Using Azure Active Directory (Azure AD), you can designate limited administrators to manage identity tasks in less-privileged roles. Administrators can be assigned for such purposes as adding or changing users, assigning administrative roles, resetting user passwords, managing user licenses, and managing domain names. The default user permissions can be changed only in user settings in Azure AD.
Limit the use of Global administrator
Users who are assigned to the Global administrator role can read and modify every administrative setting in your Azure AD organization. By default, the person who signs up for an Azure subscription is assigned the Global administrator role for the Azure AD organization. Only Global administrators and Privileged Role administrators can delegate administrator roles. To reduce the risk to your business, we recommend that you assign this role to the fewest possible people in your organization.
As a best practice, we recommend that you assign this role to fewer than 5 people in your organization. If you have over five users assigned to the Global Administrator role in your organization, here are some ways to reduce its use.
Find the role you need
If it's frustrating for you to find the role you need out of a list of many roles, Azure AD can show you subsets of the roles based on role categories. Check out our new Type filter for Azure AD Roles and administrators to show you only the roles in the selected type.
A role exists now that didn’t exist when you assigned the Global administrator role
It's possible that a role or roles were added to Azure AD that provide more granular permissions that were not an option when you elevated some users to Global administrator. Over time, we are rolling out additional roles that accomplish tasks that only the Global administrator role could do before. You can see these reflected in the following Available roles.
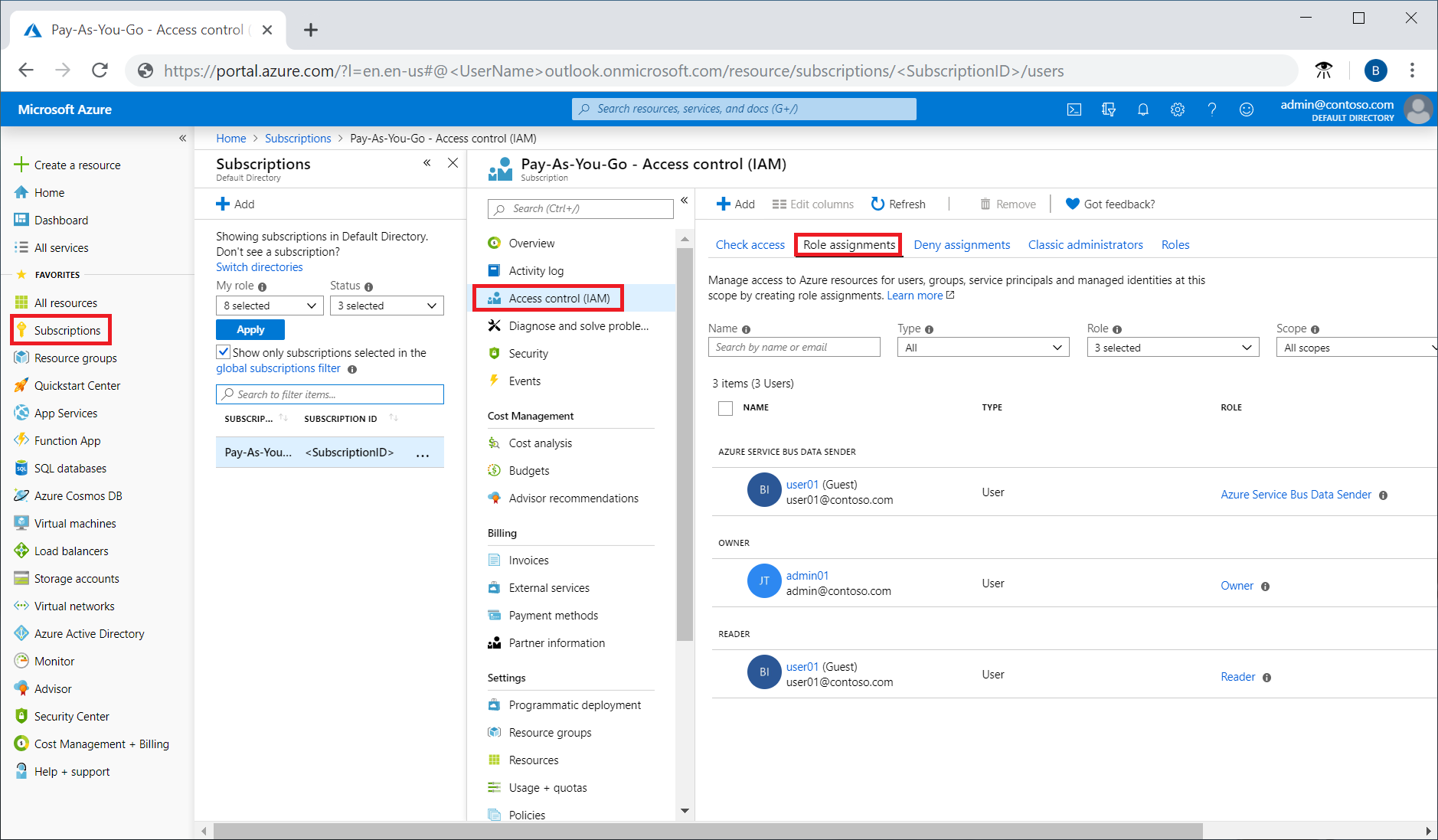
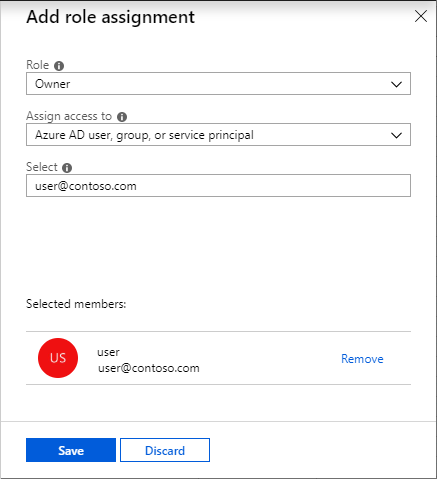
Assign or remove administrator roles
To learn how to assign administrative roles to a user in Azure Active Directory, see View and assign administrator roles in Azure Active Directory.
Available roles
The following administrator roles are available:
Application Administrator
Users in this role can create and manage all aspects of enterprise applications, application registrations, and application proxy settings. This role also grants the ability to consent to delegated permissions, and application permissions excluding Microsoft Graph and Azure AD Graph. Users assigned to this role are not added as owners when creating new application registrations or enterprise applications.
Important
