- PaaS relational database services
- Mitigate database downtime with high availability, redundancy, and resiliency capabilities.
- Enables you to scale vertically when needed.
- Receive alerts based on the metrics of your servers.
- Protect sensitive data at rest and in transit.
- Automated backups, up to 35 days.
- PostgreSQL deployment options: Single Server and Hyperscale (Citus)
- Single server pricing tiers: Basic, General Purpose, and Memory Optimized.
- Basic – light compute and I/O performance workloads.
- General Purpose – a balanced compute and memory with scalable I/O throughput workloads.
- Memory Optimized – for high performance database workloads requiring in-memory performance.
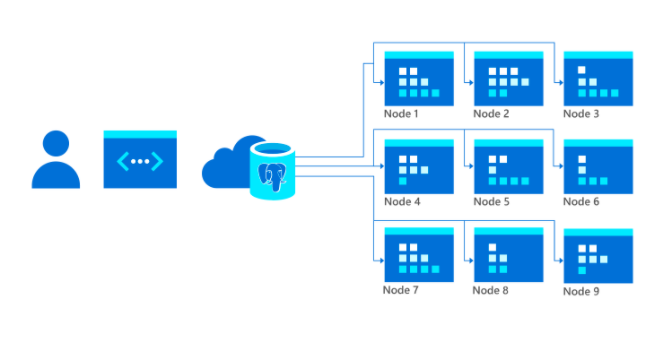
PostgreSQL – Hyperscale (Citus)
- Sharding – scales horizontally across multiple machines.
- Supports query parallelization for faster responses on large datasets.
- Primarily used for multi-tenant applications, real-time operational analytics, and high throughput transactional workloads.