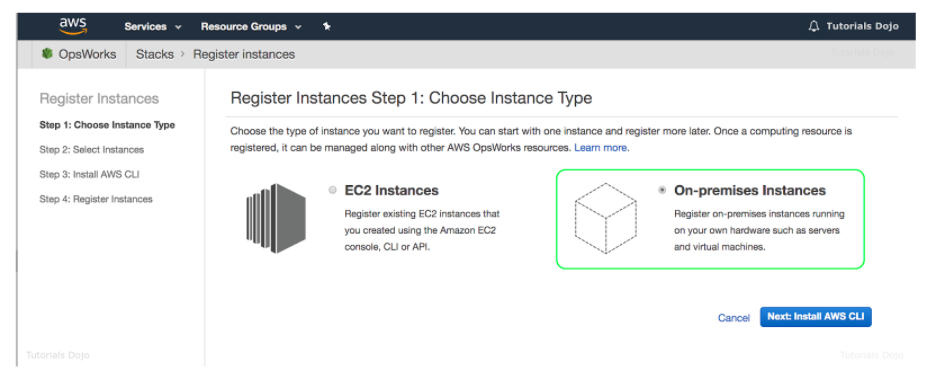
- Allows you to create, manage, and distribute catalogs of approved products to end-users, who can then access the products they need in a personalized portal.
- Administrators can control which users have access to each product to enforce compliance with organizational business policies. Administrators can also set up adopted roles so that end users only require IAM access to AWS Service Catalog in order to deploy approved resources.
- This is a regional service.
- Standardization of assets
- Self-service discovery and launch
- Fine-grain access control
- Extensibility and version control
- Users
- Catalog administrators – Manage a catalog of products, organizing them into portfolios and granting access to end users. Catalog administrators prepare AWS CloudFormation templates, configure constraints, and manage IAM roles that are assigned to products to provide for advanced resource management.
- End users – Use AWS Service Catalog to launch products to which they have been granted access.
- Products
- Can comprise one or more AWS resources, such as EC2 instances, storage volumes, databases, monitoring configurations, and networking components, or packaged AWS Marketplace products.
- You create your products by importing AWS CloudFormation templates. The templates define the AWS resources required for the product, the relationships between resources, and the parameters for launching the product to configure security groups, create key pairs, and perform other customizations.
- You can see the products that you are using and their health state in the AWS Service Catalog console.
- Portfolio
- A collection of products, together with configuration information. Portfolios help manage product configuration, determine who can use specific products and how they can use them.
- When you add a new version of a product to a portfolio, that version is automatically available to all current users of that portfolio.
- You can also share your portfolios with other AWS accounts and allow the administrator of those accounts to distribute your portfolios with additional constraints.
- When you add tags to your portfolio, the tags are applied to all instances of resources provisioned from products in the portfolio.
- Versioning
- Service Catalog allows you to manage multiple versions of the products in your catalog.
- A version can have one of three statuses:
- Active – An active version appears in the version list and allows users to launch it.
- Inactive – An inactive version is hidden from the version list. Existing provisioned products launched from this version will not be affected.
- Deleted – If a version is deleted, it is removed from the version list. Deleting a version can’t be undone.
- Access control
- You apply AWS IAM permissions to control who can view and modify your products and portfolios.
- By assigning an IAM role to each product, you can avoid giving users permissions to perform unapproved operations, and enable them to provision resources using the catalog.
- Constraints
- You use constraints to apply limits to products for governance or cost control.
- Types of constraints:
- Template constraints restrict the configuration parameters that are available for the user when launching the product. Template constraints allow you to reuse generic AWS CloudFormation templates for products and apply restrictions to the templates on a per-product or per-portfolio basis.
- Launch constraints allow you to specify a role for a product in a portfolio. This role is used to provision the resources at launch, so you can restrict user permissions without impacting users’ ability to provision products from the catalog.
- Notification constraints specify an Amazon SNS topic to receive notifications about stack events.
- Tag update constraints allow administrators to allow or disallow end users to update tags on resources associated with an AWS Service Catalog provisioned product.
- Stack
- Every AWS Service Catalog product is launched as an AWS CloudFormation stack.
- You can use CloudFormation StackSets to launch Service Catalog products across multiple regions and accounts. You can specify the order in which products deploy sequentially within regions. Across accounts, products are deployed in parallel.
- Service Catalog uses Amazon S3 buckets and Amazon DynamoDB databases that are encrypted at rest using Amazon-managed keys.
- Service Catalog uses TLS and client-side encryption of information in transit between the caller and AWS.
- Service Catalog integrates with AWS CloudTrail and Amazon SNS.
- The AWS Service Catalog free tier includes 1,000 API calls per month.
- You are charged based on the number of API calls made to Service Catalog beyond the free tier.