This role grants the ability to manage application credentials. Users assigned this role can add credentials to an application, and use those credentials to impersonate the application’s identity. If the application’s identity has been granted access to Azure Active Directory, such as the ability to create or update User or other objects, then a user assigned to this role could perform those actions while impersonating the application. This ability to impersonate the application’s identity may be an elevation of privilege over what the user can do via their role assignments in Azure AD. It is important to understand that assigning a user to the Application Administrator role gives them the ability to impersonate an application’s identity.
Application Developer
Users in this role can create application registrations when the "Users can register applications" setting is set to No. This role also grants permission to consent on one's own behalf when the "Users can consent to apps accessing company data on their behalf" setting is set to No. Users assigned to this role are added as owners when creating new application registrations or enterprise applications.
Authentication Administrator
Users with this role can set or reset non-password credentials and can update passwords for all users. Authentication Administrators can require users to re-register against existing non-password credential (for example, MFA or FIDO) and revoke remember MFA on the device, which prompts for MFA on the next sign-in of users who are non-administrators or assigned the following roles only:
- Authentication Administrator
- Directory Readers
- Guest Inviter
- Message Center Reader
- Reports Reader
The Authentication administrator role is currently in public preview. This preview version is provided without a service level agreement, and it's not recommended for production workloads. Certain features might not be supported or might have constrained capabilities. For more information, see Supplemental Terms of Use for Microsoft Azure Previews.
Important
Users with this role can change credentials for people who may have access to sensitive or private information or critical configuration inside and outside of Azure Active Directory. Changing the credentials of a user may mean the ability to assume that user's identity and permissions. For example:
- Application Registration and Enterprise Application owners, who can manage credentials of apps they own. Those apps may have privileged permissions in Azure AD and elsewhere not granted to Authentication Administrators. Through this path an Authentication Administrator may be able to assume the identity of an application owner and then further assume the identity of a privileged application by updating the credentials for the application.
