| Create certificates. |
| [root@www ~]#
cd /etc/pki/tls/certs
[root@www certs]#
openssl req -x509 -nodes -newkey rsa:2048 -keyout vsftpd.pem -out vsftpd.pem -days 365
Generating a 2048 bit RSA private key ......++++++ .......++++++ writing new private key to '/etc/pki/tls/certs/vsftpd.pem' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. -----
Country Name (2 letter code) [AU]:
[root@www certs]#
JP
# country
State or Province Name (full name) [Some-State]:
Hiroshima
# State
Locality Name (eg, city) []:
Hiroshima
# city
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Server World
# company
Organizational Unit Name (eg, section) []:
IT Solution
# department
Common Name (eg, YOUR name) []:
www.srv.world
# server's FQDN
Email Address []:
xxx@srv.world
# admin's email
chmod 600 vsftpd.pem
|
| [2] | Configure Vsftpd. |
[root@www ~]#
vi /etc/vsftpd/vsftpd.conf
# add follows to the end
rsa_cert_file=/etc/pki/tls/certs/vsftpd.pem
ssl_enable=YES ssl_ciphers=HIGH ssl_tlsv1=YES ssl_sslv2=NO ssl_sslv3=NO force_local_data_ssl=YES force_local_logins_ssl=YES
/etc/rc.d/init.d/vsftpd restart
Shutting down vsftpd: [ OK ] Starting vsftpd for vsftpd: [ OK ] |
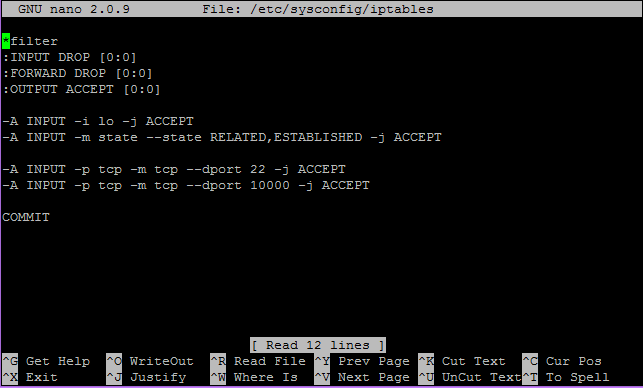
| [3] | If IPTables is running, allow FTP port and fixed PASV ports. For "-I INPUT 5" section below, Replace it to your own environment. |
[root@www ~]#
vi /etc/vsftpd/vsftpd.conf
# add to the end: fix PASV ports
pasv_enable=YES
pasv_min_port=21000 pasv_max_port=21010
/etc/rc.d/init.d/vsftpd restart
[root@www ~]#
iptables -I INPUT 5 -p tcp -m state --state NEW -m tcp --dport 21 -j ACCEPT
[root@www ~]#
iptables -I INPUT 5 -p tcp -m state --state NEW -m tcp --dport 21000:21010 -j ACCEPT
|
FTP Client : CentOS
|
Configure FTP Client to use FTPS connection.
| |
| [4] | Install FTP Client and configure like follows. |
[redhat@dlp ~]$
vi ~/.lftprc
# create new
set ftp:ssl-auth TLS set ftp:ssl-force true set ftp:ssl-protect-list yes set ftp:ssl-protect-data yes set ftp:ssl-protect-fxp yes set ssl:verify-certificate no
lftp -u cent www.srv.world
Password: lftp cent@www.srv.world:~>
|