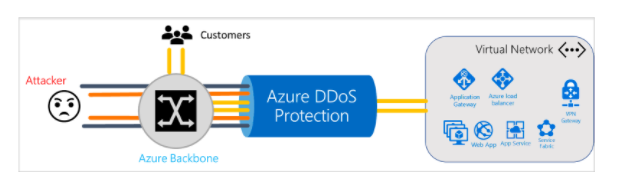
- Allows you to protect your Azure resources from denial of service (DoS) attacks.
- DDoS protection (layers 3 and 4) offers two service tiers: Basic and Standard.
Features
- Basic
- Enabled by default (free).
- It mitigates common network attacks.
- Both basic and standard protects IPv4 and IPv6 public IP addresses.
- Standard
- It has advanced capabilities to protect you against network attacks such as logging, alerting, and telemetry.
- Mitigates the following attacks:
- Volumetric attacks – flood the network layer with attacks.
- Protocol attacks – exploit a weakness in layers 3 and 4.
- Resource layer attacks – a layer 7 attack that disrupts the transmission of data between hosts.
- Enables you to configure alerts at the start and stop of an attack.
- The metric data is retained for 30 days.
- Provides autotuned mitigation policies (TCP/TCP SYN/UDP) for each public IP.
Feature | Basic | Standard |
Active traffic monitoring & always-on detection | Yes | Yes |
Automatic attack mitigations | Yes | Yes |
Availability guarantee | Azure Region | Application |
Mitigation policies | Tuned for Azure traffic region volume | Tuned for application traffic volume |
Metrics & alerts | No | Real-time attack metrics and resource logs via Azure Monitor |
Mitigation reports | No | Post attack mitigation reports |
Mitigation flow logs | No | NRT log stream for SIEM integration |
Mitigation policy customization | No | Engage DDoS Experts |