- Azure subscription owners, who may have access to sensitive or private information or critical configuration in Azure.
- Security Group and Office 365 Group owners, who can manage group membership. Those groups may grant access to sensitive or private information or critical configuration in Azure AD and elsewhere.
- Administrators in other services outside of Azure AD like Exchange Online, Office Security and Compliance Center, and human resources systems.
- Non-administrators like executives, legal counsel, and human resources employees who may have access to sensitive or private information.
Azure Information Protection Administrator
Users with this role have all permissions in the Azure Information Protection service. This role allows configuring labels for the Azure Information Protection policy, managing protection templates, and activating protection. This role does not grant any permissions in Identity Protection Center, Privileged Identity Management, Monitor Office 365 Service Health, or Office 365 Security & Compliance Center.
B2C User Flow Administrator
Users with this role can create and manage B2C User Flows (also called "built-in" policies) in the Azure portal. By creating or editing user flows, these users can change the html/CSS/javascript content of the user experience, change MFA requirements per user flow, change claims in the token and adjust session settings for all policies in the tenant. On the other hand, this role does not include the ability to review user data, or make changes to the attributes that are included in the tenant schema. Changes to Identity Experience Framework (also known as Custom) policies is also outside the scope of this role.
B2C User Flow Attribute Administrator
Users with this role add or delete custom attributes available to all user flows in the tenant. As such, users with this role can change or add new elements to the end user schema and impact the behavior of all user flows and indirectly result in changes to what data may be asked of end users and ultimately sent as claims to applications. This role cannot edit user flows.
B2C IEF Keyset Administrator
User can create and manage policy keys and secrets for token encryption, token signatures, and claim encryption/decryption. By adding new keys to existing key containers, this limited administrator can rollover secrets as needed without impacting existing applications. This user can see the full content of these secrets and their expiration dates even after their creation.
Important
This is a sensitive role. The keyset administrator role should be carefully audited and assigned with care during pre-production and production.
B2C IEF Policy Administrator
Users in this role have the ability to create, read, update, and delete all custom policies in Azure AD B2C and therefore have full control over the Identity Experience Framework in the relevant Azure AD B2C tenant. By editing policies, this user can establish direct federation with external identity providers, change the directory schema, change all user-facing content (HTML, CSS, JavaScript), change the requirements to complete an authentication, create new users, send user data to external systems including full migrations, and edit all user information including sensitive fields like passwords and phone numbers. Conversely, this role cannot change the encryption keys or edit the secrets used for federation in the tenant.
Important
The B2 IEF Policy Administrator is a highly sensitive role which should be assigned on a very limited basis for tenants in production. Activities by these users should be closely audited, especially for tenants in production.
Billing Administrator
Makes purchases, manages subscriptions, manages support tickets, and monitors service health.
Cloud Application Administrator
Users in this role have the same permissions as the Application Administrator role, excluding the ability to manage application proxy. This role grants the ability to create and manage all aspects of enterprise applications and application registrations. This role also grants the ability to consent to delegated permissions, and application permissions excluding Microsoft Graph and Azure AD Graph. Users assigned to this role are not added as owners when creating new application registrations or enterprise applications.
Important
This role grants the ability to manage application credentials. Users assigned this role can add credentials to an application, and use those credentials to impersonate the application’s identity. If the application’s identity has been granted access to Azure Active Directory, such as the ability to create or update User or other objects, then a user assigned to this role could perform those actions while impersonating the application. This ability to impersonate the application’s identity may be an elevation of privilege over what the user can do via their role assignments in Azure AD. It is important to understand that assigning a user to the Cloud Application Administrator role gives them the ability to impersonate an application’s identity.
Cloud Device Administrator
Users in this role can enable, disable, and delete devices in Azure AD and read Windows 10 BitLocker keys (if present) in the Azure portal. The role does not grant permissions to manage any other properties on the device.
