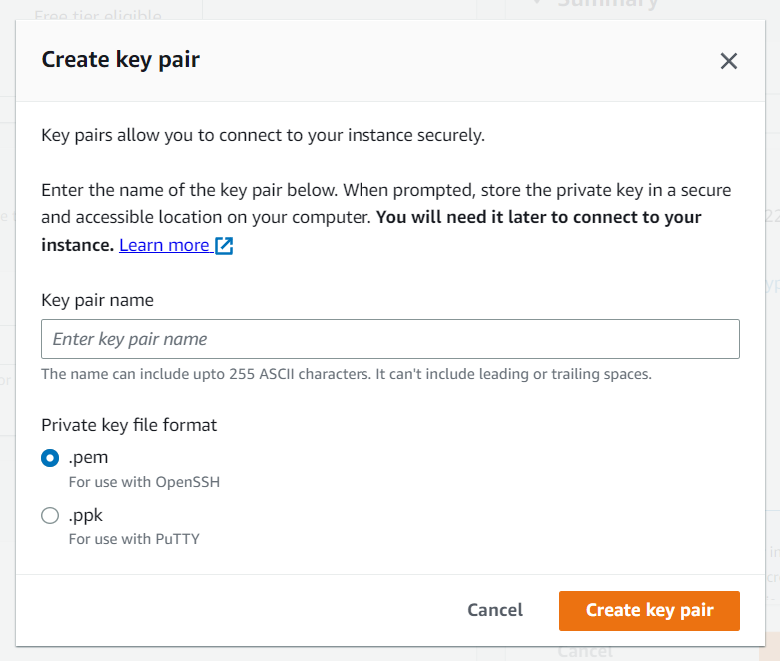
Creating key pair
Create Key-Pair
Enter name>>Select “.pem” and create. Automatically key-pair which was created will be downloaded.
Select the created key-pair.
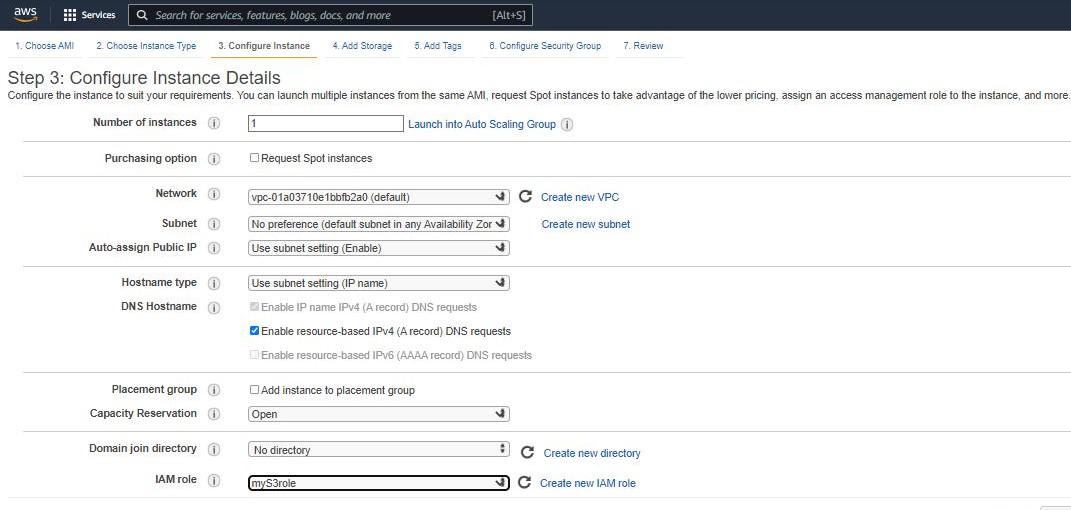
Keep the network settings as default settings and make changes if required.
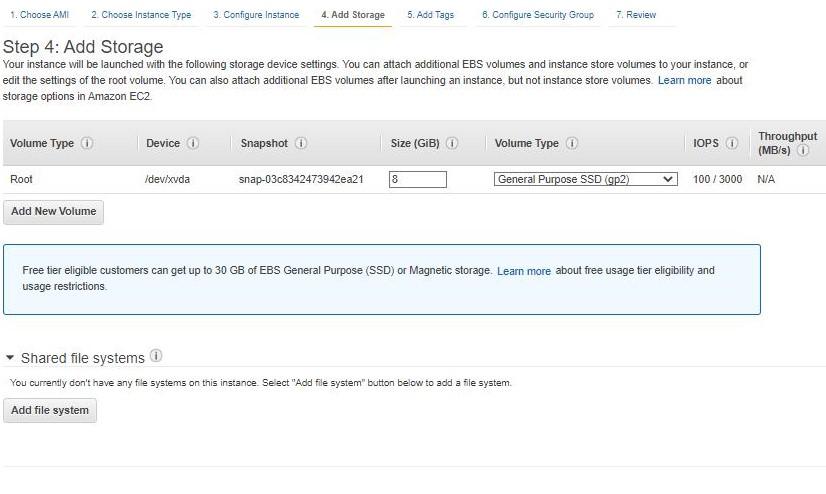
Storage
As mentioned in the picture, Free tier eligible can get up-to 30 GB of EBS Storage. Keep it as default.