Compliance Administrator
Users with this role have permissions to manage compliance-related features in the Microsoft 365 compliance center, Microsoft 365 admin center, Azure, and Office 365 Security & Compliance Center. Assignees can also manage all features within the Exchange admin center and Teams & Skype for Business admin centers and create support tickets for Azure and Microsoft 365. More information is available at About Office 365 admin roles.
Compliance Data Administrator
Users with this role have permissions to track data in the Microsoft 365 compliance center, Microsoft 365 admin center, and Azure. Users can also track compliance data within the Exchange admin center, Compliance Manager, and Teams & Skype for Business admin center and create support tickets for Azure and Microsoft 365.
Conditional Access Administrator
Users with this role have the ability to manage Azure Active Directory Conditional Access settings.
Note
To deploy Exchange ActiveSync Conditional Access policy in Azure, the user must also be a Global Administrator.
Customer Lockbox access approver
Manages Customer Lockbox requests in your organization. They receive email notifications for Customer Lockbox requests and can approve and deny requests from the Microsoft 365 admin center. They can also turn the Customer Lockbox feature on or off. Only global admins can reset the passwords of people assigned to this role.
Desktop Analytics Administrator
Users in this role can manage the Desktop Analytics and Office Customization & Policy services. For Desktop Analytics, this includes the ability to view asset inventory, create deployment plans, view deployment and health status. For Office Customization & Policy service, this role enables users to manage Office policies.
Device Administrator
This role is available for assignment only as an additional local administrator in Device settings. Users with this role become local machine administrators on all Windows 10 devices that are joined to Azure Active Directory. They do not have the ability to manage devices objects in Azure Active Directory.
Directory Readers
This is a role that should be assigned only to legacy applications that do not support the Consent Framework. Don't assign it to users.
Directory Synchronization Accounts
Do not use. This role is automatically assigned to the Azure AD Connect service, and is not intended or supported for any other use.
Directory Writers
This is a legacy role that is to be assigned to applications that do not support the Consent Framework. It should not be assigned to any users.
Dynamics 365 administrator / CRM Administrator
Users with this role have global permissions within Microsoft Dynamics 365 Online, when the service is present, as well as the ability to manage support tickets and monitor service health. More information at Use the service admin role to manage your tenant.
Note
In Microsoft Graph API, Azure AD Graph API, and Azure AD PowerShell, this role is identified as "Dynamics 365 Service Administrator." It is "Dynamics 365 Administrator" in the Azure portal.
Exchange Administrator
Users with this role have global permissions within Microsoft Exchange Online, when the service is present. Also has the ability to create and manage all Office 365 Groups, manage support tickets, and monitor service health. More information at About Office 365 admin roles.
Note
In Microsoft Graph API, Azure AD Graph API, and Azure AD PowerShell, this role is identified as "Exchange Service Administrator." It is "Exchange Administrator" in the Azure portal. It is "Exchange Online administrator" in the Exchange admin center.
External Identity Provider Administrator
This administrator manages federation between Azure Active Directory tenants and external identity providers. With this role, users can add new identity providers and configure all available settings (e.g. authentication path, service ID, assigned key containers). This user can enable the tenant to trust authentications from external identity providers. The resulting impact on end user experiences depends on the type of tenant:
- Azure Active Directory tenants for employees and partners: The addition of a federation (e.g. with Gmail) will immediately impact all guest invitations not yet redeemed. See Adding Google as an identity provider for B2B guest users.
- Azure Active Directory B2C tenants: The addition of a federation (for example, with Facebook, or with another Azure AD organization) does not immediately impact end user flows until the identity provider is added as an option in a user flow (also called a built-in policy). See Configuring a Microsoft account as an identity provider for an example. To change user flows, the limited role of "B2C User Flow Administrator" is required.
Global Administrator / Company Administrator
Users with this role have access to all administrative features in Azure Active Directory, as well as services that use Azure Active Directory identities like Microsoft 365 security center, Microsoft 365 compliance center, Exchange Online, SharePoint Online, and Skype for Business Online. The person who signs up for the Azure Active Directory tenant becomes a global administrator. Only global administrators can assign other administrator roles. There can be more than one global administrator at your company. Global admins can reset the password for any user and all other administrators.
Note
In Microsoft Graph API, Azure AD Graph API, and Azure AD PowerShell, this role is identified as "Company Administrator". It is "Global Administrator" in the Azure portal.
Guest Inviter
Users in this role can manage Azure Active Directory B2B guest user invitations when the Members can invite user setting is set to No. More information about B2B collaboration at About Azure AD B2B collaboration. It does not include any other permissions.
Helpdesk Administrator
Users with this role can change passwords, invalidate refresh tokens, manage service requests, and monitor service health. Invalidating a refresh token forces the user to sign in again. Helpdesk administrators can reset passwords and invalidate refresh tokens of other users who are non-administrators or assigned the following roles only:
- Directory Readers
- Guest Inviter
- Helpdesk Administrator
- Message Center Reader
- Reports Reader
Important
Users with this role can change passwords for people who may have access to sensitive or private information or critical configuration inside and outside of Azure Active Directory. Changing the password of a user may mean the ability to assume that user's identity and permissions. For example:
- Application Registration and Enterprise Application owners, who can manage credentials of apps they own. Those apps may have privileged permissions in Azure AD and elsewhere not granted to Helpdesk Administrators. Through this path a Helpdesk Administrator may be able to assume the identity of an application owner and then further assume the identity of a privileged application by updating the credentials for the application.
- Azure subscription owners, who may have access to sensitive or private information or critical configuration in Azure.
- Security Group and Office 365 Group owners, who can manage group membership. Those groups may grant access to sensitive or private information or critical configuration in Azure AD and elsewhere.
- Administrators in other services outside of Azure AD like Exchange Online, Office Security and Compliance Center, and human resources systems.
- Non-administrators like executives, legal counsel, and human resources employees who may have access to sensitive or private information.
Note
Delegating administrative permissions over subsets of users and applying policies to a subset of users is possible with Administrative Units (preview).
This role was previously called "Password Administrator" in the Azure portal. We have changed its name to "Helpdesk Administrator" to match its name in Azure AD PowerShell, Azure AD Graph API and Microsoft Graph API.
Intune Administrator
Users with this role have global permissions within Microsoft Intune Online, when the service is present. Additionally, this role contains the ability to manage users and devices in order to associate policy, as well as create and manage groups. More information at Role-based administration control (RBAC) with Microsoft Intune
Note
In Microsoft Graph API, Azure AD Graph API, and Azure AD PowerShell, this role is identified as "Intune Service Administrator ". It is "Intune Administrator" in the Azure portal.
Kaizala Administrator
Users with this role have global permissions to manage settings within Microsoft Kaizala, when the service is present, as well as the ability to manage support tickets and monitor service health. Additionally, the user can access reports related to adoption & usage of Kaizala by Organization members and business reports generated using the Kaizala actions.
License Administrator
Users in this role can add, remove, and update license assignments on users, groups (using group-based licensing), and manage the usage location on users. The role does not grant the ability to purchase or manage subscriptions, create or manage groups, or create or manage users beyond the usage location. This role has no access to view, create, or manage support tickets.
Message Center Privacy Reader
Users in this role can monitor all notifications in the Message Center, including data privacy messages. Message Center Privacy Readers get email notifications including those related to data privacy and they can unsubscribe using Message Center Preferences. Only the Global Administrator and the Message Center Privacy Reader can read data privacy messages. Additionally, this role contains the ability to view groups, domains, and subscriptions. This role has no permission to view, create, or manage service requests.
Message Center Reader
Users in this role can monitor notifications and advisory health updates in Office 365 Message center for their organization on configured services such as Exchange, Intune, and Microsoft Teams. Message Center Readers receive weekly email digests of posts, updates, and can share message center posts in Office 365. In Azure AD, users assigned to this role will only have read-only access on Azure AD services such as users and groups. This role has no access to view, create, or manage support tickets.
Partner Tier1 Support
Do not use. This role has been deprecated and will be removed from Azure AD in the future. This role is intended for use by a small number of Microsoft resale partners, and is not intended for general use.
Partner Tier2 Support
Do not use. This role has been deprecated and will be removed from Azure AD in the future. This role is intended for use by a small number of Microsoft resale partners, and is not intended for general use.