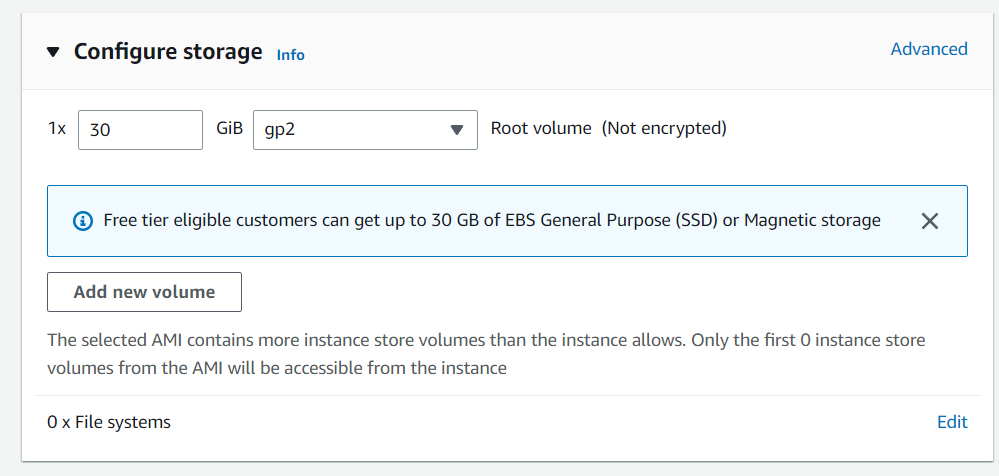
Configuring Storage
Launching Instance
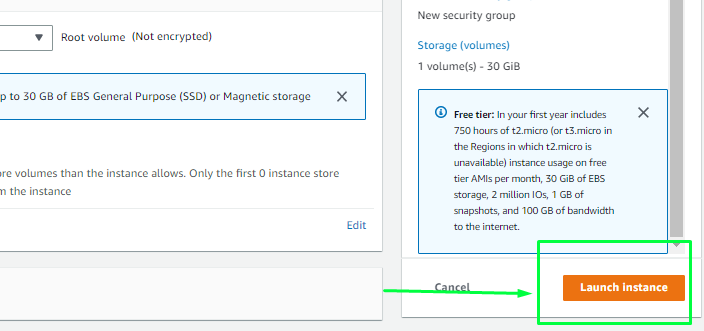
Launching instance
At last, Check if all the selected are eligible for free tier or not and click on “Launch instance”.
That’s it, an instance will be created.
EC2 Instance All State in AWS :-
The common EC2 instance states are Pending, Running, Stopping, Stopped, Terminated, Shutting Down and Reebooted. It is important to keep track of the state of your EC2 instances so that you can manage them properly. You can view the state of your instances in the EC2 Console, AWS CLI, or AWS SDKs.
In AWS, EC2 (Elastic Compute Cloud) instances can have different states, which indicate what operations can be performed on them. Here are some of the common EC2 instance states:
1. Pending: When you launch an EC2 instance, it enters the pending state. This means that AWS is in the process of creating the instance and initializing all of the necessary components, such as the virtual machine and the associated networking resources. During this time, you won’t be able to access the instance, as it is not yet ready to be used.
2. Running: Once an EC2 instance has finished initializing, it enters the running state. This means that the instance is up and running and is ready to be used. In this state, you can log in to the instance and start using it to run your applications and services.
3. Stopping: If you manually stop an EC2 instance, or if it is part of an auto-scaling group and is being terminated, it enters the stopping state. During this state, AWS prepares the instance for shutdown by stopping any processes or applications running on the instance and disconnecting it from the network. However, the instance’s configuration and data are preserved, so you can start the instance again later if you need to.
4. Stopped: Once an EC2 instance has been stopped, it enters the stopped state. In this state, the instance is not running and is not available for use. However, the instance’s configuration and data are preserved, so you can start the instance again later if you need to. You might stop an instance if you don’t need it for a period of time but don’t want to terminate it entirely.
5. Terminated: If you manually terminate an EC2 instance, or if it is part of an auto-scaling group and is being terminated, it enters the terminated state. In this state, the instance is permanently deleted, and all of its configuration and data are lost. You might terminate an instance if you no longer need it, or if you want to replace it with a new instance.
6. Shutting-down: If AWS is retiring an instance, it goes into the “Shutting-down” state for a brief period before the instance is terminated. During this time, the instance is no longer available for use, and the data and configuration are preserved. This state is similar to the stopping state, but with an added step of preparing the instance for retirement.
7. Rebooting: If you choose to reboot an EC2 instance, it enters the rebooting state. During this state, the instance’s operating system is shut down and then restarted, but the instance’s configuration and data are preserved. You might reboot an instance if you need to apply updates or make changes to the instance’s configuration.
You can view the state of your EC2 instances in the EC2 Console, AWS CLI, or AWS SDKs. It is important to keep track of the state of your instances so that you can manage them properly, such as starting, stopping, or terminating instances as needed. When you use Amazon Web Services (AWS) to run virtual servers, or instances, these instances can be in different states depending on what’s happening with them. For example, an instance might be “running” when it’s up and running properly, or “stopped” when it’s not currently being used.
AWS CloudWatch to monitor your EC2 instances and their associated resources in real-time. CloudWatch provides a wealth of data on your instances, including CPU usage, disk activity, and network traffic, which can help you identify performance issues and other problems before they have a chance to impact your users.
Another important aspect of managing EC2 instances is understanding the various instance types available in AWS. Different instance types have different performance characteristics and are optimized for different types of workloads. For example, some instances are optimized for CPU-intensive workloads, while others are better suited for memory-intensive applications. By choosing the right instance type for your workload, you can ensure that your applications are running efficiently and cost-effectively.
Overall, understanding the different states of EC2 instances in AWS is just one aspect of effectively managing your infrastructure in the cloud. By taking advantage of tools like AWS CloudWatch, choosing the right instance types for your workloads, and following best practices for security and maintenance, you can ensure that your applications and services are always available to your users, and that you’re getting the most out of your investment in the cloud.