Password Administrator
Users with this role have limited ability to manage passwords. This role does not grant the ability to manage service requests or monitor service health. Password administrators can reset passwords of other users who are non-administrators or members of the following roles only:
- Directory Readers
- Guest Inviter
- Password Administrator
Power BI Administrator
Users with this role have global permissions within Microsoft Power BI, when the service is present, as well as the ability to manage support tickets and monitor service health. More information at Understanding the Power BI admin role.
Note
In Microsoft Graph API, Azure AD Graph API, and Azure AD PowerShell, this role is identified as "Power BI Service Administrator ". It is "Power BI Administrator" in the Azure portal.
Privileged Authentication Administrator
Users with this role can set or reset non-password credentials for all users, including global administrators, and can update passwords for all users. Privileged Authentication Administrators can force users to re-register against existing non-password credential (e.g. MFA, FIDO) and revoke ‘remember MFA on the device’, prompting for MFA on the next login of all users.
Privileged Role Administrator
Users with this role can manage role assignments in Azure Active Directory, as well as within Azure AD Privileged Identity Management. In addition, this role allows management of all aspects of Privileged Identity Management and administrative units.
Important
This role grants the ability to manage assignments for all Azure AD roles including the Global Administrator role. This role does not include any other privileged abilities in Azure AD like creating or updating users. However, users assigned to this role can grant themselves or others additional privilege by assigning additional roles.
Reports Reader
Users with this role can view usage reporting data and the reports dashboard in Microsoft 365 admin center and the adoption context pack in Power BI. Additionally, the role provides access to sign-in reports and activity in Azure AD and data returned by the Microsoft Graph reporting API. A user assigned to the Reports Reader role can access only relevant usage and adoption metrics. They don't have any admin permissions to configure settings or access the product-specific admin centers like Exchange. This role has no access to view, create, or manage support tickets.
Search Administrator
Users in this role have full access to all Microsoft Search management features in the Microsoft 365 admin center. Search Administrators can delegate the Search Administrators and Search Editor roles to users, and create and manage content, like bookmarks, Q&As, and locations. Additionally, these users can view the message center, monitor service health, and create service requests.
Search Editor
Users in this role can create, manage, and delete content for Microsoft Search in the Microsoft 365 admin center, including bookmarks, Q&As, and locations.
Security Administrator
Users with this role have permissions to manage security-related features in the Microsoft 365 security center, Azure Active Directory Identity Protection, Azure Information Protection, and Office 365 Security & Compliance Center. More information about Office 365 permissions is available at Permissions in the Office 365 Security & Compliance Center.
Security operator
Users with this role can manage alerts and have global read-only access on security-related feature, including all information in Microsoft 365 security center, Azure Active Directory, Identity Protection, Privileged Identity Management and Office 365 Security & Compliance Center. More information about Office 365 permissions is available at Permissions in the Office 365 Security & Compliance Center.
Security Reader
Users with this role have global read-only access on security-related feature, including all information in Microsoft 365 security center, Azure Active Directory, Identity Protection, Privileged Identity Management, as well as the ability to read Azure Active Directory sign-in reports and audit logs, and in Office 365 Security & Compliance Center. More information about Office 365 permissions is available at Permissions in the Office 365 Security & Compliance Center.
Service Support Administrator
Users with this role can open support requests with Microsoft for Azure and Office 365 services, and views the service dashboard and message center in the Azure portal and Microsoft 365 admin center. More information at About admin roles.
Note
In Microsoft Graph API, Azure AD Graph API, and Azure AD PowerShell, this role is identified as "Service Support Administrator." It is "Service Administrator" in the Azure portal, the Microsoft 365 admin center, and the Intune portal.
SharePoint Administrator
Users with this role have global permissions within Microsoft SharePoint Online, when the service is present, as well as the ability to create and manage all Office 365 Groups, manage support tickets, and monitor service health. More information at About admin roles.
Note
In Microsoft Graph API, Azure AD Graph API, and Azure AD PowerShell, this role is identified as "SharePoint Service Administrator." It is "SharePoint Administrator" in the Azure portal.
Skype for Business / Lync Administrator
Users with this role have global permissions within Microsoft Skype for Business, when the service is present, as well as manage Skype-specific user attributes in Azure Active Directory. Additionally, this role grants the ability to manage support tickets and monitor service health, and to access the Teams and Skype for Business Admin Center. The account must also be licensed for Teams or it can't run Teams PowerShell cmdlets. More information at About the Skype for Business admin role and Teams licensing information at Skype for Business and Microsoft Teams add-on licensing
Note
In Microsoft Graph API, Azure AD Graph API, and Azure AD PowerShell, this role is identified as "Lync Service Administrator." It is "Skype for Business Administrator" in the Azure portal.
Teams Administrator
Users in this role can manage all aspects of the Microsoft Teams workload via the Microsoft Teams & Skype for Business admin center and the respective PowerShell modules. This includes, among other areas, all management tools related to telephony, messaging, meetings, and the teams themselves. This role additionally grants the ability to create and manage all Office 365 Groups, manage support tickets, and monitor service health.
Note
In Microsoft Graph API, Azure AD Graph API, and Azure AD PowerShell, this role is identified as "Teams Service Administrator ". It is "Teams Administrator" in the Azure portal.
Teams Communications Administrator
Users in this role can manage aspects of the Microsoft Teams workload related to voice & telephony. This includes the management tools for telephone number assignment, voice and meeting policies, and full access to the call analytics toolset.
Teams Communications Support Engineer
Users in this role can troubleshoot communication issues within Microsoft Teams & Skype for Business using the user call troubleshooting tools in the Microsoft Teams & Skype for Business admin center. Users in this role can view full call record information for all participants involved. This role has no access to view, create, or manage support tickets.
Teams Communications Support Specialist
Users in this role can troubleshoot communication issues within Microsoft Teams & Skype for Business using the user call troubleshooting tools in the Microsoft Teams & Skype for Business admin center. Users in this role can only view user details in the call for the specific user they have looked up. This role has no access to view, create, or manage support tickets.
User Administrator
Users with this role can create users, and manage all aspects of users with some restrictions (see below), and can update password expiration policies. Additionally, users with this role can create and manage all groups. This role also includes the ability to create and manage user views, manage support tickets, and monitor service health.
Important
Users with this role can change passwords for people who may have access to sensitive or private information or critical configuration inside and outside of Azure Active Directory. Changing the password of a user may mean the ability to assume that user's identity and permissions. For example:
- Application Registration and Enterprise Application owners, who can manage credentials of apps they own. Those apps may have privileged permissions in Azure AD and elsewhere not granted to User Administrators. Through this path a User Administrator may be able to assume the identity of an application owner and then further assume the identity of a privileged application by updating the credentials for the application.
- Azure subscription owners, who may have access to sensitive or private information or critical configuration in Azure.
- Security Group and Office 365 Group owners, who can manage group membership. Those groups may grant access to sensitive or private information or critical configuration in Azure AD and elsewhere.
- Administrators in other services outside of Azure AD like Exchange Online, Office Security and Compliance Center, and human resources systems.
- Non-administrators like executives, legal counsel, and human resources employees who may have access to sensitive or private information.
Role Permissions
The following tables describe the specific permissions in Azure Active Directory given to each role. Some roles may have additional permissions in Microsoft services outside of Azure Active Directory.
Application Administrator permissions
Can create and manage all aspects of app registrations and enterprise apps.
Application Developer permissions
Can create application registrations independent of the ‘Users can register applications’ setting.
Authentication Administrator permissions
Allowed to view, set and reset authentication method information for any non-admin user.
Azure Information Protection Administrator permissions
Can manage all aspects of the Azure Information Protection service.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
B2C User Flow Administrator permissions
Create and manage all aspects of user flows.
B2C User Flow Attribute Administrator permissions
Create and manage the attribute schema available to all user flows.
B2C IEF Keyset Administrator permissions
Manage secrets for federation and encryption in the Identity Experience Framework.
B2C IEF Policy Administrator permissions
Create and manage trust framework policies in the Identity Experience Framework.
Billing Administrator permissions
Can perform common billing related tasks like updating payment information.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Cloud Application Administrator permissions
Can create and manage all aspects of app registrations and enterprise apps except App Proxy.
Cloud Device Administrator permissions
Full access to manage devices in Azure AD.
Company Administrator permissions
Can manage all aspects of Azure AD and Microsoft services that use Azure AD identities.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Compliance Administrator permissions
Can read and manage compliance configuration and reports in Azure AD and Office 365.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Compliance Data Administrator permissions
Creates and manages compliance content.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Conditional Access Administrator permissions
Can manage Conditional Access capabilities.
CRM Service Administrator permissions
Can manage all aspects of the Dynamics 365 product.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Customer LockBox Access Approver permissions
Can approve Microsoft support requests to access customer organizational data.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Desktop Analytics Administrator permissions
Can manage the Desktop Analytics and Office Customization & Policy services. For Desktop Analytics, this includes the ability to view asset inventory, create deployment plans, view deployment and health status. For Office Customization & Policy service, this role enables users to manage Office policies.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Device Administrators permissions
Users assigned to this role are added to the local administrators group on Azure AD-joined devices.
Directory Readers permissions
Can read basic directory information. For granting access to applications, not intended for users.
Directory Synchronization Accounts permissions
Only used by Azure AD Connect service.
Directory Writers permissions
Can read & write basic directory information. For granting access to applications, not intended for users.
Exchange Service Administrator permissions
Can manage all aspects of the Exchange product.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
External Identity Provider Administrator permissions
Configure identity providers for use in direct federation.
Guest Inviter permissions
Can invite guest users independent of the ‘members can invite guests’ setting.
Helpdesk Administrator permissions
Can reset passwords for non-administrators and Helpdesk Administrators.
Intune Service Administrator permissions
Can manage all aspects of the Intune product.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Kaizala Administrator permissions
Can manage settings for Microsoft Kaizala.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
License Administrator permissions
Can manage product licenses on users and groups.
Lync Service Administrator permissions
Can manage all aspects of the Skype for Business product.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Message Center Privacy Reader permissions
Can read Message Center posts, data privacy messages, groups, domains and subscriptions.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Message Center Reader permissions
Can read messages and updates for their organization in Office 365 Message Center only.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Partner Tier1 Support permissions
Do not use - not intended for general use.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Partner Tier2 Support permissions
Do not use - not intended for general use.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Password Administrator permissions
Can reset passwords for non-administrators and Password administrators.
Power BI Service Administrator permissions
Can manage all aspects of the Power BI product.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Privileged Authentication Administrator permissions
Allowed to view, set and reset authentication method information for any user (admin or non-admin).
Privileged Role Administrator permissions
Can manage role assignments in Azure AD,and all aspects of Privileged Identity Management.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Reports Reader permissions
Can read sign-in and audit reports.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Search Administrator permissions
Can create and manage all aspects of Microsoft Search settings.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Search Editor permissions
Can create and manage the editorial content such as bookmarks, Q and As, locations, floorplan.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Security Administrator permissions
Can read security information and reports,and manage configuration in Azure AD and Office 365.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Security Operator permissions
Creates and manages security events.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Security Reader permissions
Can read security information and reports in Azure AD and Office 365.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Service Support Administrator permissions
Can read service health information and manage support tickets.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
SharePoint Service Administrator permissions
Can manage all aspects of the SharePoint service.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Teams Communications Administrator permissions
Can manage calling and meetings features within the Microsoft Teams service.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Teams Communications Support Engineer permissions
Can troubleshoot communications issues within Teams using advanced tools.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Teams Communications Support Specialist permissions
Can troubleshoot communications issues within Teams using basic tools.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
Teams Service Administrator permissions
Can manage the Microsoft Teams service.
Note
This role has additional permissions outside of Azure Active Directory. For more information, see role description above.
User Administrator permissions
Can manage all aspects of users and groups, including resetting passwords for limited admins.
Role template IDs
Role template IDs are used mainly by Graph API or PowerShell users.
Deprecated roles
The following roles should not be used. They have been deprecated and will be removed from Azure AD in the future.
- AdHoc License Administrator
- Device Join
- Device Managers
- Device Users
- Email Verified User Creator
- Mailbox Administrator